SQL Injection Guide
In this article, I intended to explain SQL injection in the most basic and most easily understandable way. Because the resources, I tried to learn were often too detailed for the beginner level and not very clear for the beginner level. So, I preferred a shorter and clearer explanation.
But it would not be right for me to give only the basic information in my article. I want you to understand the basics, and let the SQL injection fit your logic. So, there are many resources that I have shared in this article, check them out. There are many labs where you can practice your knowledge. I also shared a lot of cheat sheets as a helper.
I hope the article is useful to you. It helps you to learn SQL injection ![]()
Topics
-
Basic First
-
SQL Injection and Types
-
SQL Injection Labs
-
SQL Injection Sources
-
SQL Injection Cheat Sheats
Basic First
What is a Database?
A database is where all kinds of data and information are stored electronically.
What is Database Management System (DBMS)?
The database is usually controlled by a Database Management System (DBMS). Thanks to this system, data can be easily accessed, managed, changed, updated, and organized.
Most databases today use SQL.
What is SQL?
SQL is a programming language used in databases to query, manipulate and define data, as well as to provide access control.
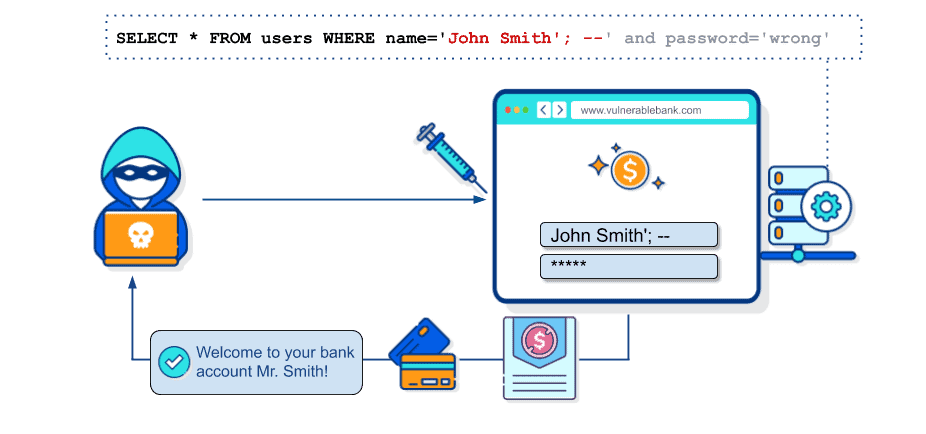
SQL Injection and Types
A web application sends SQL queries to use data found in the database. The attacker can inject their own queries into these SQL queries or manipulate the queries. In this case, it can access other information stored in the database. We call this situation the SQL Injection vulnerability.
A successful SQL injection attack can result in unauthorized access to sensitive data, such as passwords, credit card details, or personal user information. In some cases, an attacker can obtain a persistent backdoor into an organization’s systems, leading to a long-term compromise that can go unnoticed for an extended period.
Error-Based SQLi
An error is received in response to submitted SQL queries. The attacker can also send new queries according to this error, or by manipulating the error, he can reach the information he wants to reach from within the output.
Union-Based SQLi
Multiple Select queries can be written using the Union operator. In this case, the attacker can write his own SELECT query with a union operator. But it should be noted that when the union expression is used, the number of columns must be equal to each other.
Boolean-Based SQLi
It does not return an error or requested information in response to submitted SQL queries. Instead, it gives a true or false answer. This makes the process very long.
Time-Based SQLi
It doesn’t return anything in response to submitted SQL queries. However, the attacker tries to see if the query works by adding functions such as sleep() to these SQL queries.
Out-of-Ban SQLi
None of the techniques described so far will work. The application’s response doesn’t depend on whether the query returns any data, on whether a database error occurs or on the time taken to execute the query. In this situation, it is often possible to exploit the blind SQL injection vulnerability by triggering out-of-band network interactions with a system that you control. These can be triggered conditionally, depending on an injected condition, to infer information one bit at a time. But more powerfully, data can be exfiltrated directly within the network interaction itself.
Various network protocols can be used for this purpose, but typically the most effective is DNS.
Warning
Take care when injecting the condition OR 1=1 into a SQL query. Although this may be harmless in the initial context you’re injecting into, it’s common for applications to use data from a single request in multiple different queries. If your condition reaches an UPDATE or DELETE statement, for example, this can result in an accidental loss of data.
SQL Injection Labs
- Web Security Academy - All Labs
- TryHackMe - SQL Injection Lab
- TryHackMe - OWASP Juice Shop
- TryHackMe - SQL Injection
- TryHackMe - Sqlmap
- TryHackMe - Game Zone
- TryHackMe - Poster
-
TryHackMe - Chill Hack - My Writeup

-
TryHackMe - Gallery - My Writeup

- TryHackMe - Avengers Blog
-
TryHackMe - The Marketplace - My Writeup

- TryHackMe - Wekor
- TryHackMe - Zeno
-
TryHackMe - SQHell - My Writeup

-
TryHackMe - Olympus - My Writeup

-
TryHackMe - Revenge - My Writeup

- TryHackMe - Metamorphosis
- TryHackMe - WWBuddy
- TryHackMe - Unstable Twin
-
TryHackMe - Daily Bugle - My Writeup

- TryHackMe - Year of the Dog
- TryHackMe - Year of the Pig
- TryHackMe - M4tr1x: Exit Denied
- PentesterLab - From SQL Injection to Shell
- PentesterLab - From SQL Injection to Shell: PostgreSQL Edition
- CTFLearn - Basic Injection
- CTFLearn - Inj3ction Time
SQL Injection Sources
- Web Security Academy - SQL injection
- TryHackMe - SQL Injection
- HackerRank - SQL
- OWASP - SQL Injection
- Niveet Palan - Handbook for SQL Injection
- Graham Zemel - Step by Step Guide to SQL Injection
- Raj Chandel’s Blog - Manual SQL Injection Exploitation Step by Step
- Atmanand Nagpure - A technique that a lot of SQL injection beginners don’t know
- goswamiijaya - Identifying & Exploiting SQL Injections: Manual & Automated
- daffainfo - SQL Injection
- Security Lit Limited - Definitive Guide to SQL Injection
- goswamiijaya - Exploiting Error Based SQL Injections & Bypassing Restrictions
- Lee Chun How - Out-of-Band (OOB) SQL Injection
- Mcry - First step to an SQL-Injection
- Secpy Community - SQL Injection: An Overview
- Frost - What is SQL Injection and How Does it Work
- Kontra Application Security - SQL Injection
- Start - SQL Injections
- CTFlearn - SQL Injection
- Imperva - What is SQL Injection
- Edward Low - Edward Low
- Sudarshan S - SQL INJECTION: IMPORTANT…
- Arth Detroja - SQL Injection
- A51F221B - Web penetration testing guide
- W3Schools - SQL Tutorial
- Codecademy - Learn SQL
- Programiz - Learn SQL: SQL Tutorial for Beginners
- TutorialsPoint - SQL Tutorial
- Cyber Security Roadmap
SQL Injection Cheat Sheets
- Web Security Academy - SQL Injection Cheat Sheet
- Ismail Tasdelen - SQL Injection Payload List
- NetSPI SQL Injection Wiki
- Pentestmonkey - Oracle SQL Injection Cheat Sheet
- Pentestmonkey - MySQL SQL Injection Cheat Sheet
- Pentestmonkey - Postgres SQL Injection Cheat Sheet
- Pentestmonkey - Informix SQL Injection Cheat Sheet
- Pentestmonkey - MSSQL Injection Cheat Sheet
- Pentestmonkey - DB2 SQL Injection Cheat Sheet
- Pentestmonkey - Ingres SQL Injection Cheat Sheet
- Codecademy - Preventing SQL Injection Attacks
- Exploiting hard filtered SQL Injections
- MS Access SQL Injection Cheat Sheet
- Yazılım Kodlama - SQL Sorguları ve SQL Sorgu Örnekleri
- Cheatography - Injection SQL Cheat Sheet by Neolex
- Cheatography - SQL CheatSheet Cheat Sheet by nimakarimian
- INVICTI - SQL Injection Cheat Sheet
- Deadly Hacker - List of google dorks for sql injection
- Perspective Risk - MySQL SQL Injection Practical Cheat Sheet
- MySQL Injection Cheat Sheet
I hope you liked my article. See you in my other articles![]()