Bug Bounty Methodology, Otorecon
Bug Bounty Methodology, Otorecon
OTORECON
I am building a tool for my bug bounty methodology. I will explain the tool, but first I want to explain myself and my methodology. You can get to the tool by clicking on the title.
First of all, I’m not a bugbounter, I don’t actually have a title in cybersecurity. But I want to have one because I’m very interested in cybersecurity. So I decided to try to get a bugbounter title first and that is my goal for now. But doing bug bounty for a job looks hard. Anyway, we use a lot of different tools and different codes in bug bounty. So I just want to combine different tools together to create and control in just one tool. Then I create otorecon tool.
I want to do this because I believe it could be useful and good work for my portfolio.
I hope you like this article and the tool I created.
Let’s continue. Now I’m going to explain my bug bounty methodology to you, I don’t have any results yet and I don’t know if the methodology works or not, but I believe it does. The first thing I want to say is that this methodology doesn’t have a lot of detail because I created this methodology for the tool. So it’s more basic and probably has a lot of things missing, but that’s not important. I can improve this project with feedback. So I will wait for your feedback.
Otorecon Workflow
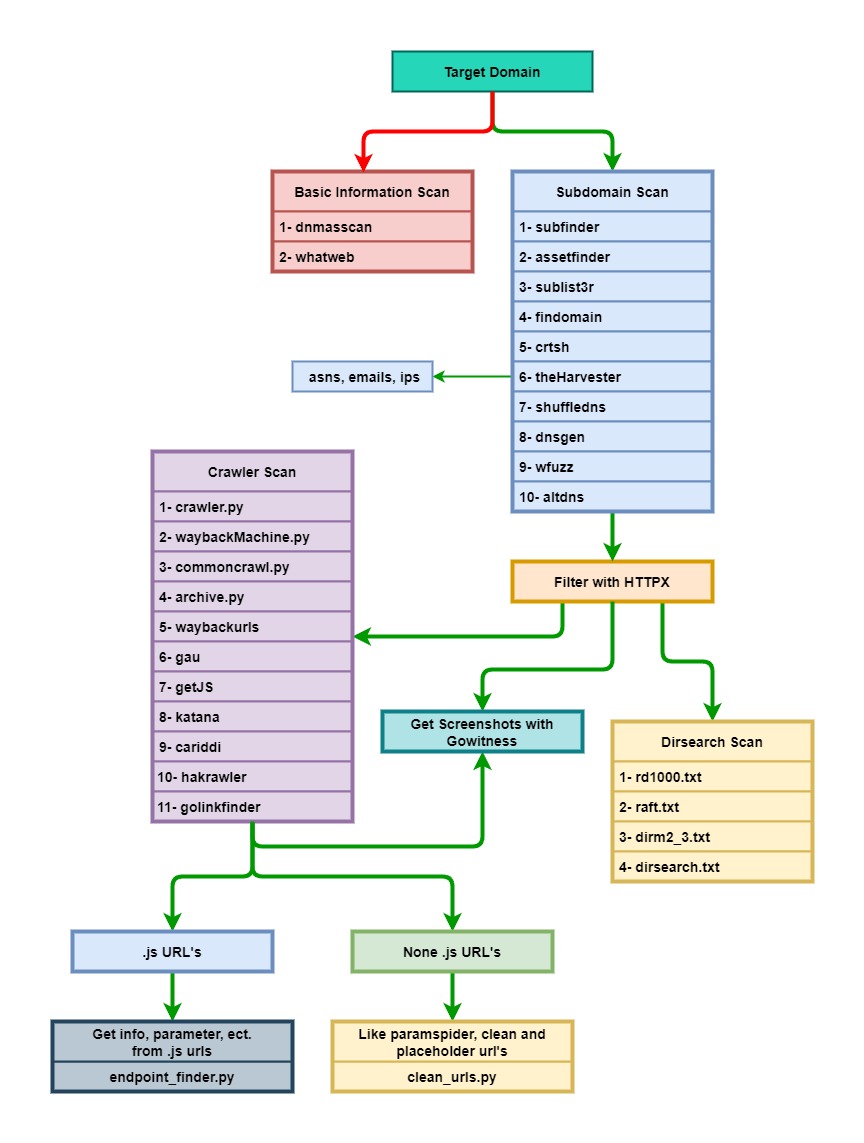
Basic Scan
Basic scan fuction include theese tools, dnmasscan and whatweb. This fuction purpose is getting basic information about target domain. You can run this command for basic scan.
$ python3 otorecon.py -bs all/tools -d example.com
First I use masscan for the find open ports. I chose masscan because it’s fastest than nmap.
$ python3 dnmasscan.py <domain_file> <out_file>
Then I use whatweb for getting a lot of information about target.
whatweb -v
Now we have bunch of information about target.Basic scan function save results as txt and html format.
Subdomain Scan
Subdomain scan include theese tools; subfinder, assetfinder, findomain, sublist3r, theHarvester, shuffledns, dnsgen, altdns, crtsh and wfuzz
I use a lot of tool and I use bunch of wordlists for scan. But I didn’t use some popular tools in otorecon because they are too slow. These tools are; amass, subbrute.py, subdominizer it’s a good tool but it’s too slow. But I will write all of them.
Beside that this function have out of scope option. Remember I create this tool for bugbounty. So you can write out of scope domains in a file and try -os parameter. It’s required option. And if you want you can choose a tool for scan or all for all tools.
You can run this command for subdomain scan
$ python3 otorecon.py -subs all/tools -d example.com
$ python3 otorecon.py -subs subfinder/all -d example.com -os out.txt
Hard Subdomain Scan Tools
Crtsh is a usefull website you can go visit here . And I write a code for getting crtsh results in terminal my code is in my github page you can download here
$ python3 crtsh.py -d example.com
theHarvester, have very usefull results. You can download here
$ theHarvester -d example.com -b anubis,crtsh,dnsdumpster,rapiddns,otx,urlscan,yahoo -f theHarvester_out'
submass, I call that submass because we use subbrute.py and massdns. You can download subbrute here and you can download massdns here.
$ python3 subbrute.py example.com names.txt | massdns -r resolvers.txt -o S -w results.txt'
dnsgen, This time we use dnsgen tool(download) and massdns. You can use domains file. I saw this code in one source which I don’t remember. I don’t know “dnsgen -“ mean. But I use in my function. You can downlad here
$ cat domain.file | dnsgen - | massdns -r resolvers.txt -t A -o J --flush 2>/dev/null -w result.txt'
wfuzz, I use all.txt t’s jason haddix’s wordlists. You can download here. Also I write a tool for subdomain bruteforcing you can downlad here
$ wfuzz -f result.txt -Z -w fierce.txt/all.txt -sc 200,202,204,301,302,403 example.com
altdns you can download tool here.
$ altdns -i domain.file -o result.txt -w words.txt'
Subdomainizer, you can download here this tool have usefull results like theHarvester.
$ subdomanizer -h
Shuffledns You can download here
$ shuffledns -d {domain_name} -w /names.txt -r resolvers.txt -silent'
Now we will get results. Subdomain Scan function save results as txt and html. Also this time theHarvester can result interesting information so I save them to.
Filtering
I use httpx tool for filtering but if you want you can use httprobe to.
$ python3 otorecon.py -fl subdomains.txt
httpx, you can download here
$ httpx -l <domainlist.txt> -p 443,8443,80,8080 -mc 200,202,204,301,307,403 -status-code -title
Crawling URL’s
I use a lot of tool for this scan. And I parse the results of the scan. Then I have two result file. One of them just include js files. First I take this file end scan with endpointer.py. Second I take other file and use clean_subs.py this like paramspider tool.
All tools;
- crawler.py
- waymac.py
- cocrawl.py
- archive.py
- waybackurls
- gau
- getJS
- katana
- cariddi
- hakrawler
- golinkFinder
$ python3 otorecon.py -cs all -cl subdomain_list.txt -cp
Get Screenshots
I use gowitness for this scan.
$ python3 otorecon.py -gcs domain_list.txt
Dirsearch Scan
I use gobuster for this scan. And I use 4 wordlists. Theese are;
- rd1000.txt
- raft.txt
- dirm2_3.txt
- dirsearch.txt
$ python3 otorecon.py -ds raft -dl subdomain_list.txt
Full Scan
Otorecon have full scan option. This option combine all scans each other.
$ python3 otorecon.py -fs example.com
